A new report by Recorded Future has found in the latest annual report “The Top 10 Vulnerabilities Used by Cyber-criminals”, criminal exploit kits and phishing campaigns favoured Microsoft products in 2017, with seven of the top 10 vulnerabilities exploited by phishing attacks and exploit kits utilising Microsoft products.
Javvad Malik, Security Advocate at AlienVault:
 From OTX, we observed similar trends with Microsoft Windows and Office being the most popular to exploit. Microsoft have exceptionally mature processes to prevent exploits. However, due to their software’s ubiquity, once an exploit does slip through and is discovered, it is used heavily.
From OTX, we observed similar trends with Microsoft Windows and Office being the most popular to exploit. Microsoft have exceptionally mature processes to prevent exploits. However, due to their software’s ubiquity, once an exploit does slip through and is discovered, it is used heavily.
The below table shows exploits in order of the number of times they have been referenced in vendor reports on OTX. (taken from a dataset of approximately 80 vendor reports from 2017).
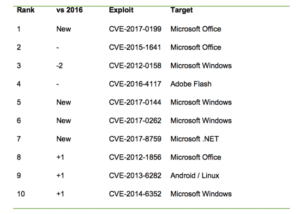
CVE-2012-0158 comes in as the third most referenced vulnerability. Sophos described the exploit as “arguably one of the most exploited vulnerabilities of the last decade” – and it continues to be extremely popular despite being 5 years old. This isn’t a new phenomenon. Kaspersky reported that the Stuxnet vulnerability CVE-2010-2568 from 2010 was the exploit most seen by their users in 2015.
To protect against vulnerabilities being exploited, enterprises need to understand which vulnerabilities are the most important to patch quickly, and which ones are being actively exploited in the wild. Using this information, enterprises should prioritise which systems to patch, and what to look out for in threat detection controls. Using a product like Open Threat Exchange (OTX) can help enterprises answer both these questions and protect themselves better.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



