Phishing emails with subject lines related to vaccines now being used to trick recipients into downloading malicious Windows, Word and Excel files designed to steal a person’s credentials
- Number of new, vaccine-related coronavirus domains double in June and July 2020
- 1 out of every 25 malicious coronavirus-related websites’ landing pages is vaccine-related
- Email (82%) dominates web (18%) as the attack-vector of choice for malicious files in the last 30 days
Researchers at Check Point have observed a new trend of phishing emails exploiting interest in coronavirus vaccines. The primary attack method is email, which constituted 82% of all attack vectors for malicious files in the last 30 days. In these hacking campaigns, hackers craft email subject-lines that incorporate deceptive coronavirus vaccine-related content, while simultaneously lacing malicious links into the email bodies.
After clicking the malicious link, recipients inadvertently download a malicious file, typically in file type forms of .exe, .xls or .doc. Two examples found by Check Point researchers are.
Subject: Urgent Information Letter: Covid-19 New Approved Vaccines
In the first example, Check Point researchers cite a malspam campaign they caught with the email subject “URGENT INFORMATION LETTER: COVID-19 NEW APPROVED VACCINES”. The respective emails delivered malicious .EXE files with the name “Download_Covid 19 New approved vaccines.23.07.2020.exe”, that when clicked on, installs an InfoStealer capable of gathering information, such as login information, usernames and passwords from the user’s computer.
Subject: UK coronavirus vaccine effort is progressing
In the second example, Check Point researchers point to an email phishing campaign that sends the subject-line: “UK coronavirus vaccine effort is progressing badly appropriate, recruiting consequence and elder adults”. The mail contains a malicious link “surgicaltoll\.com/vy2g4b\.html”. Further investigation revealed that it was used to redirect traffic to a medical phishing website; “thelifestillgoeson[.]su”, which was trying to imitate a legitimate Canadian pharmacy.
Coronavirus-related attacks are dropping
Although the number of general cyber-attacks remained high in July, the number of coronavirus-related attacks has dropped significantly. In July, Check Point researchers witnessed an weekly average of 61,000 coronavirus-related attacks, a decrease of over 50% when compared to the weekly average of 130,000 attacks in June.
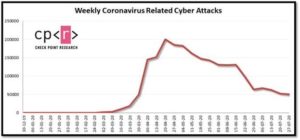
Omer Dembinsky, Data Manager at Check Point said: “Lately, we’re seeing a clear trend adopted by hackers: deceive the masses by using their interest in coronavirus vaccines. Most of the campaigns involve a person’s inbox, which is concerning. Over 80% of attacks against organizations start from a malicious email. Email is the first link in a chain of attacks. Since email attacks usually involve the human factor, employees’ email inboxes are an organization’s weakest link. Closing this security gap requires protections against various threat vectors: phishing, malware, data theft and account-takeover. I strongly urge everyone to closely read the subject lines of emails coming in. If it has the word “vaccine” in it, think twice. Chances are that you are the threshold of being tricked into giving up your most sensitive, most private information.”
How to Protect Yourself
- Check the full email address on any message and be alert to hyperlinks that may contain misspellings of the actual domain name.
- Do not supply login credentials or personal information in response to a text or email.
- Protect mobile and endpoint browsing with advanced cyber security solutions, which prevent browsing to phishing web sites, whether known or unknown
- Use two-factor authentication to verify any change to account information or wire instructions.
- Continuously educate your end users: whenever irreversible actions such as money transfers are conducted, details of the transaction must be verified in additional means such as voice communication and must not exclusively rely on information from email correspondence.
- Regularly monitor financial accounts.
- Keep all software and systems up to date.
- Make sure you are using an email security solution that blocks sophisticated phishing attacks like Business Email Compromise, in order to prevent them from reaching employees mailboxes to begin with