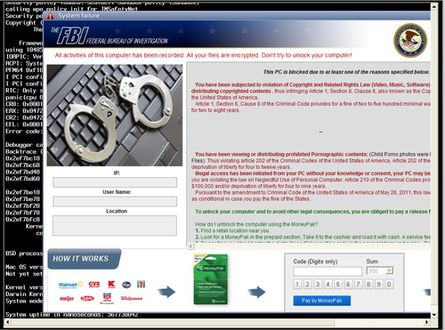
A persistent, widespread malware campaign that utilizes compromised Apache servers is locking users’ computers and demanding a fee of US$300 to free their data.
Researchers from Eset wrote that the ransomware scam is an extension of a long-running attack that compromises the infrastructure of web hosting companies with a variant of a malicious Apache module called “Darkleech.”
“Malicious modification of server binaries seems to be a very popular trend for malware distribution,” wrote Sebastien Duquette, an Eset malware researcher, on a company blog.
Eset also suspects that hackers also may have figured out how to compromise CPanel and Plesk, which are both software programs used by hosting companies to manage their networks and websites.
Darkleech tampers with websites hosted on an Apache server. It loads an iframe into a web page and redirects a victim to a malicious URL that hosts the Blackhole exploit kit, Duquette wrote. Eset detected at least 270 websites that redirected victims this way in the last week.
SOURCE: computerworld.com.au