I’m sure very few of you knew that Dell is in the security business. Well we are, in fact at approximately 1B in revenue per annum, it is one of our fastest growth areas in the company. In order to help people understand what we do, and how we are thinking about security, a few weeks ago, Dell proudly introduced our CONNECTED SECURITY vision and strategy to the world. We did so to ensure that we are adding value to our customers key imperatives around protecting their valuable data.
Today’s mega-trends ─ Cloud, BYOD/mobility, Social and big data ─ each introduce exciting opportunities for businesses to be disruptive and change the competitive playing field however also bring about a magnitude of new threats and vulnerabilities. The new challenges these threats create for the IT environment such as insufficient visibility, unconnected information and silo’d security tools and processes, as well as compliance requirements and new reporting ─ all must be managed with limited resources. So net/net, bigger risks, more controls, but the same or less money to manage them with, urrrggh!
Dell’s Point of View:
At Dell we believe “security done in silo’s is dangerous and expensive”. This is a very strong position to take, but the time has come for a new approach. Unlike days past, company data can be anywhere (on-prem, virtualized and in the Cloud) and users can access it at anytime, anywhere on any device. The only true line of defense for this complex and connected world is a comprehensive set of predictive, context-aware, connected security solutions that break down silos and protect data from end-point, to datacenter to cloud. Dell’s Connected Security vision and strategy provides such a dynamic solution portfolio, and as we evolve it we will give our customers MORE power to solve today’s biggest security and compliance challenges, while helping them better prepare for tomorrow.
Proof’s in the Pudding: Connected Security vision and strategy; what we announced:
• Five new and updated solutions which provide immediate value in protecting the organization, dramatically reducing business risk
• Support for CONNECTED USERS: re. BYOD, cloud, network security and compliance needs
• Comprehensive and integrated Connected Security solutions; aimed at providing seamless protection of data from the endpoint to the datacenter to the cloud
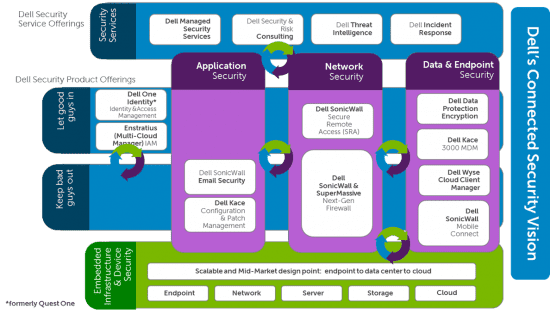
In addition to all of the solutions outlined in the Connected Security grid diagram, there are FIVE new or updated products here’s what we have brought to the market in support of this vision:
• Dell™ One Identity Cloud Access Manager (note name change from: Quest Identity One to Dell Identity One)
• Dell™ SonicWALL NSA 2600 next generation firewall,
• Dell™ SonicWALL™ E-Class Secure Remote Access (SRA) for enterprise appliance + Dell SonicWall Mobile Connect
• Dell™ ChangeAuditor 6.0, and
• Dell™ InTrust™ 10.7
All 5 of these solutions provide new levels of protection in and of themselves, and additionally will start working collectively to gather, analyze, report and act in a proactive way when managing security threats, versus acting independently in silo’s, as most of our competitors’ point solutions do. The interesting thing that should be noted, when looking at the Connected Security vision diagram above, is that the Dell Identity and Access Management solutions are important “glue or binding” that help weave and add a lot of context about users and business policies to our other security solutions, relative to who is doing what, or who is allowed to do what on the network; from an endpoint device and with which data/applications. In other words keeping the bad guys out and keeping the good guys good (and productive).
So needless to say, Identity & Access Management (“IAM”) is a great starting point on any security journey given the latest statistics indicates that 70% of all security threats start from within! I imagine that number has gone up significantly with the surge of “bring your own…” and data moving around via smartphones and tablets, whether intentionally or by accident. In addition to internal threats, the watchful eye of auditors gets more intense with every passing day, and auditors want to know exactly who has access rights to what! In fact, that’s exactly what happened with one of the municipalities here in Texas, in June of this year after the news reported an incident where 5,000 employees personal information was compromised when a payroll files was inappropriately accessed by a user that had not been de-provisioned as they transitioned into a new role. Now this City is busily implementing access controls and governance tracking to show the auditors that they are compliant.
But back to Connected Security. When Dell says “Connected Security”, the question that jumps out is: So how do you “connect” security Dell?
