In August 2014, the US-based Institute of Internal Auditors Research Foundation published (together with ISACA at their 2014 GRC joint conference) a research report focused on what the Board of Directors needs to ask in relation to Cyber Security.
As approach the 2015 GRC Conference – to be held in Phoenix, AZ on 17-19 August – J.C. Gaillard of Corix Partners offers his views on the 2014 report, and his own take on the key questions the Board of Directors should consider around Cyber Security.
Deconstructing the 2014 report
At high level, the 2014 report is still very relevant and compelling. It endorses, without ambiguity, the need for the Board to be involved on Cyber Security matters – and the importance of looking beyond traditional IT issues. It also offers clear and sound principles to guide the Board’s involvement as well as reiterating the key relevance of the CISO reporting structure and the positioning of Security in the second line of defence.
Those are fundamental aspects on which Corix Partners has repeatedly commented in the past, and on which we are broadly in agreement with the authors.
But, looking into the details of the report, there are 4 concerning aspects which overall do some damage to its authority:
- As a UK based consultancy, we find the approach to privacy matters to be very US-centric. This is only a minor criticism and an idiosyncrasy, as the topic is otherwise well covered and its concepts can easily be translated to a different context
- More serious is the reliance of the report on IT examples and references, having stated categorically upfront that Cyber Security cannot be “relegated” to the IT department or treated “just as an IT issue”
- The report also falls into the language trap of referring to Cyber Security as a “risk”. This is a dangerous and simplistic shortcut we have highlighted several times in the past
- Our main criticism revolves around the questions the report suggests the Board should ask. While they broadly cover the right topics, in our opinion, they are often too specific and overall lack a clear and logical structure
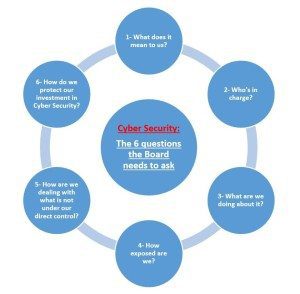
We offer below our own groupings, forming 6 questions around the concepts which an organisation’s Board of Directors should be concerned about when it comes to Cyber Security. In many cases, we simply repeat, redistribute or expand upon the ideas put forward in 2014 by the IIA, but at the same time, we have tried to structure those into a coherent framework.
Fundamentally, we believe that the Board of Directors should not approach Cyber Security purely from a Risk perspective. Risk is ultimately about “things that may or may not happen”. When it comes to Cyber Security, the Board should start from the premise that this is a matter of “when”, not “if” – and should shift the focus towards understanding and managing what is actually getting done to protect the organisation.
In the end, it may come down to a more traditional risk discussion – and it may make sense to embed Cyber Risk into a broader enterprise-wide risk model. However, this should only be as a by-product of a sound examination of the protection measures in place to protect the business from those very real and active Cyber Threats.
The Board must not be allowed to believe that it needs to be involved simply because the Cyber Security topic is making headline news. The topic is making headline news because security breaches are occurring more and more often. This, in turn, is due to decades of complacency, neglect or short-termist “tick-in-the-box” practices around the Information and IT Security space. It is this attitude which has resulted in the low maturity and protection levels, such as those recently highlighted by the RSA Cyber Poverty Index survey.
In large organisations exhibiting such low levels of Cyber Security maturity, it would be misleading to allow the Board of Directors to believe it’s a simple problem to fix – or that it simply requires the Board’s supervision around a handful of key aspects. It is also misleading to allow the Board to believe in ready-made technical solutions or that throwing money at the problem will solve everything, as McKinsey & Co have recently highlighted in an article that echoes their 2014 findings for the World Economic Forum.
“Cyber Security is a high-stakes topic, so it is a CEO-level one”, states the McKinsey article. However, the problem has some depth – and in most large organisations, where Cyber Security maturity levels are low, it will be rooted in 10 to 15 years of failure. This is the true problem which many organisations’ Boards of Directors need to confront and address.
The real questions the Board of Directors needs to ask
- What does it mean to us?
First of all, the Board must form an understanding of the nature of the Cyber Threats that might target the firm.
Cyber Threats do not target all organisations in the same way – and some industry sectors are more exposed than others. Cyber Security results from the application of proportionate controls to protect the business against the Cyber Threats it faces.
