Security researchers have caught a Bitcoin-hijacking Chrome extension that only managed to grab one BitCoin transaction before being exposed. Researchers said the malicious extensions used an attack technique that first emerged last year, dubbed FacexWorm, and added that they noticed re-emerging activity earlier this month. FacexWorm propagates in malicious Facebook Messenger messages and only attacks Chrome. Security experts commented below.
Allan Liska, Senior Solutions Architect at Recorded Future:
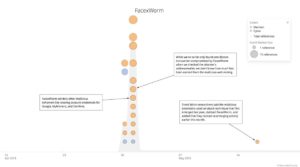
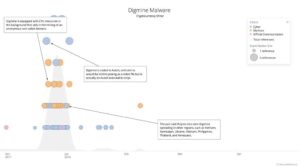
 “The new FacexWorm campaign is an example of attackers building upon successful previous campaigns and adding new features. This is at least the third campaign this same attacker has launched using this methodology. The first campaign, in August of 2017, pushed adware and attempted to harvest users credentials, the second campaign, in December, added the Digmine malware. This latest campaign adds in a cryptocurrency scam that attempts to steal money from victim’s wallets.
“The new FacexWorm campaign is an example of attackers building upon successful previous campaigns and adding new features. This is at least the third campaign this same attacker has launched using this methodology. The first campaign, in August of 2017, pushed adware and attempted to harvest users credentials, the second campaign, in December, added the Digmine malware. This latest campaign adds in a cryptocurrency scam that attempts to steal money from victim’s wallets.
While the capability of the attacks has increased, the delivery methods have remained the same: the attacker uses a combination of Facebook Messenger and a malicious Chrome extension to deliver the malware. Interestingly, however, these attackers appear to have dropped their attempt to get victims to install a fake Adobe Flash plug-in.
In order to protect themselves, users should avoid clicking on Facebook messenger links from friends that seem unusually worded or out of character – at least confirm before clicking and their friends may not know they have been infected. In addition, never install a Google Chrome extension directly from a website, instead download them from the Google Chrome Store directly. Extensions in the store are regularly monitored for potential trojans installed in the code.”
Timeline on FacexWorm:
Timeline on Digmine Malware:
Sean Newman, Director of Product Management at Corero Network Security:
 “Reports of the new Facex worm spreading across Facebook, via faked messenger video links, raises the potential for large-scale malicious botnets to new heights. With an estimated 2.2 Billion active Facebook users, there is real potential for botnets of tens, or even hundreds, of millions of devices with large amounts of computing power and masses of connected bandwidth.
“Reports of the new Facex worm spreading across Facebook, via faked messenger video links, raises the potential for large-scale malicious botnets to new heights. With an estimated 2.2 Billion active Facebook users, there is real potential for botnets of tens, or even hundreds, of millions of devices with large amounts of computing power and masses of connected bandwidth.
“In the case of Facex, the objective appears to currently be crypto-mining and crypto-currency theft, on a mass scale, but the power of its architecture means that each newly recruited bot can be instructed to carry out whatever task the controller decides. With that flexibility, it’s easy to think that other objectives could be achieved with very little effort, such as launching DDoS attacks on a massive scale. This latest revelation is just another reason, in a growing list, why organisations should be proactively protecting themselves from DDoS attacks. And, those that place a high value on every minute of their online presence should be deploying the latest generation of always-on, real-time, automatic DDoS protection solutions.”
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



