At a recent security and risk management conference, I had an opportunity to talk with industry analysts about today’s challenges in network security. It seems that many analysts’ perspectives are driven by client inquiries that seek simple product recommendations to solve complex challenges. A recurring problem with this sort of inquiry is that oftentimes the right solution requires more than the purchase of a product. Solutions to complex problems often also require organizational changes – yet this critical element is either ignored or impossible to implement based on the level of the individual making the inquiry.
Featured Download: Social media access at work. Do your employees know the rules?
With that in mind, my conversations with some analysts focused on common misconceptions about the value of perimeter security, next generation firewalls, and other cure-alls that are being purchased with the mistaken goal of providing an impenetrable wall around a company’s IT infrastructure. The latest buzzword spouted by many analysts (and commonly misunderstood) is technology that provides “detect and respond” capabilities.
The dirty secret I raised with those analysts is that this latest “silver bullet” technology is no cure-all and in many cases provides little added value to customers beyond the previous generation of perimeter security. And yet these technologies do seem to provide political cover against almost inevitable data loss, since they’re currently the analysts’ recommended solution for perimeter protection.
Intrusions and Kill Chains
For the record, I am not saying that firewalls and other perimeter protection have no value. Perimeter protection is getting better every year and remains an excellent investment. The problem is that many customers do not fully understand how cyber-attacks work and so might expect that perimeter protection alone can protect their networks. Why not? They’ve paid more than enough money, and a salesperson probably told them it was sufficient.
An IT security professional will tell you that almost any competent attacker can walk through the best and latest perimeter protection, infecting an entire network within minutes. Today it’s almost certain that infected content will make its way through corporate email servers, or users’ machines will get infected via employees opening personal web email at work.
In many cases, your perimeter protection can detect these infections after a period of time – say, 15 minutes to 2 days. Unfortunately, this detect-and-respond chain also generates a lot of false positives and requires full-time (24/7) trained staff to analyze the alerts and determine the appropriate action. If there are too few competent people monitoring these mechanisms, an intruder’s access will only persist and expand. To understand the scope of this problem, keep in mind today’s breach reports often tell us that intruders have had undetected access for more than 200 days.
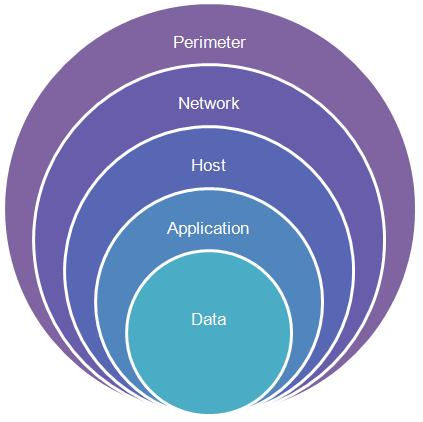
Defense in Depth
Given that intruders can easily get past the detect and respond protections, what are the best practices to protect your corporate network?
Let’s start with the assumption that your perimeter defenses will fail some of the time. Next, you have to do a pragmatic analysis of how far an intruder could go after taking control of any one machine in your environment. Here is what you should expect: the compromised machine has a key logger installed that records every user name and password entered on the machine. Assume that any administrator account credentials that ever touch the compromised machine are now available for the attacker to access other systems. And if the compromised machine has user certificates, server certificates, or SSH keys, these are also now owned by the attacker for their use.
To evolve to a defense-in-depth strategy, you have to look at each potentially compromised machine and ask yourself how to limit the value of the stolen credentials. Also, how do you limit the machine’s ability to access other systems given that it’s been compromised, but no one may know it? The goal is to stop lateral motion on your network by an intruder and to minimize the damage.
To help you solve the compromised credentials issue, here are some suggestions:
– Make sure that every credential on every machine is unique (so that each root and administrator account has a different password on every machine).
– Avoid using domain administrator credentials to connect to systems, and if they must be used in an emergency, change the password immediately after access.
– Consider creating multiple domains with different security policies and appropriate trust models in each. This way, a compromised domain account in sales won’t allow unrestricted access to systems in development or HR (for example).
– Never allow users to be members of the local administrators group on their machines, as this enables easy exfiltration of password hashes by an intruder.
– Never allow SSH keys to be stored on a local user’s machine; instead a bastion host should hold the private keys in a secure local storage mechanism that cannot be accessed by a user or an intruder.
– Add jump servers/bastion servers/VPNs and gateways within your interior network that require additional authentication to get to different internal networks.
– Never store server certificates on a local machine; instead store them in an encrypted file repository on a central server that requires multi-factor authentication and access approval workflows.
– Assume that a key logger is present on all your users’ machines. Consider using privileged access management to add multi-factor access and approval workflows to sensitive web and on-premises applications that don’t have native multi-factor authentication. This assures that an attacker cannot replay what they have captured to gain access to your sensitive systems.
Summary
I have made the analogy that many corporate networks are like pieces of candy with a hard, thin shell and a big gooey interior. Organizations’ common misconception is that they can protect the network interior by making the exterior a little harder – but this never works. The best strategy (and the most challenging politically) is to change the consistency of the interior network into a series of concentric layers of protection and trust – limiting access, accepting that some data loss is inevitable, and vastly reducing the potential consequences.
We believe that perimeter security is essential, and there’s always a value in a having a detect-and-respond process in place. However, without significant investments in interior security (including privileged identity management, privileged access management, and secure file storage) to mitigate the inevitable incursion, the best detect-and-respond systems have little real value.
Would you rather have your detect-and-respond system report that a single machine has been compromised, or all of your machines? With the right interior safeguards, you get less bad news that is far easier for your staff to repair.
Are the Analysts Right?
I proposed this strategy to the analysts I met. Their universal response was that most clients can’t grasp the concept of a network interior that’s ultimately too soft. As a result, most will continue to rely solely on expensive perimeter security – an expedient solution with low political risk. As I shook my head in disbelief, I commented that without interior protection, “detect-and-respond” is a half-measure that will eventually fail. The response was: “Yes, that is the best that most clients are willing to do.”
Were the analysts right? Is defense-in-depth too hard for most companies to achieve or even understand?
By Philip Lieberman, CEO, Founder, and President, Lieberman Software
 Bio: Philip Lieberman, noted cybersecurity expert and founder/president of Lieberman Software, has more than 30 years of experience in the software industry. In addition to his proficiency as a software engineer, Lieberman developed the first products for the privileged identity management space, and continues to introduce new solutions to resolve the security threat of privileged account credentials. He is frequently quoted by industry news organizations as well as mainstream media and has published numerous books and articles.
Bio: Philip Lieberman, noted cybersecurity expert and founder/president of Lieberman Software, has more than 30 years of experience in the software industry. In addition to his proficiency as a software engineer, Lieberman developed the first products for the privileged identity management space, and continues to introduce new solutions to resolve the security threat of privileged account credentials. He is frequently quoted by industry news organizations as well as mainstream media and has published numerous books and articles.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.