We are starting to arrive at the conclusion that it is the people who make our organisations insecure – right? It is the people who are those assets who are protected by the firewall, and perimeter defences, yet these very same people-assets are usually the ones who allow some delinquent logical attack to gain the power and ability to circumvent such logical protection! And it is some of these people-assets who are the owners of the unpatched humanoid-operating-systems [HoS] – and as such these neurological empowered operatives are the very beings which can make wrong decisions, at the wrong time. However, the real inherent danger of the unpatched HoS is, it also has the ability to cover its own tracks, and hide its woeful actions.
Webinar By Duo Security: Securing Apps and Data in the Cloud and On-Premises (March 11, 2015 at 10 am PST / 1 pm EST)
OK, so recognising we have a problem with the ‘people-factor’ who are hosting the flawed O/S, we need to address it, and apply a patch in the form of Security Education and Awareness. But then we know this doesn’t always work either, as whilst you can take a horse to water, whilst you can’t make it drink, you can always drone it – neither of which are beneficial outcomes to the end cause. So, recognising that this conventional methodologies alone of delivering security education don’t always work, maybe we need to look elsewhere for a solution.
Next step is maybe look at the work carried out in 1908 and onward by Yerkes & Dodson with their Dancing Mice experiments, which proved that the use of a low-voltage electrical current, or the rewarding of the mice with milk soaked bread can change the behaviour of the subject rodents. However, whilst this approach based on the pain of inducement shock, or providing some form of gratification to the subject may well work with the homosapien, I am sure that it would not meet the blessing of the all-powerful Human Resources Department, let alone creating a potential for a group of miscreant users to become the new owners of curly hair; or others who have put on a few pounds into the bargain. Whilst I feel that this approach could serve up some interesting results, I am of the opinion that this won’t work either in modern day corporate world.
So, looking at the options, to patch our user, having considered the overt in-your-face style of the direct marketing approach to deliver Security Education may not work for all – and I fully appreciate that the idea of shocking the bad users, and feeding up the good carries a lot of adverse baggage, so there must be another way to tap into the and patch those resistant human.
One option which has been proven to work is that of the subliminal approach, leveraging the inquisitive nature of the human build, to encourage them to join a journey of learning and discovery with some magical manipulation of the brain. In fact it happens to most of us every day of our lives, but we just don’t see it! For instance, do you recall when Orange launched their services in the UK, which in that case ran short advert bursts which just introduced the word, and simple graphics, invoking an inquisitive thought process as to what this was all about.
In more recent times, my attention was caught by the simple advertisement being run by Honda – with the subliminal traits of quick-fire words being ran across the screen, emotive, aggressive red lettering, and images of cars at speed drifting over sand, and aircraft skimming the earth. In my case I noticed that whilst I found the early run of the advert uninteresting, I became very aware that I was starting to want to know what the advert was all about, and started to pay more attention to read what the words of what is actually a very simple advert – it tapped into my subconscious and created the need-to-know more – I became inquisitive!
Such advertisements as I have introduced above are not evolved by accident, but are born out of psychology, and the leverage of delivering both direct, and indirect communications to their viewing audience which attempt to tap into our emotional, and thinking state with subliminal undertones – and we all know it works. In particular with brands such as Apple who have built a considerable following based on tapping into the human surface of stylised exposure?
So the question is, just how we may leverage the subliminal message to conjoin with the conventional approach to delivering the Security Education and Awareness Programme. Here one tried, and proven methodology I have used is to apply a form of Reversed Social Engineering, and to create an unmentioned hook which is bated with a single payload. For instance, when running a security awareness programme, start the ball rolling by embedding the subtle subliminal message into the materials as they are introduced [but never mention them]. You will notice when this approach is first run, some may notice something, whilst others may think the presenter has made a mistake in preparation of the materials [please stay with me on this, we will get there I promise].
The second level of the subliminal plan is to follow up on the initial delivery with strategically placed posters in areas of high footfall – for example like the poster shown below.
Now whilst the poster itself may not be very exciting or interesting, it is carrying a hook, and it has been proven to start to draw the attention of some of the passers-by. The next level of the plan may be executed on the Corporate Intranet where we will again introduce the message, say this time on the Information Security page, again carrying the hooked-message to the end user public. For instance:
July 2015 sees the launch of the International Information Security Roadshow
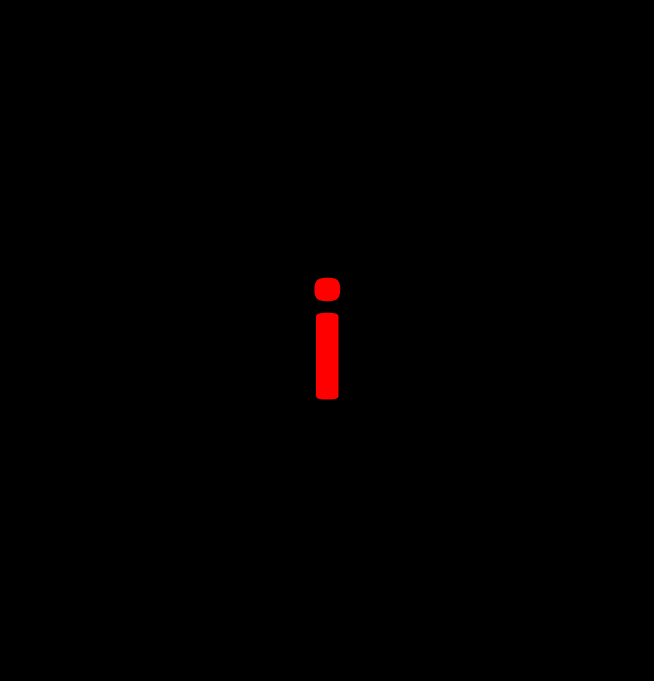
I am sure you can see that in the example I have shown the hook is based on what I refer to as NVP [Nero Visual Programming] with the Visual hook being played by the ‘i’. The eventual delivery of the subliminal associated message will be timed with some coordinated plan, which then reveals the association to the hook [‘i’] which in the case of this particular programme was ‘ignorance’ tied into a message that provides the readership with a takeaway – in this case:
ignorance of the threats posed by the Internet can harm your family
The final message carried by the ‘i’ may then be further associated with supporting materials and facts, such as the implications of Cyber Bullying, Trojans that Steal Banking Detail Scams, and other such nasty acts that can expose the end-user and their families to the criminal element of the Internet.
A further underpin to delivering the message will be to bone up on, and leverage some inbuilt techniques from the world of Neuro Linguistic Programming [NLP] where we may then augment the element of what I call NVP, with the language of security, further driving home the subliminal message with some well versed statements.
This approach is not by any means rocket science, but when used with the conventions of delivering the Corporate Security Education and Awareness Programme it has been proven to be a very high value add, by engaging those who may not normally pay any attention, by tinkering with their inquisitive nature – after all, nobody ever likes to be left out.
On my own part, I have already delivered this approach in multiple guises, and can confirm it to be an effective medium-to-long term methodology to underpin the security education lifecycle, which can, with very little effort generate beneficial outcome to the mission of caging behaviours – so just give it a try, after all, what have you got to lose?
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.