Being at the forefront of fraud prevention, our level of awareness for fraud related schemes is definitively higher than it is for any other business. We live to fight back fraud 24 by 7, and being one of the pioneers in the industry to champion DMARC and knowing its benefits.
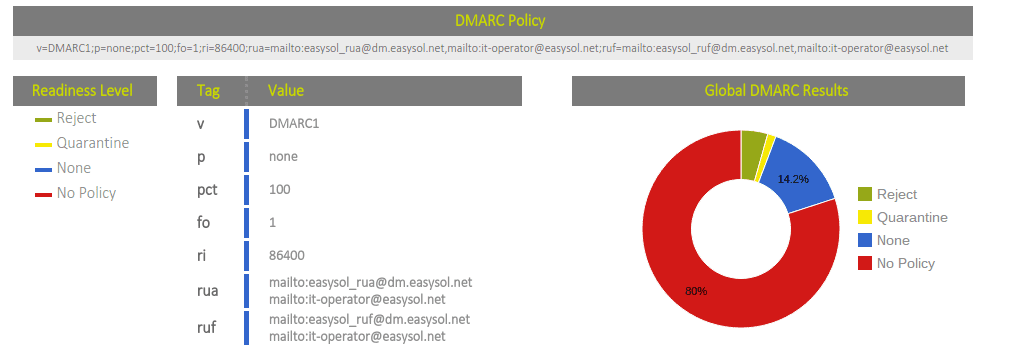
we decided to deploy the DMARC policy in monitoring mode, as you can see here :
P=none means no action is taken on emails that fail the authentication protocol, however, we have the visibility as to who is spoofing our domain and for what purpose.
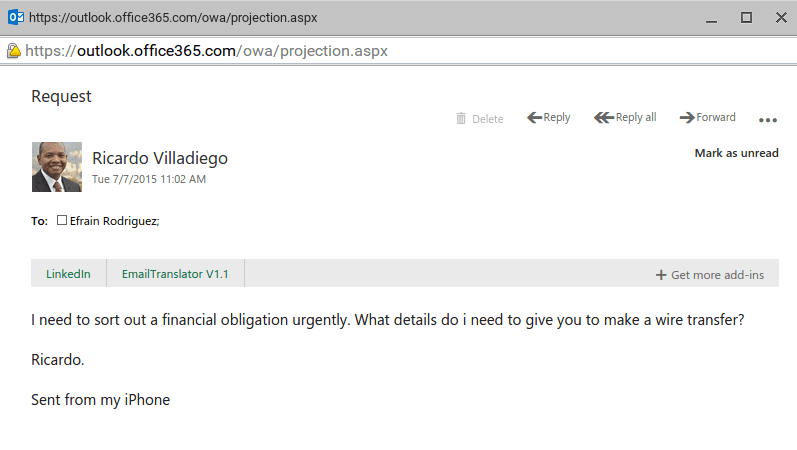
Knowing that it was a matter of time until criminals attempted a move against our organization, we started our monitoring process. And it was last week when I received a call from the CFO, who was properly trained to identify suspicious emails, to validate if an email requesting a wire transfer was sent legitimately.
While you never want to be the attempted victim of fraud, part of me was happy this happened, because I’ve been thinking about this post for some time.
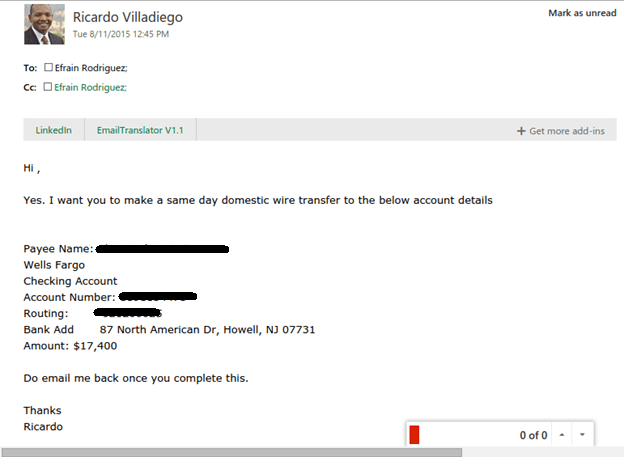
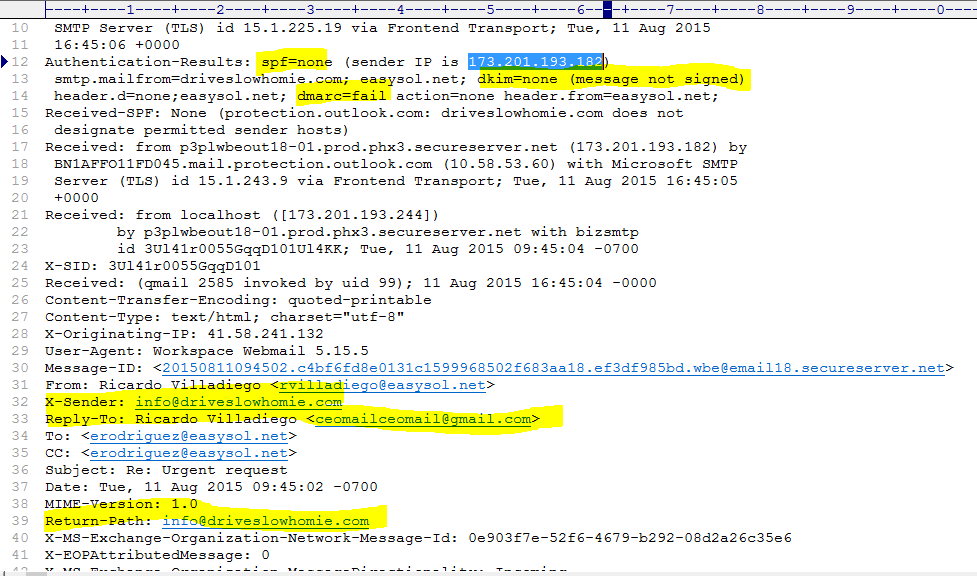
Below you see the screenshot with the spoofed email.
One note to make here is that most likely the recipient’s account was also compromised, so we immediately notified the financial institution so they can conduct their investigation.
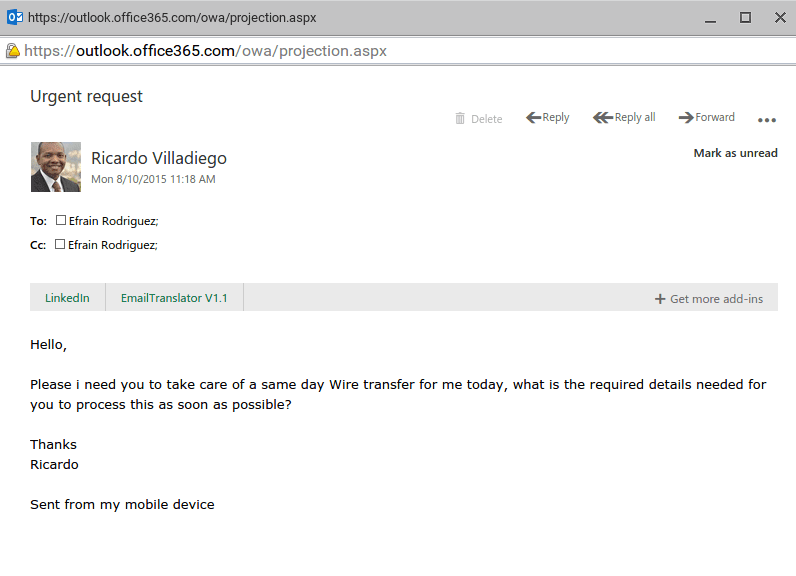
A common technique, employed here is to follow-up with additional emails to increase the pressure:


