Distributed denial of service (DDoS) attacks are a constantly evolving menace that threaten online businesses with downed websites, financial losses and damaged client relationships. As perpetrators continue to adopt new technologies and methods to execute attacks, the need for organizations to stay informed and up-to-date with the latest trends in online security has never been greater.
Our latest DDoS Threat Landscape report reviews the changes in DDoS attack patterns in Q3 2015. The report was compiled using data from 7,752 network and application layer assaults mitigated by Imperva Incapsula in Q3 2015.
The third quarter was notable for a number of reasons, not least of which was the high number of attacks targeting clients in our network during this period.
On average we mitigated 129 DDoS attacks every day, representing a steep 116 percent increase from the previous quarter. Additionally, the changes in attack tactics we witnessed point to new threats of which every online entity should be aware.
Key Findings
Looking back at Q3 2015, we can identify several clear patterns that defined this time period in DDoS mitigation, including:
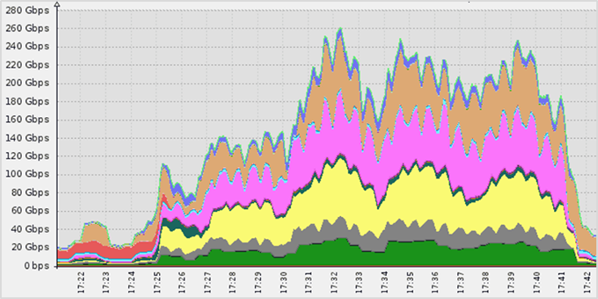
- 100+ Gbps attacks became commonplace: A 100+ Gbps network layer attack was mitigated once every other day, with the largest one peaking at 260 Gbps. The largest application layer attack peaked at 268,800 requests per second.
- China cemented its status as top attacking country: 37.5 percent of DDoS botnet traffic originated in China, making it by far the leading source country of attacks worldwide.
- Attackers focused fire on US and APAC hosted websites: US hosted websites were targeted by 45.8 percent of DDoS botnet traffic, making them the most attacked worldwide. APAC hosted websites were on the receiving end of 40.7 percent of botnet traffic.
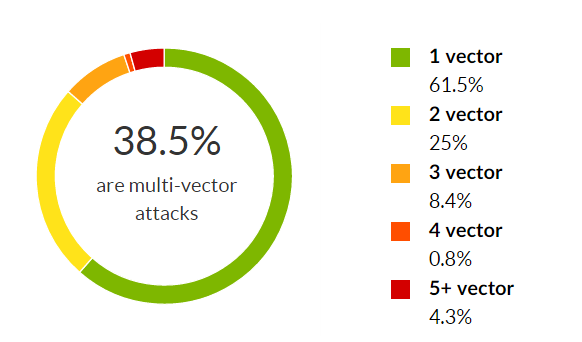
- The increased sophistication of multi vector attacks: While the number of multi-vector attacks decreased from 44 percent in the second quarter, they increased in sophistication, with eight and nine vector assaults taking place.
- The resurgence of Baidu impersonators: After a huge decrease in Q2 2015, there was a resurgence in Baidu bot impersonators, most likely due to the increase in DDoS attacks out of China.
- Attacks grew shorter:The duration of network layer attacks was markedly down, with only four percent lasting more than three hours. Still, the longest one lasted for 31 days. The longest application layer attack lasted more than 20 days.
Unprecedented Spike in Attack Numbers
The most prevalent trend we saw in Q3 2015, was the unprecedented spike in the number of network and application layer DDoS attacks, both increasing by more than 100 percent, compared to the previous quarter.
At the same time, there was a marked decrease in the duration of network layer assaults. This can be taken as a sign of the increased use of DDoS-for-hire services (a.k.a., streesers or booters), as they typically only offer limited access to their botnet resources.
For certain time frames, application layer attacks actually increased in duration, as evidenced by the 14.6 percent of attacks that lasted longer than 12 hours; the figure is up from 6.2 percent in the second quarter.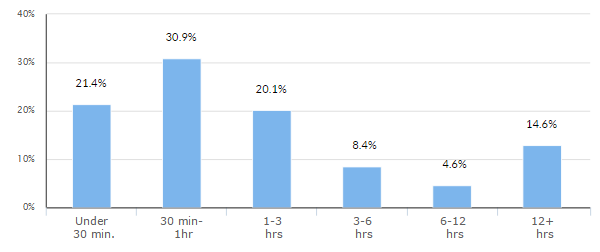 Additionally, there was a significantly higher target distribution among Imperva Incapsula clients, with a much higher percentage of websites being targeted by DDoS attacks. This is a potentially worrying trend going into the final quarter of 2015.
Additionally, there was a significantly higher target distribution among Imperva Incapsula clients, with a much higher percentage of websites being targeted by DDoS attacks. This is a potentially worrying trend going into the final quarter of 2015.
Methodology
Our analysis is based on DDoS data collected from 2,732 network layer and 5,020 application layer attacks on websites using Incapsula services from July 1 through August 29 of this year, referred to as Q3 or the third quarter.
Information about DDoS bot capabilities and assumed identities comes from a random sample of 4.34 billion bot sessions collected from such assaults over the same period.
Data from Q2, or the second quarter, is taken from 1,572 network layer and 2,714 application layer attacks on websites using Incapsula services from March 1, 2015 to May 7, 2015.[su_box title=”About Imperva®” style=”noise” box_color=”#336588″] Imperva® (NYSE:IMPV), is a leading provider of cyber security solutions that protect business-critical data and applications. The company’s SecureSphere, Incapsula and Skyfence product lines enable organizations to discover assets and risks, protect information wherever it lives – in the cloud and on-premises – and comply with regulations. The Imperva Application Defense Center, a research team comprised of some of the world’s leading experts in data and application security, continually enhances Imperva products with up-to-the-minute threat intelligence, and publishes reports that provide insight and guidance on the latest threats and how to mitigate them. Imperva is headquartered in Redwood Shores, California.[/su_box]
Imperva® (NYSE:IMPV), is a leading provider of cyber security solutions that protect business-critical data and applications. The company’s SecureSphere, Incapsula and Skyfence product lines enable organizations to discover assets and risks, protect information wherever it lives – in the cloud and on-premises – and comply with regulations. The Imperva Application Defense Center, a research team comprised of some of the world’s leading experts in data and application security, continually enhances Imperva products with up-to-the-minute threat intelligence, and publishes reports that provide insight and guidance on the latest threats and how to mitigate them. Imperva is headquartered in Redwood Shores, California.[/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.