11 months back, I successfully hacked Facebook Security and brought it to their notice.I sent them the following message: “I have written a script where through any mobile/web application, I can post any message, image, or video on a user’s and/or their friend’s timeline on behalf of the original user without any prior permission.”
Featured Download: Social media access at work. Do your employees know the rules?
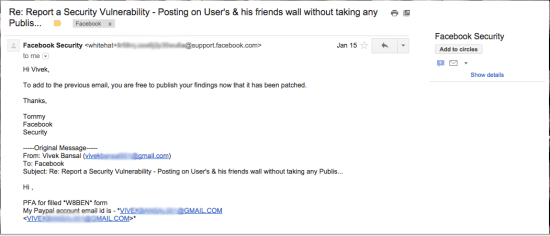
I received $2000 from Facebook as a token of their appreciation, as well as an email stating that they had patched the vulnerability and that I could make it public, as you can see from this screenshot:
The news was also covered by a few media outlets.
I was happy with my work and took for granted the fact that they must have solved the problem. However, recently I was surprised to discover that in fact NO ACTION had been taken to repair the loophole I had originally found. Indeed, I was able to reproduce my exploit and breach their security AGAIN using the same script. I was shocked that everything went off as it had before, so I wrote them again expressing my concerns.
I also wrote an article in which I question how serious Facebook’s teams are about fixing security issues, which can be read here: http://goo.gl/VrvOBr.
This is not the first Facebook vulnerability ever discovered. In July 2013, a guy named Khalil found a vulnerability that he exploited in order to successfully post a comment on Mark Zuckerberg’s timeline.
Clearly, with the kind of access my bug grants, it’s easy to spam other users and to have people steal your identity, posing as you and posting on loved ones’ timelines but all the while an imposter.
And with hundreds of millions of people accessing Facebook every day via mobile and other web applications, the fact that Facebook won’t patch security vulnerabilities is very serious.
For more information about the vulnerability I discovered, please watch this video: https://www.youtube.com/watch?v=G-LrXJeTjlI.
By Vivek Bansal, Android & Back-End Developer, TimesCity at Times Internet Limited | @vivekbansal001
 Bio: Vivek Bansal currently works at TimesCity as and Android and back-end developer. He is mostly interested in Research & Development, back-end developing, and game development. His specialties include wireframe / mockup design for Android apps and writing enterprise-quality code backed by robust automated unit and regression-test suites.
Bio: Vivek Bansal currently works at TimesCity as and Android and back-end developer. He is mostly interested in Research & Development, back-end developing, and game development. His specialties include wireframe / mockup design for Android apps and writing enterprise-quality code backed by robust automated unit and regression-test suites.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.