Last July, Damballa’s Threat Discovery Center discussed the infamous web forum, Darkode, that was supposed to be resuscitated by sp3cial1st. Since then, we’ve been monitoring the dark web to see if a new Darkode forum would show up and we discovered the new Darkode Reloaded. It has resurfaced.
As promised, the administrators moved the forum to the dark web for “security” reasons and anonymity. Security and anonymity of a criminal forum is only as good as the forum administrator. It’s all a “trompe-l’œil” (illusion). See for yourself, the search page of the forum was wide open to anyone without being logged in.
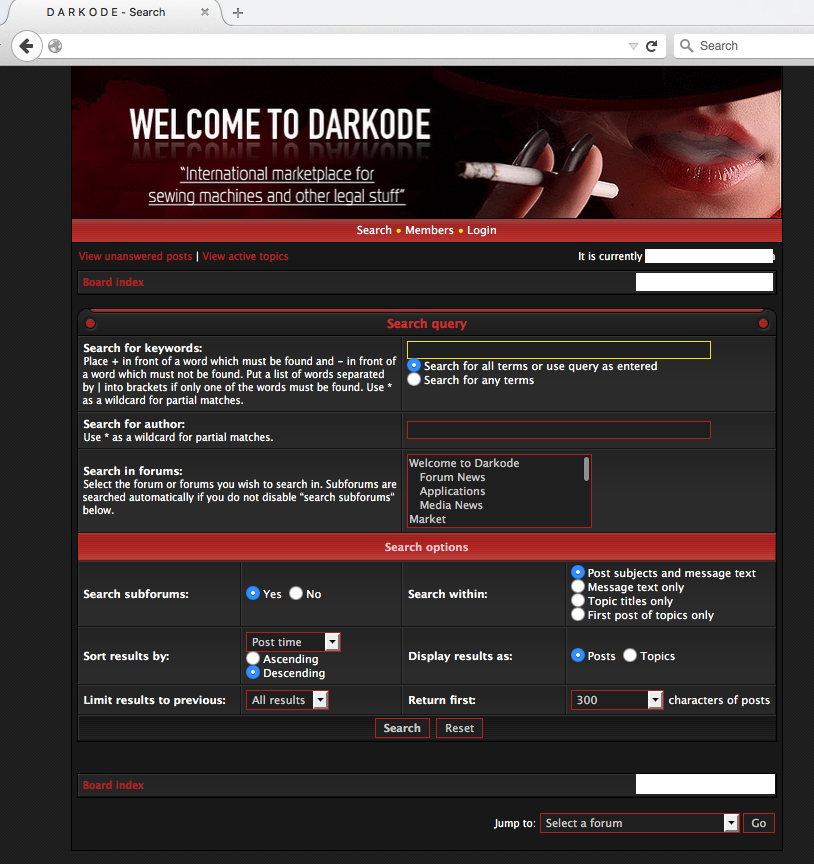 From the search page, the forum was completely accessible. The member list, the active topics, you name it. The member list link revealed the whole list of members.
From the search page, the forum was completely accessible. The member list, the active topics, you name it. The member list link revealed the whole list of members.
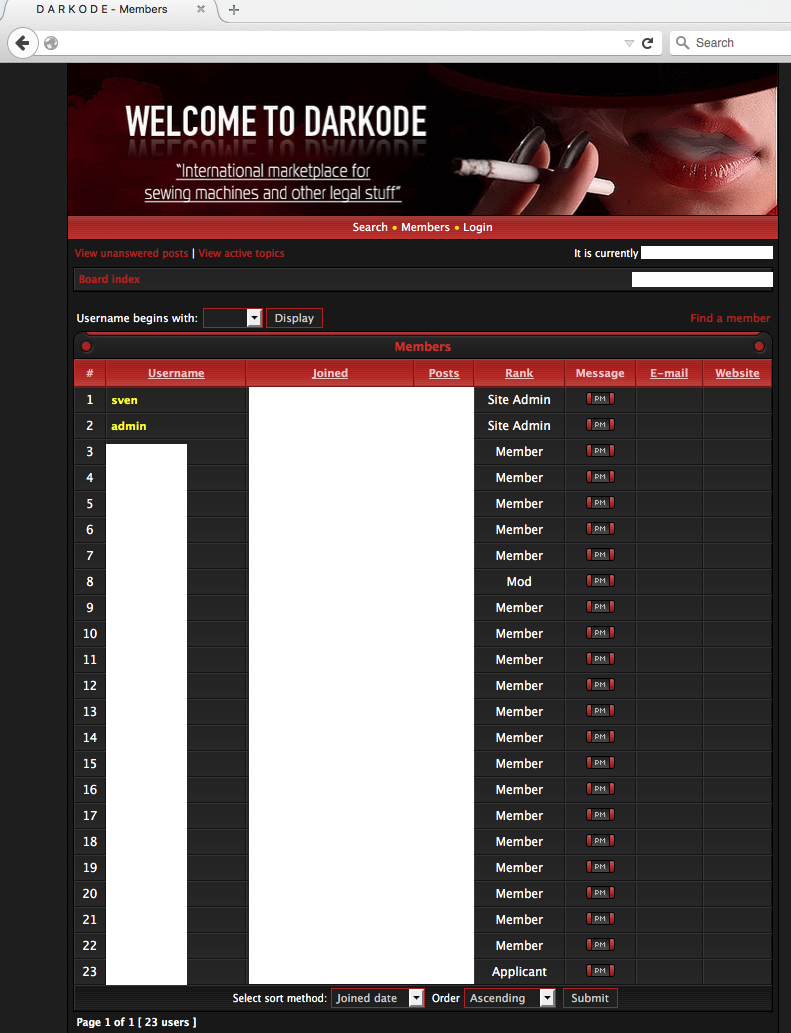 The forum administrator Sven is a very generic handle but we know that he’s a previous member of Darkode. As for the rest of the members, there is a mix of HackForum members usually called HF skids and DamageLab members. This gives you an idea about the quality of the forum.
