The Bitdefender hack
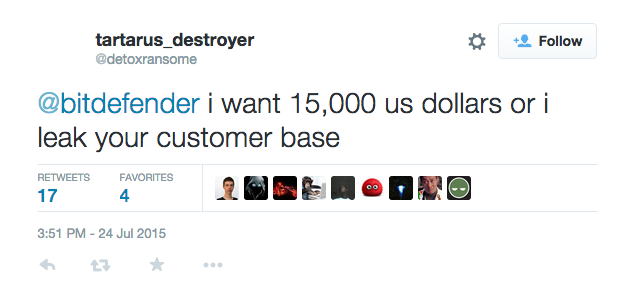
On July 24th 2015, Detoxransome tried to blackmail Bitdefender in exchange of a portion of their customer base. He threatened the company to leak the data he stole if he doesn’t receive the payment he requested.
 On Aug, 1st 2015, he gave some details around the reasons why he hacked Bitdefender on a post on Reddit. He was upset because no one paid attention to him after he allegedly hacked Louis Vuitton. Thus, he decided to hack a bigger fish.
On Aug, 1st 2015, he gave some details around the reasons why he hacked Bitdefender on a post on Reddit. He was upset because no one paid attention to him after he allegedly hacked Louis Vuitton. Thus, he decided to hack a bigger fish.
What Detoxransome was up to before July 24th, 2015
We retraced his criminal forum activity back to June 11, 2015. He tried to sell his wares under different handles. We also know that he was involved in several hacks and discovered vulnerabilities he posted on either Pastebin or syph0n.net.
A few weeks ago, he requested help looking for a server where he could host the front-end of his wares to launch DDOS attacks.
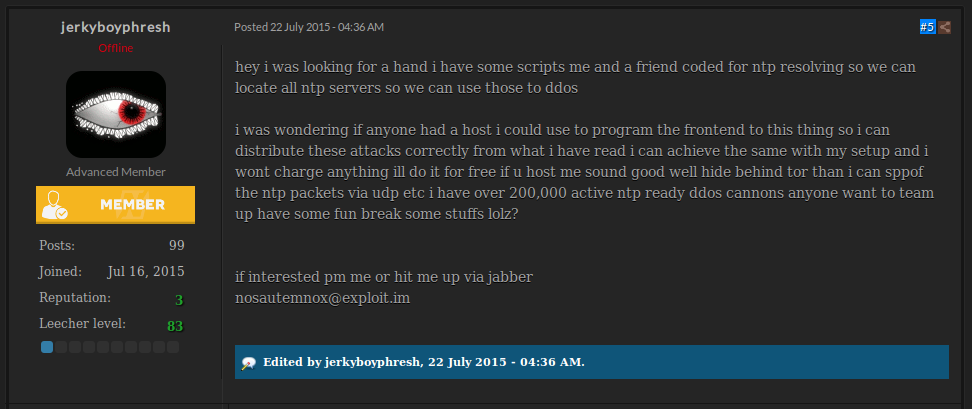 On another board, he tried to sell a Tor-based ransomware dubbed Tartarus Ransomware. He claimed it is better than anything else and offers affiliate programs. Other forum members did not necessarily agree.
On another board, he tried to sell a Tor-based ransomware dubbed Tartarus Ransomware. He claimed it is better than anything else and offers affiliate programs. Other forum members did not necessarily agree.
