In light of the increasing volume and sophistication of cyber threats, organizations needs to identify their relevant risk, determine their cybersecurity posture and act upon it. That much is clear, but it is easier said than done. Organizations needs not only an agreed methodology to work by, but also a tool to help them achieve that goal and properly assess their threat landscape, control maturity and better prepare for the upcoming threats.
The FFIEC (Federal Financial Institutions Examination Council) has developed a Cybersecurity Assessment Tool, which was released on June 2015.
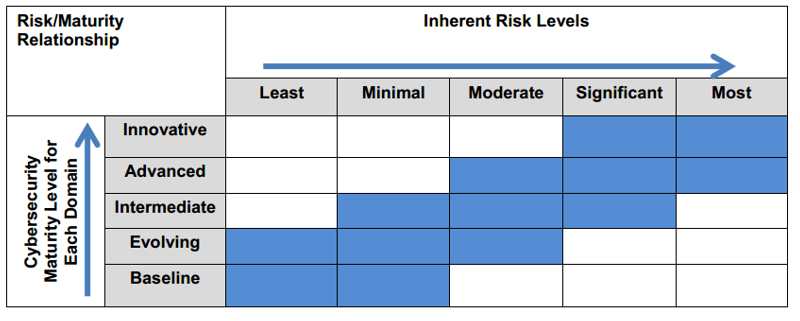
The Assessment presents a new and innovative view on cybersecurity risk management, and consists of two parts: Inherent Risk Profile and Cybersecurity Maturity. Upon completion of both parts, management can evaluate whether the institution’s inherent risk and preparedness are aligned.
Inherent Risk Profile :
Inherent risk incorporates the type, volume, and complexity of the institution’s operations and threats directed at the institution. Inherent risk does not include mitigating controls. The Inherent Risk Profile includes descriptions of activities across risk categories with definitions for the least to most levels of inherent risk. The profile helps management determine exposure to risk that the institution’s activities, services, and products individually and collectively pose to the institution. Cybersecurity inherent risk is the level of risk posed to the institution by the following:
- Technologies and Connection Types
- Delivery Channels
- Online/Mobile Products and Technology Services
- Organizational Characteristics
- External Threats
The Assessment’s second part is Cybersecurity Maturity, designed to help management measure the institution’s level of risk and corresponding controls. The levels range from baseline to innovative. Cybersecurity Maturity includes statements to determine whether an institution’s behaviors, practices, and processes can support cybersecurity preparedness within the following five domains:
- Cyber Risk Management and Oversight
- Threat Intelligence and Collaboration
- Cybersecurity Controls
- External Dependency Management
- Cyber Incident Management and Resilience
 Now, Management can review the institution’s Inherent Risk Profile in relation to its Cybersecurity Maturity results for each domain to understand whether they are aligned. Management can then decide what actions are needed either to affect the inherent risk profile or to achieve a desired state of maturity. On an ongoing basis, management may use the Assessment to identify changes to the institution’s inherent risk profile when new threats arise or when considering changes to the business strategy, such as expanding operations, offering new products and services, or entering into new third-party relationships that support critical activities. Consequently, management can determine whether additional risk management practices or controls are needed to maintain or augment the institution’s cybersecurity maturity.
Now, Management can review the institution’s Inherent Risk Profile in relation to its Cybersecurity Maturity results for each domain to understand whether they are aligned. Management can then decide what actions are needed either to affect the inherent risk profile or to achieve a desired state of maturity. On an ongoing basis, management may use the Assessment to identify changes to the institution’s inherent risk profile when new threats arise or when considering changes to the business strategy, such as expanding operations, offering new products and services, or entering into new third-party relationships that support critical activities. Consequently, management can determine whether additional risk management practices or controls are needed to maintain or augment the institution’s cybersecurity maturity.
 Although the Assessment is not mandatory yet, The FFIEC intention is to give time to organizations to review, comment and prepare to implement the Assessment in their organization during the upcoming year.
Although the Assessment is not mandatory yet, The FFIEC intention is to give time to organizations to review, comment and prepare to implement the Assessment in their organization during the upcoming year.
When we look at the grand picture of the assessment, it lacks several key issues:
- There is missing information about Threat Actors, their motivations (which assets are they targeting and why), their used Attack Methods and Activity Level (Actual up-to-date threat landscape).
- The Assessment doesn’t perform a measurable analysis, it leaves the organization itself to set the maturity score, inherent risk and even the relation between them.
- There is no correlation between different types of threats against different type of controls (or the effect of a control in mitigating a specific threat).
- Not Actionable – Assessment like these take a lot of time and resources to conduct, which result in irrelevant data (due to the ever changing nature of control status) and more “what we should have done in the past” rather than “what we should do in the future”. Therefore the organization needs to continuously monitor and measure its control maturity and threat landscape using an automated system.
Overall, the tool describes a solid and important methodology on cybersecurity risk management, but in fact it defines the building blocks in cyber risk management and not an organized methodology that defines objectively and monovalent the actual risk level against measurable threats and control maturity. The tool is an additional standard (such as NIST CSF, FISMA, Israeli Banking Regulation 361, Etc.) that describes a guideline and the principles of cybersecurity risk management process but is not an actionable tool.[su_box title=”About FFIEC” style=”noise” box_color=”#336588″] The Federal Financial Institutions Examination Council (FFIEC) was established on March 10, 1979, pursuant to title X of the Financial Institutions Regulatory and Interest Rate Control Act of 1978 (FIRA), Public Law 95-630. In 1989, title XI of the Financial Institutions Reform, Recovery and Enforcement Act of 1989 (FIRREA) established The Appraisal Subcommittee (ASC) within the Examination Council.[/su_box][su_box title=”About Cytegic” style=”noise” box_color=”#336588″]Cy-te-gic /pronounced: sʌɪ-ˈtē-jik/ adjective: A plan of action or strategy designed to achieve a long-term and overall successful Cyber Security Posture Optimization – “That firm made a wise Cytegic decision”. Cytegic develops a full suite of cyber management and decision-support products that enable to monitor, measure and manage organizational cyber-security resources.Cytegic helps organization to identify threat trends, assess organizational readiness, and optimize resource allocation to mitigate risk for business assets.[/su_box]
The Federal Financial Institutions Examination Council (FFIEC) was established on March 10, 1979, pursuant to title X of the Financial Institutions Regulatory and Interest Rate Control Act of 1978 (FIRA), Public Law 95-630. In 1989, title XI of the Financial Institutions Reform, Recovery and Enforcement Act of 1989 (FIRREA) established The Appraisal Subcommittee (ASC) within the Examination Council.[/su_box][su_box title=”About Cytegic” style=”noise” box_color=”#336588″]Cy-te-gic /pronounced: sʌɪ-ˈtē-jik/ adjective: A plan of action or strategy designed to achieve a long-term and overall successful Cyber Security Posture Optimization – “That firm made a wise Cytegic decision”. Cytegic develops a full suite of cyber management and decision-support products that enable to monitor, measure and manage organizational cyber-security resources.Cytegic helps organization to identify threat trends, assess organizational readiness, and optimize resource allocation to mitigate risk for business assets.[/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.




