Over the last two/three years, when chatting with clients, or delivering training, there has been occasions when the following question has come up:
‘How do I know FIPS/140-2 encrypted drives are as secure as claimed by the commercial sales bumph of the provider?’
AKA- how confident can the user be in the modern era of data breaches – can they be assured that, if the worse-case scenario does occur, their sensitive data objects are not placed in readable reach of the finder, or for that matter criminal?
So, having decided that there is a real need to prove (or disprove) the claims, I set off to take some action to test the theory in hands-on, practical terms, and commenced on my 10 Step technical venture with a 500GB iStorage diskAshur PRO encrypted drive in-hand, loaded with data.
Step 1: Connect drive to PC to assure that it was in full working order on two Operating Systems – Linux and Windows 10 – both loaded and mounted the encrypted drive after the correct PIN code had been input and accepted – at this point we have a green light displayed on the drive and full access to the secured contents was achieved.
Step 2: With hammer in hand, a pair of pliers and a screwdriver I started to break open the drive outer cover.
Steps 3 – 5: The following steps were a matter of gradually pealing back the drive internals and along that path upon every part being deconstructed from the build of the part disassembled drive, it was again mounted, the PIN entered, and authenticated, and access was gained to the drive contents– see images 1 – 3. Now, things are getting serious, but yes, the part disassembled drive is still working.
Image 1 – Drive Outer Case Removed Image 2 – PIN Pad Outer Removed Image 3 – Drive Exposed
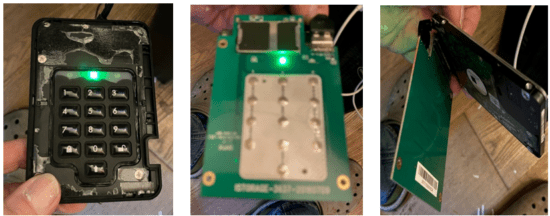
Note 1: Throughout Steps 3 to 5, the drive was again mounted and was allowing the PIN Pad to be operated (even without the outer cover) and access could be gained to the dive files once authenticated.
Step 6: Step 6 was the point at which the internal secured (encrypted) hard drive was disconnected from the drives hard-coded security chip – as shown at Image 4 below:
Image 4 – Internal Drive Removed

Step 7: Reconnect the drive to a Linux O/S and reattach the interface cable to the disk bare keyboard – enter pin, and as testaments to the disk’s physical durability, it could still be properly authenticated, and access could be achieved to its (See Image 2).
Step 8: The last acid test to be carried out was to attach the removed hard drive to a USB 3.0 TO IDE/SATA interface (which had been tested to assure it was in full working condition). It is at this juncture where it was proven, beyond all reasonable doubt that the data stored in encrypted form on the iStorage drive was secure – in fact, the drive would not even mount in a raw format.
Step 9: Step 9 was a gentle attempt to gain access to the drive’s hardware security logic chip secured as directed under the FIPS/140-2 Standard.
Note 2: This does not attack the components with force but attempted to gain access to the component at the physical level of the circuit board.
Step 10: The final test of the iStorage FIPS/140-2 Drive was to reassemble the internal drive, and connect it to the circuit board storing the hardware stored encryption key, and attempt to authenticate as had been carried out at all previous stages – at this point, multiple attempts were carried out to load the drive, but the only outcome was to show a RED light, and access to the secure contents of the drive were no longer possible (even with the correct PIN) – AKA the keys to the encryption algorithm had been destroyed, and access could not be achieved – see Image 5 below of the locked drive.
Image 5 – Inaccessible Locked Drive
(Red Light – Locked)

Of course, there could be the additions of Step 11 which would be to attempt to recover the secured data from the physical drive, but this would leave a final two obstacles to overcome before gaining access to the potentially sensitive data, and they would be as follows:
- If any data could be recovered, it would still be in an encrypted, unreadable format (secure)
- Given the secured data objects had been processed with AES-XTS 256 full disk hardware encryption, you will need to have some time on your hands (and possibly an extended life) – depending where you look for the information as to how long it will take to break the encryption – but as an example, secured by a 12-character passcode, it is estimated it would take 6 billion years to brute-force. However, let’s us take into account that in the world of technology, advances are made, and as such the time to brute-force could potentially be significantly reduced – maybe as low as just 1 billion years – good luck with that!
Conclusion
The next time I am asked the question:
‘How do I know FIPS/140-2 encrypted drives are as secure as claimed by the commercial sales bumph of the provider?’
At least, in the case of iStorage drives I can save some time with the conversation, and simply hand them this 10-step journey of evidence.
The only leaves one thing to do – for sale, one iStorage drive as shown at Image 6 below – one carful user – all reasonable offers will be considered.
Image 6 – Drive for Sale

The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.