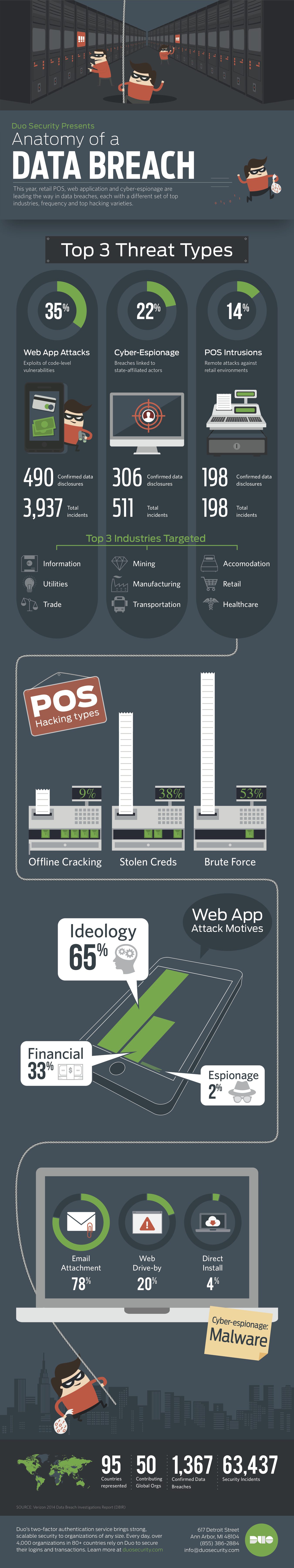
When it comes to the 2014 Verizon Data Breach Investigations Report (DBIR), web application, cyber-espionage and POS intrusions topped off the list of most frequently occurring categories of data breaches. The one common theme throughout most of the attack vectors includes Verizon’s recommendation for the one security control that transcends many different categories of attack, from retail to crimeware – that is, two-factor authentication.
Why is two-factor such a fundamental aspect of any organization’s information security strategy? It brings a lot to the table in one simple solution. Among other things, it does the following:
-Provides a secure second layer of defense that remote attackers can’t penetrate.
-Protects any type of account you log into, from web apps to VPNs to enterprise cloud-based apps.
-Modern two-factor solutions allow authentication through convenient mobile apps, letting you verify your identity without requiring an extra device.
Two-factor authentication is a more effective way to protect organizations than simple usernames and passwords, as the latter can be cracked (if weak in nature) or given away if employees are tricked by phishing schemes.
Duo Security recognizes the benefits of implementing two-factor authentication solutions – as well as the risks. Provided below is an infographic created by Duo Security that depicts the top threat types, top targeted industries, hacking types, web attack motives and more in today’s information security field. The infographic presents an accurate idea of what the data breach landscape was in the past year.
About Duo Security
 Duo Security provides cloud-based two-factor authentication to more than 4,000 organizations worldwide.
Duo Security provides cloud-based two-factor authentication to more than 4,000 organizations worldwide.
The company’s unique, high-availability architecture provides centralized management, self-service enrollment, and interactive secondary login through an intuitive web interface, eliminating the high costs, complexity, and confusion associated with traditional two-factor systems. In as little as fifteen minutes, Duo’s innovative and easy-to-use technology can be deployed to protect users, data, and applications from credential theft, account takeover and phishing attacks.
Try it for free at www.duosecurity.com