The forum administrator Sven is a very generic handle but we know that he’s a previous member of Darkode. As for the rest of the members, there is a mix of HackForum members usually called HF skids and DamageLab members. This gives you an idea about the quality of the forum.
In terms of security, the forum is also accessible without the Tor software. It can be accessed from any browser without anonymity. Another poor design of the forum.
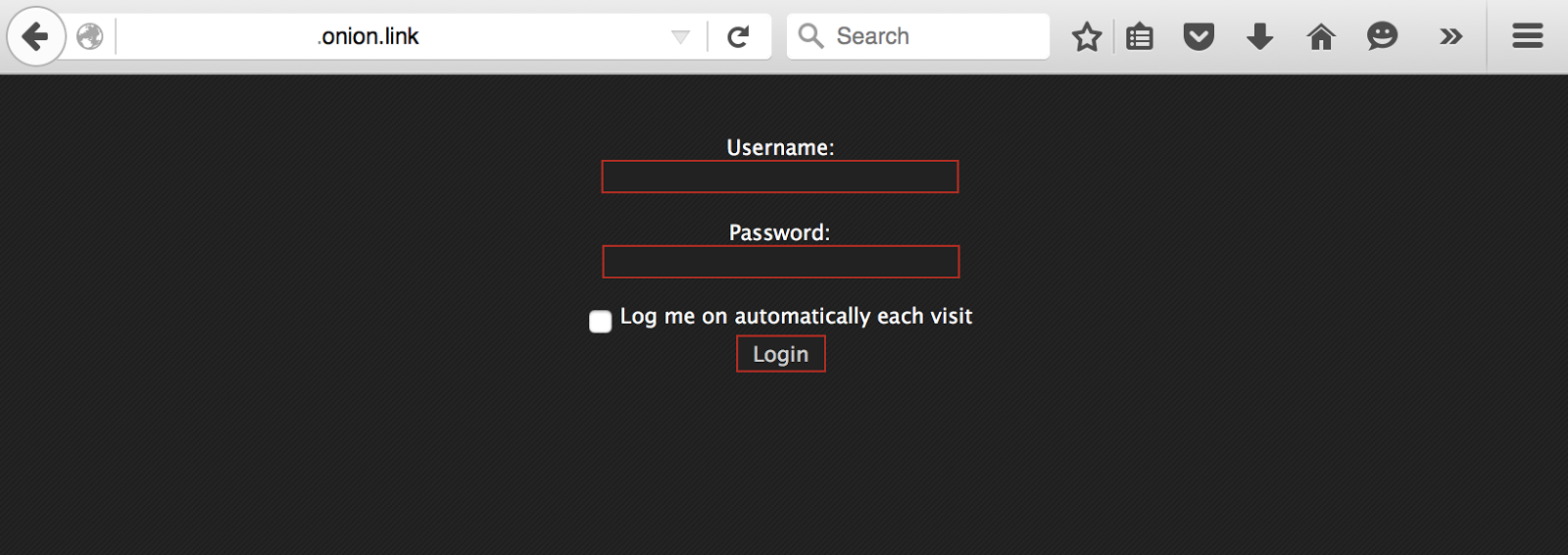 Darkode Jabber Service
Darkode Jabber Service
Sven, the administrator of Darkode, offers a Jabber service to its members. The jabber server runs on the domain darkode.club and is hosted on a dedicated server at 86.105.227[.]13 located in Russia.