Understanding those Threats is key to success and approaching the problem from a generic “one-size-fits-all” angle – or simply based on the content of media coverage – is dangerous and can lead to misguided judgements.
The Board should seek internal or external advice as required on this matter, until these basic building blocks are in position.
It is also key for the Board to realise that many of the Cyber Security topics hitting the headlines today result from the absence of basic IT Security controls – despite these having been known and well mapped out for the best part of the last 10 to 15 years (as highlighted by the UK GCHQ back in 2013).
Understanding the IT and Information Security history of the firm could help position what needs to be done next. If Cyber Security maturity is deemed to be low, understanding where the roadblocks are that have prevented progress in the past should be essential to avoid repeating mistakes.
- Who’s in charge?
Having established its own understanding of the concepts, the first concern of the Board should be to ensure that Cyber Security responsibilities are clearly and unambiguously distributed across the organisation.
Cyber Security should be formally part of the portfolio of a Board member, and accountability cascaded down (directly or indirectly) to an individual specifically tasked to make sure the business is, and remains, protected from Cyber Threats. This responsibility would lie with the CISO in most large organisations.
The reporting line of the CISO should be clear – and at a level allowing visibility, credibility and accountability across the organisation. The actual reporting line itself should be dictated by the priorities of the organisation, ahead of arbitrary separation of duties considerations.
The repartition of roles across the various lines of defence and across corporate silos should be clear. A sound Security Governance Framework and Target Operating Model should document those aspects across IT and beyond – into HR, Procurement, Legal, Corporate Communications and business units. They should cover, without complacency, the true geographical perimeter of the organisation and its dependency on third-parties where relevant.
- What are we doing about it?
Having established that a sound Security Governance platform is in place across the business, the Board should ensure that key protective measures are (and remain) in place.
Starting with a sound appreciation of the Threats the business faces (both internally and externally), a determination of the Controls required to protect the business against such Threats should naturally follow. These should be consolidated in a Cyber Security controls framework, specifically tailored to each organisation.
Relying on recognised generic industry frameworks and good practice catalogues instead is often preferred (or recommended, as in the IIA report), but the approach has its pros and cons. On one hand, it is a sound way of making sure that all angles are covered; on the other, it could easily lead to over-engineering and over-spending – particularly for smaller firms.
Fundamentally, the Board should ensure that Controls are proportionate to the Threats the business faces – otherwise their deployment could be challenged or costs may escalate. The Board must look beyond which framework is actually being used, to focus on the way the controls it contains are effectively implemented across the organisation. Once again, it should also take into account the organisation’s true geographical perimeter and its dependency on third-parties where relevant.
- How exposed are we?
The Board should ask for periodic reports showing adherence of the organisation to its Cyber Security controls framework, and the primary focus should be on any deviations from this. Such deviations create opportunities for Threats to target the business and cause harm, creating “risk” – in the most classical sense of the word.
The Board should be concerned with any main issues – whether they’re financial, organisational or technical – which are preventing the implementation of the Cyber Security controls framework, ensuring they remain updated on what is being done to address these.
The Key Threats should be those to which the firm is the most vulnerable (i.e. those against which it is the least protected). Once the Key Threats are identified, the Board should ensure that their organisation’s Incident Response Capability is regularly tested in those areas – if relevant.
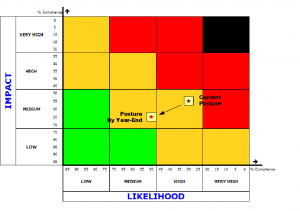
The overall Cyber Risk Posture of the organisation should result from the analysis of deviations from an established Cyber Security controls framework. This should be tracked year-on-year on a risk matrix as more controls are implemented, preferably as part of an agreed Strategic Security Roadmap – or otherwise as a result of various tactical projects.
- How are we dealing with what is not under our direct control?
The Board should be concerned with 2 very different aspects in that space:
- Dependency on Third-parties: The Board should be acutely concerned about dependency on third-parties, across the business and IT, as we have highlighted several times above. Many controls in the Cyber Security controls framework will have to be cascaded down to (and implemented by) a variety of external firms, but the organisation may have no actual means to enforce those – even if a breach in the other party environment could cause catastrophic damage to the business. As such, effective vendor risk management could be of critical importance for some organisations.