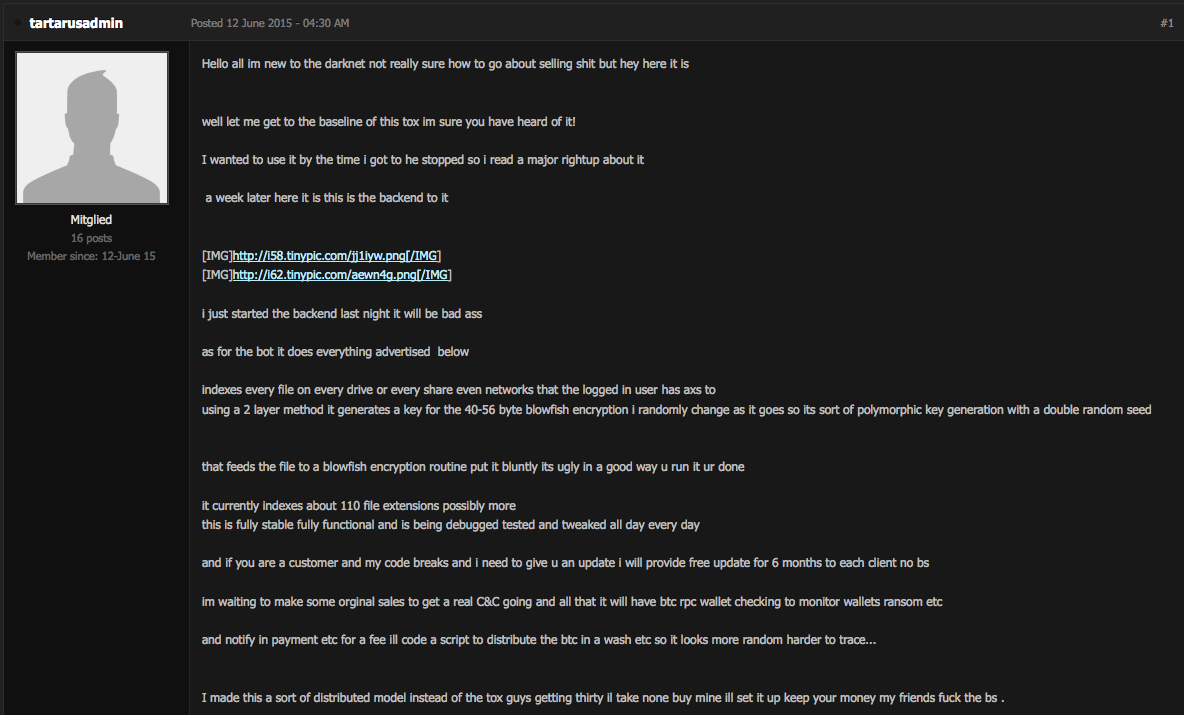
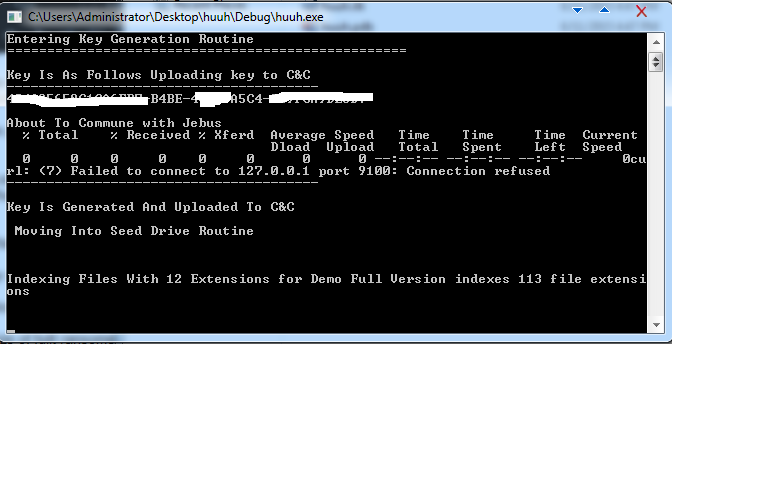
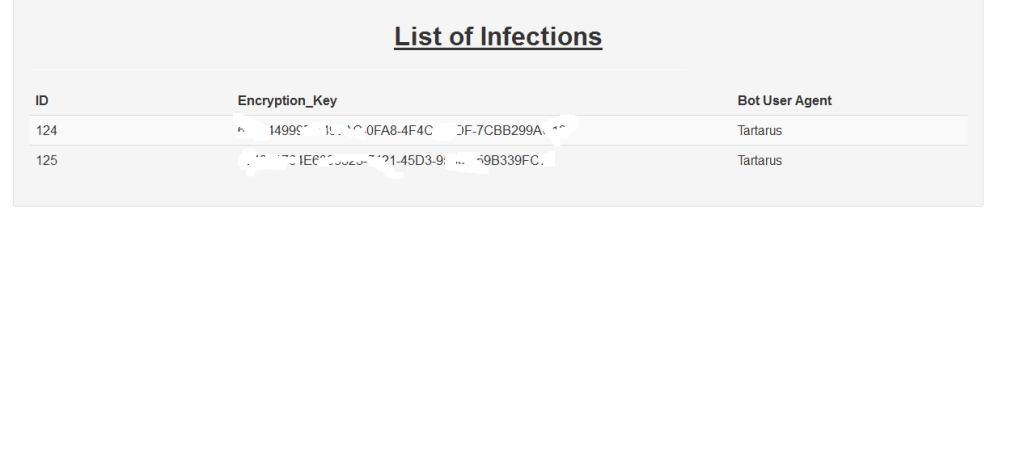