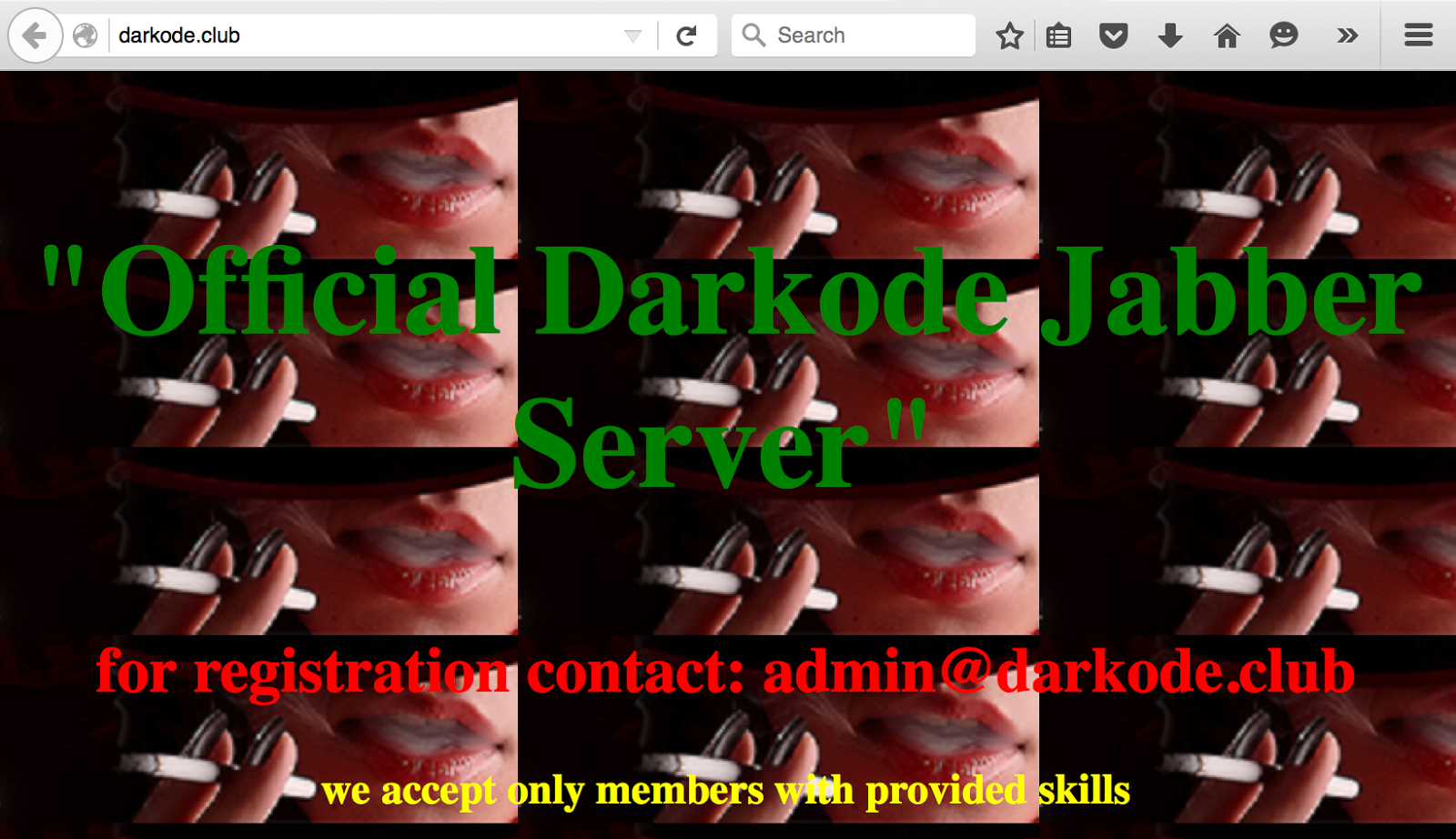 The server is poorly configured. We know that this server runs a software called Jetty 9.2 Snapshot. This software comes along with Openfire. Openfire is a Jabber server software and the version 3.10.2 is installed.
The server is poorly configured. We know that this server runs a software called Jetty 9.2 Snapshot. This software comes along with Openfire. Openfire is a Jabber server software and the version 3.10.2 is installed.