• Dell Connects Security by embedding security right into the infrastructure, endpoint devices and even the Clouds we build and deliver to clients.
• Dell Connects Security by connecting the Information coming from our different solutions, for example: threat alerts from our 1 million+ SonicWall Firewalls around the globe and our SecureWorks command center, that is now being leveraged together to provide our customers with predictability and the ability to address threats before they become a problem.
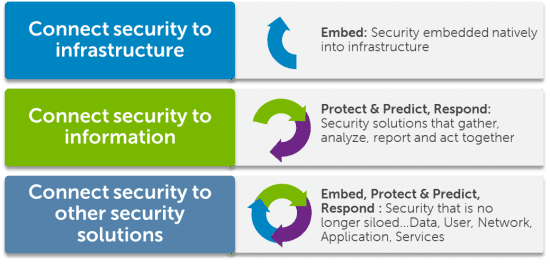
Dell Connects our security solutions to each other so each solution is “CONTEXT AWARE” and policy based management can be enforced. For example,
– Identity Aware Firewalls: a contractor traversing the network to an unauthorized country can be detected by SonicWall and dealt with by IAM. If an IAM policy is breached, IAM can de-provision the contractor’s access rights entirely, until the situation is analyzed and rectified.
– Encryption Aware Firewalls: the ability for our Next-Gen Firewalls integrating with our device encryption solutions to ensure data on devices is in fact encrypted, if not, a rule can be invoked to encrypt the data on the device, quickly.
When you connect Dell IAM, Firewalls, SecureWorks (security managed services) and Dell Data Protection/Encryption on devices, together, they protect data wherever it resides and protect it better than security done independently in silos ─ on the network, in the cloud, or on mobile devices ─ so net/net: Dell delivers Connected Security through solutions that provide embedded, predictive and context-aware security to protect and detect against unseen threats.
John McClurg our Chief Security Officer at Dell had this to say about these Power-House Security announcements:
“In an age of increasing risk, the security industry is facing the need to dramatically change its approach to protecting organizations of all sizes across all industries, at all times. Dell is at the forefront of this shift. Our vision for Connected Security ─ a holistic, context-aware and connected approach to security that spans from endpoint to datacenter to cloud ─ is the driving force behind these collaborative, performance-focused security solutions. The new solutions announced today further expand our Connected Security portfolio, providing CSOs like myself with the business intelligence, contextual richness and tools we need to mitigate risks and become business enablers.”
This is an enormous amount of security innovation going on at Dell, and we are proud of our vision for better security i.e. “ Connected Security” and moreover pleased with the enormous progress we have made in helping customers address their toughest security challenges.
For more information click here:
Joanne Moretti | | | @joannmoretti
 Joanne Moretti joined Dell in 2012 as VP & Global Head of Software Marketing reporting to John Swainson the President of the newly formed Dell Software Group. She directly enables Dell’s transformation from a product company to an E2E solution provider by integrating the recently acquired software marketing organizations into Dell and developing GTM strategies and compelling value propositions for organizations looking to accelerate their results through mobile, cloud and big data technologies in a secure and simplified way.
Joanne Moretti joined Dell in 2012 as VP & Global Head of Software Marketing reporting to John Swainson the President of the newly formed Dell Software Group. She directly enables Dell’s transformation from a product company to an E2E solution provider by integrating the recently acquired software marketing organizations into Dell and developing GTM strategies and compelling value propositions for organizations looking to accelerate their results through mobile, cloud and big data technologies in a secure and simplified way.
Before joining Dell, Joanne led Hewlett Packard’s sales force transformation by designing, developing and delivering the HP Sales Excellence program including the award winning HP Sales University.
Prior to HP, Joanne was SVP, WW Product Marketing & Analyst Relations at CA, Inc. There she and her team delivered GTM strategies, messaging & content for CA. While in this role she received the coveted Executive Women’s Forum: Most Influential Woman in IT Security Award-solution provider category.
Prior to her marketing career Joanne led sales teams, and was GM and SVP for two of CA’s largest businesses from 2004-2007: CA Canada and the US West.
Prior to that, Joanne spent 16 years in sales, sales management and technical engineering roles.
– Joanne spent the first 7 years of her career in IT Security and Data Center Operations at CIBC Bank in Toronto Canada,
– Joanne supports women in IT throughout North America by participating in WITI, the EWF, Anita Borg Institute and internally in Dell’s WISE organization.
– Joanne graduated from Control Data Institute in Toronto with honors in Computer programming and engineering, and currently resides in the Dallas Fort-Worth area.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