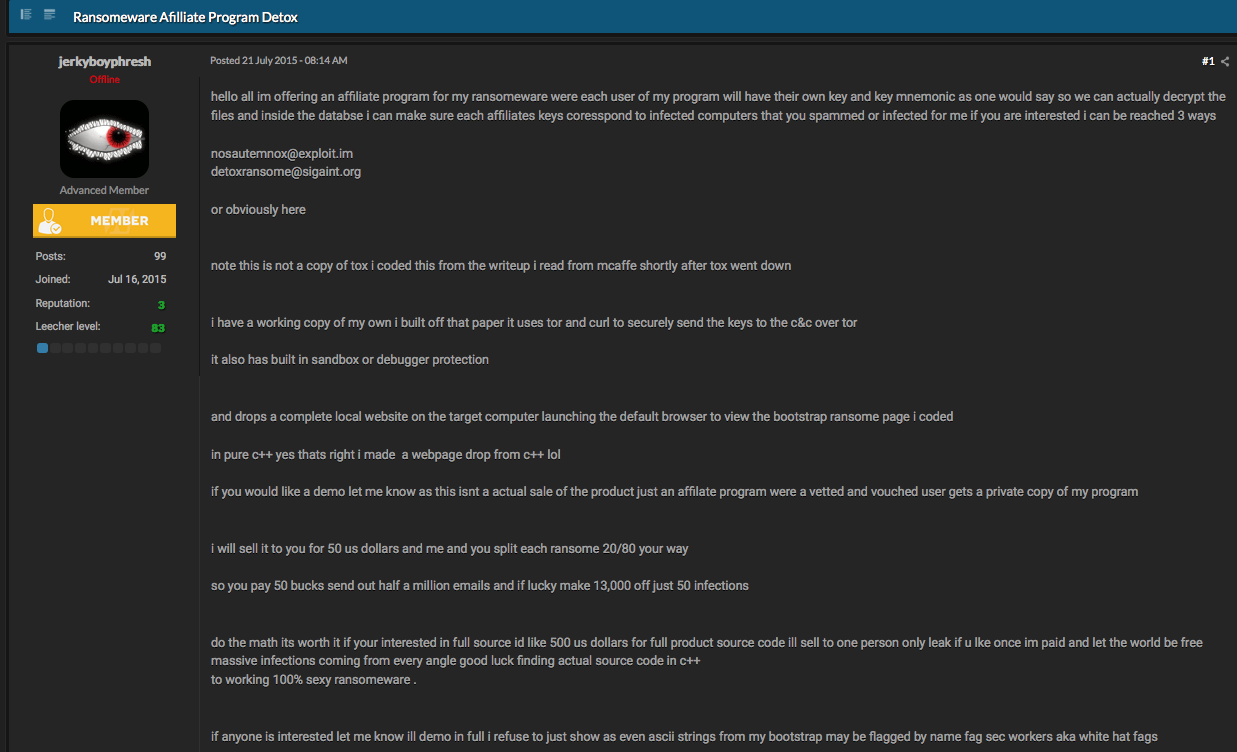 Below are the screenshots Detoxransome posted on his post to demonstrate his ransomware exists.
