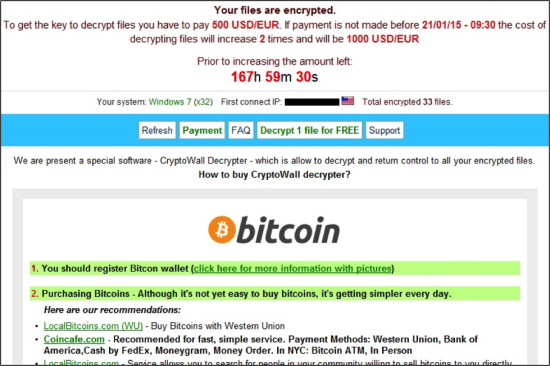
In response to the news that Imperva has issued a new report on CryptoWall 3.0, which has revealed that a small organised cybercrime ring behind CryptoWall 3.0 was able collect more than $330,607 in ransom from some 670 victims, Mark James, security specialist at ESET have the following comments on it.
[su_note note_color=”#ffffcc” text_color=”#00000″]Mark James, Security Specialist at IT Security Firm ESET :
“Cryptowall or indeed any ransomware malware poses a very real threat to many computer users because of the potential damage to files that so many still fail to backup. Considering this is something that is so simple to defend against, it is still so widely used and often successfully. The fact that it will adapt for the market area it is infecting shows that the malware writers do have an understanding of how important it is to tailor the ransom in an affordable way to ensure the biggest hit rate in gaining funds. If you have not backed up and your encrypted files are irreplaceable then your train of thought may well be along the lines of, can I afford to pay this to get my files back, they want you to pay so making it too expensive is counter-productive, but it still begs the question “why are you not backing up?” There are so many options for cheap easy backup procedures these days from USB or removable media that even a ransom of £50 could be more than you would spend on backup media. “[/su_note]
[su_box title=”About ESET” style=”noise” box_color=”#336588″] Since 1987, ESET® has been developing award-winning
Since 1987, ESET® has been developing award-winning
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.