Executive Summary
Everything has its price on dark web, and almost anything can be sold or bought openly. Although sometimes it seems that to succeed in cybercrime, a person must be a Jack of all trades, in reality almost every criminal endeavor requires various tools and services provided by a network other members.
The cybercriminal underground is quite verticalized, with threat actors specializing in particular areas of expertise. It is this distribution of expertise that contributes to the underground market’s resiliency. Similar to drug cartels, once you remove one threat actor or forum, rivals will immediately take its place. As a result, to kickstart a campaign and move beyond a concept to the final execution and substantial profit, a puzzle game has to be completed first.
Background
In the past 20 years, the cybercriminal underground has evolved from a handful of disperse message boards, mostly built around mundane e-commerce fraud primarily conducted by Eastern-European fraudsters, to a highly complex ecosystem that we now call dark web. Today the shadowy world of the internet is comprised of communities divided by various geographical regions, specialty, and the experience of its members and is capable of supporting both entry-level script kiddies and the masterminds of incredibly sophisticated attacks, such as the Taiwan ATM heist and malware attacks on Russian banks, which netted threat actors tens of millions of dollars.
Threat Analysis
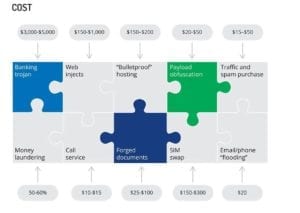
A botnet operation is the best example to put things into perspective and to explain the complexity of all necessary steps to achieve the maximum profitability levels for its operators. The following example illustrates the upfront cost of launching and sustaining a cyber operation, as well as the direct and secondary financial returns for its operators.
- A banking trojan license is one of the most expensive elements of a cybercriminal campaign and can be obtained from professional malware developers for $3,000–$5,000.
- Then to intercept banking credentials, web-injects for each target financial institution have to be acquired separately and can cost anywhere between $150–$1,000 per set. In the past year, we’ve seen a significant increase in the cost of web-injects targeting Canadian institutions, offered at the upper-level of the price spectrum, while the cost of malware targeting U.S.-based banks has remained the same.
- To maintain consistent visibility into the entire operation and to control an infected network of computers, bulletproof hosting in one of the unfriendly jurisdictions in China, the Middle East, or Eastern Europe is required. Monthly rental of a web-server in a datacenter favorable to criminal activity will usually cost $150–$200.
- To ensure the consistent payload delivery, and to remain undetected by antivirus products, the executable file must be “cleaned” and obfuscated daily and in the case of a very large-scale operation, several times a day. Such services are available for $20–$50 per single payload obfuscation; however, lower prices can be negotiated for large-volume orders.
- Steady web traffic redirected to the infected resource or email spam campaign are two primary delivery vehicles of malicious payloads. While it’s going to cost $15–$50 to get a thousand unsuspecting people to visit the infected web page, professional spam operators will charge $400 per million of successfully delivered emails.
- Once the malware is successfully planted and banking credentials intercepted, the perpetrator has to work with a chain of mule handlers and money-laundering intermediaries to receive a final pay-off. A money launderer with a stellar reputation and is capable of quick turnaround, will charge a hefty 50-60 percent commission from each payment transferred from a victim’s account. In some cases, an additional 5-10 percent commission might be required to launder the funds and deliver it to the main operator via preferred payment method, such as bitcoin, Web Money, or the Western Union.

- In the case an additional phone confirmation is needed to proceed with a money transfer, it will be facilitated by one of the underground calling services, with prices standing at $10–$15 per each call.
- If an additional document and phone verification are needed to proceed with the money transfer, various supporting vendors are available. A counterfeit driver’s license may be delivered within several hours for $25 while a more sophisticated video selfie will cost $100.
- To minimize the chances of an account holder noticing an unauthorized transaction, to intercept SMS confirmation, or to render an owner’s phone entirely unreachable for the duration of the attack, an email/phone “flooding” can be purchased for $20. However, the cost of a cloned SIM card is significantly more expensive at $150–$300.
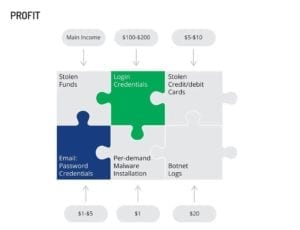
Aside from funds stolen from compromised bank accounts, persistent access to an extensive network of victims around the world will inevitably generate a significant residual income.
- Look-ups of login credentials to resources not directly targeted by the attacker, can be offered to members of the underground and may fetch an additional $100–$200 per set. Such a service is in demand from niche buyers, who are likely to be engaged in a commercial and nation-state spying campaigns.
- Credit card information may be quickly sold via one of the dark web marketplaces at $5–$10 a piece.
- The demand for various e-commerce credentials is steady; however, the recent proliferation of large-scale account takeover campaigns has created a surplus of available data, lowering the price to $1–$5 per each set of credentials.
- In some cases, when an attacker is unable to achieve the desired results, per-demand malware may be offered to other criminals for approximately $1 per installation.
- At the end of its reasonable shelf-life, random botnet logs comprised of unstructured data collected can be easily sold for $20 per gigabyte of data.
Outlook
Although this example only examined a single popular attack method, a similar supporting infrastructure would be used to initiate other cybercriminal operations, including ransomware and phishing campaigns. It is going to be rare to attribute a cyberattack to a sole individual operating in isolation, because success requires expertise across multiple disciplines to take an attack from conceptualization to profit. The means to do so are all available for a price; cost would simply depend on how sophisticated a campaign is desired by the actor.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