The Jetty software listens on port 7070 by default and this port is wide open on the server:
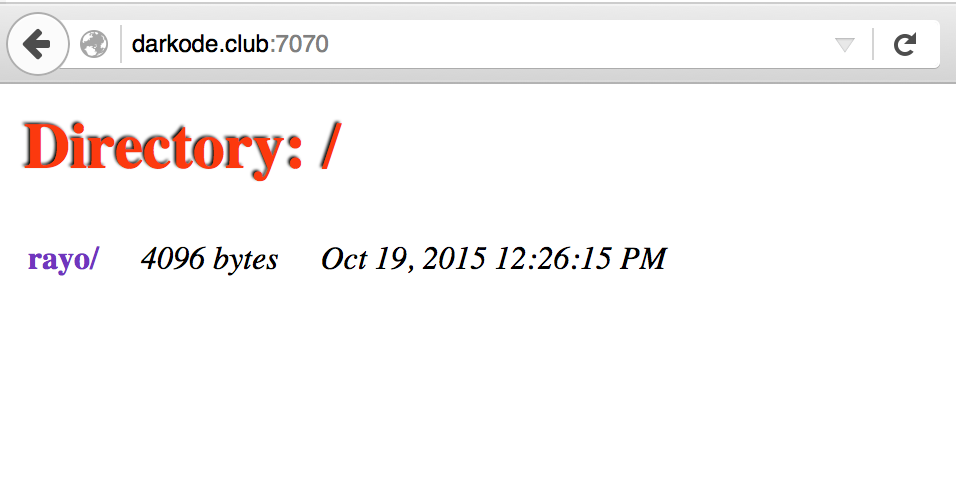 The administration interface for the jabber server is also accessible with the default configuration port 9090.
The administration interface for the jabber server is also accessible with the default configuration port 9090.
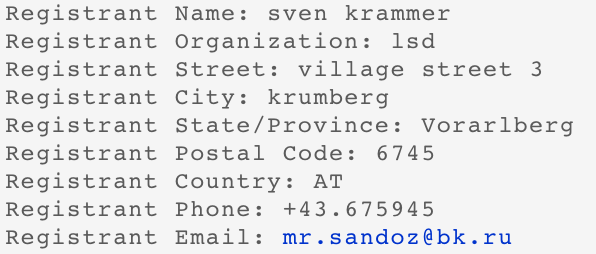
 The email address and name used to register the domain darkode.club are:
The email address and name used to register the domain darkode.club are:
The server has the following ports open:
- 22 – SSH
- 25 – SMTP
- 80 – HTTP
- 5222 – Openfire
- 5223 – Openfire
- 5229 – Openfire
- 5269 – Openfire
- 7070 – Jetty Snapshot
- 9090 – Openfire Administration interface
On top of access control issues with the forum, the software also has vulnerability issues. The Openfire version installed 3.10.2 is subject to several reported vulnerabilities, you can find a complete list HERE.
Forum activity
From the posts we reviewed, no significant activity stood out. It felt like a bad Darkode imitation with rigorous rules. There was no discussion of banking trojans or similar high profile malware.
The criminal community has low trust in the ‘new’ Darkode forum. The lack of security and misconfiguration shows that Darkode can’t be trusted and will never regain its former glory. Another Darkode fail. In previous times, we’d provide the link, but this time we aren’t because it’s just not worth anyone’s time.
[su_box title=”About Damballa” style=”noise” box_color=”#336588″] As a leader in automated breach defence, Damballa delivers advanced threat protection and containment for active threats that bypass all security prevention layers. Born for breach defence, Damballa rapidly discovers infections with certainty, pinpointing the compromised devices that represent the highest risk to a business, and enabling prioritized response and refocusing of security experts to the areas of greatest risk to an enterprise. Our patented solutions leverage Big Data from one-third of the worlds Internet traffic, combined with machine learning, to automatically discover and terminate criminal activity, stop data theft, minimize business disruption, and reduce the time to response and remediation. Damballa protects any device or OS including PCs, Macs, Unix, iOS, Android, and embedded systems. Damballa protects more than 400 million endpoints globally at enterprises in every major market and for the world’s largest ISP and telecommunications providers.[/su_box]
As a leader in automated breach defence, Damballa delivers advanced threat protection and containment for active threats that bypass all security prevention layers. Born for breach defence, Damballa rapidly discovers infections with certainty, pinpointing the compromised devices that represent the highest risk to a business, and enabling prioritized response and refocusing of security experts to the areas of greatest risk to an enterprise. Our patented solutions leverage Big Data from one-third of the worlds Internet traffic, combined with machine learning, to automatically discover and terminate criminal activity, stop data theft, minimize business disruption, and reduce the time to response and remediation. Damballa protects any device or OS including PCs, Macs, Unix, iOS, Android, and embedded systems. Damballa protects more than 400 million endpoints globally at enterprises in every major market and for the world’s largest ISP and telecommunications providers.[/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