Below are the screenshots Detoxransome posted on his post to demonstrate his ransomware exists.
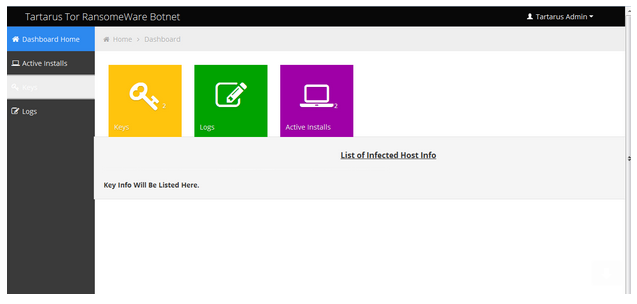 We found two samples of his so called ransomware; it looks like a script kiddie program and shows his limited skills in programing.
We found two samples of his so called ransomware; it looks like a script kiddie program and shows his limited skills in programing.
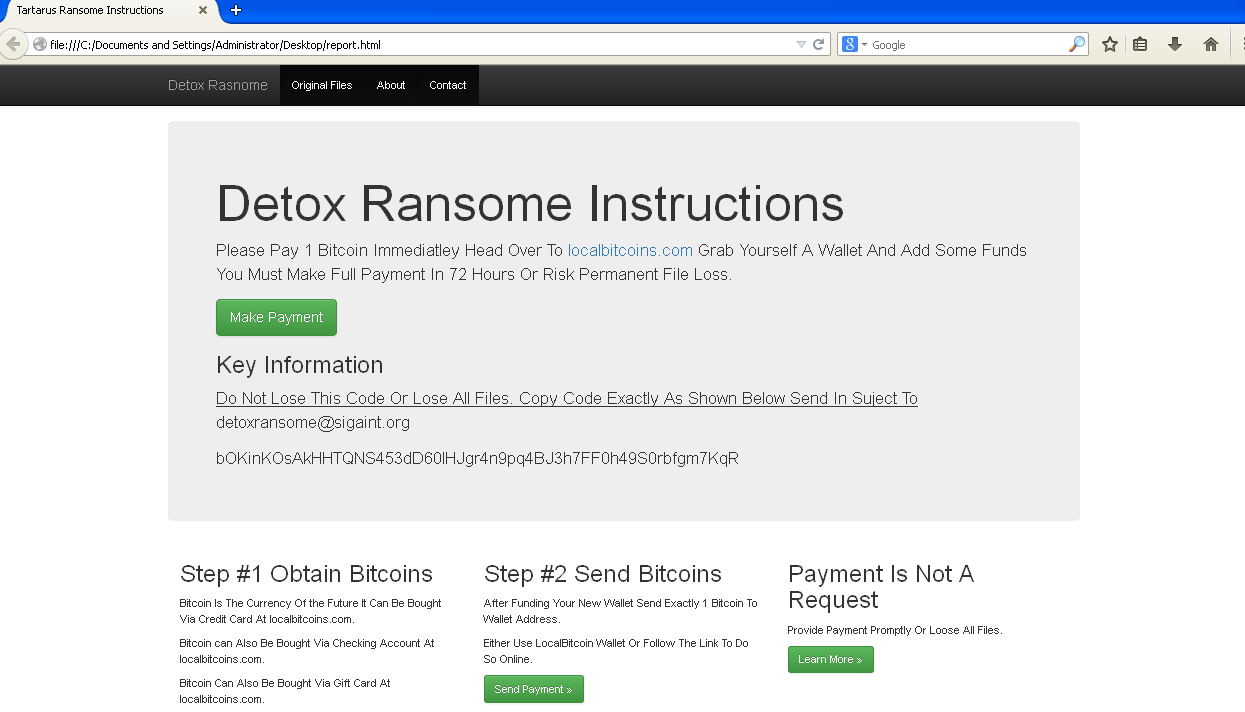
We decided to give it a try and see how and if it works the way Detoxransome claims. Once you execute the malware, it drops a file called report.html and automatically opens it. The file report.html is an HTML page that he uses as a ransomware warning. Nothing was observed to be encrypted by the malware in this debug build, in fact there is a comment to let the author know that the encryption algorithm was commented out prior to building. The report.html page shows a message where he requests a payment of 1 BTC to be sent at the address bOKinKOsAkHHTQNS453dD60lHJgr4n
We have analyzed the sample 6d0daa316dfaad7729971185ec181d
Both files use the following CnC URLs:
- http://fzrqs6ctwtdkzh4z[.]