These attacks exist because it is still possible to easily and cheaply forge emails from any address on the Internet as outlined by FS-ISAC/CERT. The alternative attack vector for these kinds of attacks is to directly compromise the sender’s email account via malware or some other method of compromise. This method, while possible it is harder and more expensive for the attacker. We believe that steps must always be taken to push costs to adversaries and never present them with an easy and cheap option.
What to Do?
- Deploy DMARC to gain visibility into email attacks and spear-phishing both targeting your employees and your clients
- Consider leveraging a DMARC visibility and compliance product such as DMARC Compass
- Confirm with your enterprise email team that your email enterprise email provider honors DMARC policies on inbound email to prevent spear-phishing attacks.
- Train your leadership, especially in finance about the risks associated with these kinds of attacks, methods of detection and manual authentication.
This is just another real-world example of the all-to-common attacks that are putting many enterprises at risk. We strongly encourage any enterprise that relies on trusted email-based communication with their clients to evaluate these recommendations to see if they work for you. Also, even if you have no plans currently to leverage DMARC to block spoofed email, it is very important to leverage the power of DMARC to gain visibility into real or potential attacks that might lead directly to successful attacks.
We are the living proof that it is a matter of time until criminals threaten your business. These attacks are inexpensive and easy to launch, as such, they will continue to happen until organizations improve their email authentication methods, making it harder for cybercriminals to carry on their fraudulent operations.[su_box title=”Ricardo Villadiego, CEO of Easy Solutions” style=”noise” box_color=”#336588″]