DomainTools identifies over 300 websites tricking web users into thinking they’re clicking on to UK high street bank websites
London, UK, – DomainTools, the leader in domain name and DNS-based cyber threat intelligence, today released research regarding the plethora of cybersquatters and how they target popular UK banks. DomainTools found 324 registered domains using the trademarked names of five of the UK’s top high street banks. Domains masquerading as legitimate UK bank websites are often used by hackers to trick customers into handing over personal details or login information.
Cybersquatting (also known as domain squatting) is the act of registering a domain name with the purpose of getting monetary benefit from a trademark that belongs to someone else. These domains are often used in phishing email campaigns and various other kinds of scams including pay per click ads (often for competitors’ services), for-profit survey sites and affiliate program abuse, or more nefarious content like ransomware and drive-by download campaigns.
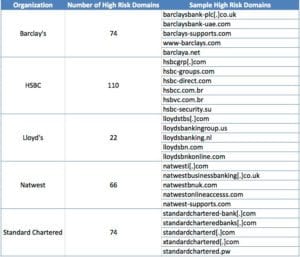
The DomainTools research team analysed domains mimicking Barclays, HSBC, Natwest, Lloyd’s and Standard Chartered using its PhishEye tool. PhishEye allows users to search for existing and new domains that spoof legitimate brand, product, organization, or other names. In total, there were 324 domains identified as high risk that contained the banks’ brand names. Some examples include:
- natwesti[.]com
- natwestbusinessbanking[.]uk
- lloydstbs[.]com
- hsbcgrp[.]com
- bhsbc[.]com
- barclaysbank-plc[.]uk
- wealthbarclays[.]uk
- standardchartered-bank[.]com
- standardcharteredbanks[.]com
- standardcharterd[.]com
- xtandardchartered[.]com
Kyle Wilhoit, senior security researcher at DomainTools said, “Imitation has long been thought to be the sincerest form of flattery, but not when it comes to domains. While domain squatters of the past were mostly trying to profit from the domain itself, these days they’re often sophisticated cybercriminals using the spoofed domain names for more malicious endeavours.”
He explained how there are patterns to be found in these types of domains – “Many will simply add a letter to a brand name, such as Domaintoools.com, while others will add letters or an entire word such as ‘login’ to either side of a brand name. Users should remember to carefully inspect every domain they are clicking on or entering in their browser. Also, ensure you are watching redirects when you are going from site to site.”
“Brands can and should start monitoring for fraudulent domain name registrations and defensively register their own typo variants. It is better to lock down typo domains than to leave them available to someone else and at an average of £12 per year per domain, this is a relatively cheap insurance policy.” Wilhoit concluded.
DomainTools offers top tips for consumers to avoid falling foul of a spoof website:
- Check for extra added letters in the domain, such as Yahooo[.]com
- Check for dashes in the domain name, such as Domain-tools[.]com
- Look out for ‘rn’ disguised as an ‘m’, such as com versus modern.com
- Check for reversed letters, such as Domiantools[.]com
- A plural or singular form of the domain, such as Domaintool[.]com
The full research is available on the Domain Tools blog: http://blog.domaintools.com/2017/05/up-to-your-gills-in-phishing-attacks-this-research-may-help
Notes to editor:
- The brand domains were monitored from the 27th– 31st March 2017
- DomainTools generates risk scores according to a proprietary algorithm that assigns a “guilt by association” score to the domain based on a number of factors. Like friends, domains tend to cluster with similarly good or bad domains and such patterns are highly predictive of whether a new domain is going to be good or bad.
- The full results are available upon request
[su_box title=”About DomainTools” style=”noise” box_color=”#336588″][short_info id=’61027′ desc=”true” all=”false”][/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