onion/admin_dash/gate1.php - http://fzrqs6ctwtdkzh4z[.]
onion/admin_dash/btcwalletgen. php
Both of these samples reach out and grab a copy of the Tor and Curl installer packages. The malware then installs Tor and Curl binaries in order to beacon to the CnC rather than using libraries.
From posting dates and also by his own admission it appears that Detoxransome was relatively unknown prior to June of 2015. It would seem that Detoxransome got lucky in discovering a single outward facing server that had a known vulnerability.
We have compiled a list of handles, and other details he uses online to operate his criminal business:
Handles:
- Detoxransome
- nosautemnox
- tartarusadmin
- tartarus
- jerkyboyphresh
- Detox The B0ss
Criminal Forums:
Online services:
- reddit.com
- pastebin.com
- ibin.co
- imagebin.ca
Jabber:
- nosautemnox @ exploit[.]im
- tartarus@exploit.im
Darkweb email address (only accessible via TOR):
-
Detoxransome @ sigaint[.]org
Conclusion :
For a relatively new and inexperienced hacker, Detoxransome has made a name for himself in a big way by attacking one of the biggest names in antivirus and information security. However, this seems to be more of a case of luck than skill. This also looks to someone seeking credit for their wares and activities. We may see more from Detoxransome in the future. For now, keeping your systems patched and being aware of the status of your perimeter devices including what data is leaving those devices should keep you out of harm’s way from criminals like Detoxransome.[su_box title=”About Damballa” style=”noise” box_color=”#336588″] As a leader in automated breach defence, Damballa delivers advanced threat protection and containment for active threats that bypass all security prevention layers. Born for breach defence, Damballa rapidly discovers infections with certainty, pinpointing the compromised devices that represent the highest risk to a business, and enabling prioritized response and refocusing of security experts to the areas of greatest risk to an enterprise. Our patented solutions leverage Big Data from one-third of the worlds Internet traffic, combined with machine learning, to automatically discover and terminate criminal activity, stop data theft, minimize business disruption, and reduce the time to response and remediation. Damballa protects any device or OS including PCs, Macs, Unix, iOS, Android, and embedded systems. Damballa protects more than 400 million endpoints globally at enterprises in every major market and for the world’s largest ISP and telecommunications providers.[/su_box]
As a leader in automated breach defence, Damballa delivers advanced threat protection and containment for active threats that bypass all security prevention layers. Born for breach defence, Damballa rapidly discovers infections with certainty, pinpointing the compromised devices that represent the highest risk to a business, and enabling prioritized response and refocusing of security experts to the areas of greatest risk to an enterprise. Our patented solutions leverage Big Data from one-third of the worlds Internet traffic, combined with machine learning, to automatically discover and terminate criminal activity, stop data theft, minimize business disruption, and reduce the time to response and remediation. Damballa protects any device or OS including PCs, Macs, Unix, iOS, Android, and embedded systems. Damballa protects more than 400 million endpoints globally at enterprises in every major market and for the world’s largest ISP and telecommunications providers.[/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.