The Board should start by building an understanding of the diversity and numbers of such vendors, and of those on which the business is most dependent. This must not be seen as a mere IT issue and it is key to approach it in terms of business processes.
Following this, the Board should build an overview of those vendors’ levels of adherence to the Cyber Security controls framework – or where relevant, of their unwillingness to cooperate with Cyber Security assessment efforts.
Finally, the Board should ensure that unsatisfactory outcomes are being addressed – ensuring they remain updated on these matters. Board members also sitting on the Boards of some of the offending third-parties may want to take the matter into their own hands if and where they can.
Again, it is key to ensure that this is not turned into an IT matter – and that all business relationships are in scope.
- Media & Political Interest: The Board should also be acutely concerned with the outcome of a Cyber Security breach spilling over into surrounding corporate areas – potentially contaminating their brand, customer trust, or shareholders’ confidence.
The dynamics of recent cases show that contamination often occurs as a result of aggressive media and political interest following breaches of privacy or service disruptions affecting the general public.
While it is difficult to predict where media attention will be in relation to any particular service incident, the Board can build an understanding of the amount of sensitive personal data the organisation stores and processes. The Board should ensure it possesses a clear understanding of its legal duty of protection towards the privacy of its organisation’s customers and staff – as well as the measures that are in place (or not) as part of the Cyber Security controls framework. The Board of international organisations should also be aware that those obligations may vary from country to country.
In all cases, the Board should ensure that the Security Governance Framework is active across all relevant corporate silos and reaches into all areas that may be involved in case of a breach – and that those interactions are regularly tested.
- How do we protect our investment in Cyber Security?
The Board should be aware that Cyber Threats evolve constantly and that there is no silver bullet solution, technical or otherwise.
Ongoing protection can only come from a strong controls culture, embedded in the way the firm works. Such cultural shift could take time, particularly in organisations where Cyber Security maturity is low to start with, so taking a long-term view and sticking to it is key to success.
Ensuring that key personnel (the CISO and their team in most large organisations) remain in charge over the period is also key, and means they may have to consider their tenure over a 5 to 7 years horizon in many cases. Changing approach every 2 to 3 years every time a new CISO comes is a recipe for disaster and could be very simply why so many large organisations still show such a low level of Cyber Security maturity.
The Board should also ensure that its direct involvement in Cyber Security matters is clear, unambiguous and widely publicised across the enterprise. The Cyber Security message from the Board should in turn be cascaded down across the organisation through regular management channels, and it is key for the staff to see that management (at their level) takes Cyber Security at heart. This type of bond is generally stronger, longer-lasting and cheaper to establish than any type of engagement through awareness development campaigns – which often miss the point entirely by being too tactical or too technical.
Finally, having examined all aspects listed above, the Board should consider the current level of Cyber Risk Insurance protection the firm holds (if any), and whether it provides adequate cover.
The Insurance question should come last, and the Board should consider adjusting cover if possible to match the findings highlighted by previous questions. The Cyber Risk Insurance market is evolving fast, and products may be available today that were not available last time the Board inquired.[su_box title=”About JC Gaillard” style=”noise” box_color=”#336588″] A senior executive with over 20 years of experience developed in several global financial institutions in the UK and continental Europe, gaining exposure to all layers of management up to board level. Jean-Christophe (JC) was the Chief Security Officer at Rabobank International from 2000 to 2009. Prior to that, he held a number of IT Management positions within the Paribas/BNP-Paribas organisation between 1991 and 2000. A French national permanently established in the UK since 1993, he holds an Engineering Degree from Telecom Paris Tech.[/su_box]
A senior executive with over 20 years of experience developed in several global financial institutions in the UK and continental Europe, gaining exposure to all layers of management up to board level. Jean-Christophe (JC) was the Chief Security Officer at Rabobank International from 2000 to 2009. Prior to that, he held a number of IT Management positions within the Paribas/BNP-Paribas organisation between 1991 and 2000. A French national permanently established in the UK since 1993, he holds an Engineering Degree from Telecom Paris Tech.[/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.