The year is circa 1995; Major League Baseball players end a 232-day strike, Windows 95 is released by Microsoft, JavaScript is first introduced and deployed, the Grateful Dead announce their break-up, and Toy Story became the first ever wholly computer generated movie to be released. Did you also know that in 1995 the average inpatient medical record was accessed and viewed by at least 150 people during a typical five-day hospital stay by nursing staff, to receptionists to x-ray technicians?
Think about this; 150 viewers in 1995! That number has to have quadrupled since then to at least 600 health professionals today with health information exchanges, business associates, and electronic health records (EHI/EPHI) being the healthcare industry norm. Furthermore, there is no end in sight as the number of record viewers continues to grow as medical coders, medical billers, insurance companies, and even quality control personnel all require access to medical patient information of some degree in order to conduct their day-to-day work associated with healthcare payment and operations. To be honest; these are only just a few of the many legitimate reasons around why a patient’s medical records are viewed and in that same light why a patient’s medical information could become part of an information breach.
Securing, protecting, and ensuring health information is private has become an ever increasing challenge with fiscal penalties for failure increasing almost at the same rate EHI and EPHI data is expanding. Adherence to HIPAA must not be focused solely on a “point-in-time” that aligns with the organizations audit and compliance review cycle. Therefore, Healthcare organizations must embrace HIPAA as an on-going, full-time effort that requires a combined program of resources and compliance tools to ensure success. This allows institutions to avoid penalties and remediation costs that aren’t budgeted for.
For example: on the black market a stolen social security card costs one dollar while a stolen medical record is worth $50. Healthcare information is ripe for an information breach due to the fact that it allows a fraudster the ability to take over the victim’s identity in its entirety.
Let’s look at some recent HIPAA violations that have materialized in fines:
– CIGNET → fine: $4,300,000
– Concentra → fine: $1,725,220
– Alaska Department of Health and Human Services → fine: $1,700,000
– WellPoint → fine: $1,700,000
– Blue Cross Blue Shield of Tennessee → fine: $1,500,000
– Massachusetts Eye and Ear Infirmary and Massachusetts
– Eye and Ear Associates → fine: $1,500,000
– Affinity Health Plan → fine: $1,215,780
– South Shore Hospital → fine: $750,000
– Idaho State University → fine: $400,000
– Shasta Regional Medical Center → fine: $275,000
– Phoenix Cardiac Surgery → fine: $100,000
– The Hospice of Northern Idaho → fine: $50,000
Source: U.S. Dept. of Health & Human Services (HHS), Case Examples and Resolution Agreements
Below is a slide I recently developed that demonstrates the costs of remediation to an organization that experiences a breach:
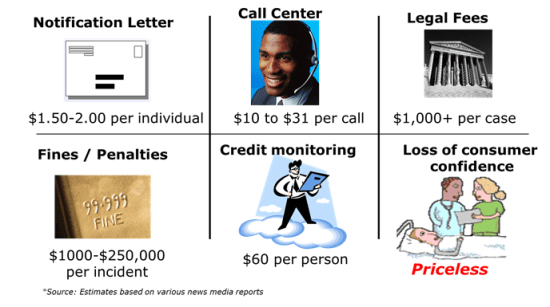
The digital age is driving new restrictions on using Personal Health Information (PHI) within Healthcare organizations. HHS Secretary Kathleen Sebelius recently emphasized that “…much has changed in healthcare since HIPAA was enacted over 15 years ago…” and that the “…new rules associated with PHI/EPHI data will help protect patient privacy and safeguard patients’ health information in an ever-expanding digital age”.
Prevention is still the best approach for reducing the risk of information breach and ensuring your organization is HIPAA compliant. The human error factor of security breaches can only truly be solved through educating and re-educating time and time again the organizational resources that interact with sensitive data aligned with HIPAA. Prevention at its core isn’t a one and done concept; it must become part of your organizations DNA.
By Kyle Kennedy
 Kyle Kennedy is STEALTHbits Technologies’ Chief Technology Officer. With nearly 20 years of experience in the Information Technology field, over a decade of which he focused on Enterprise Security Architecture, Identity & Access Management, and Business Process Management, Kyle has been able to lead large, complex organizations by efficiently mapping business processes to technology solutions. As the former Vice President of Business Development at Pontis Research and Global Director – Directory Services, Identity Services and Enterprise Security Architecture in the Corporate Information Technology organization at ADP, Kyle brings personal, real-world experience in facing the challenges STEALTHbits’ customers encounter daily and the knowledge of how to navigate the hurdles that present themselves along the way. Kyle holds a Bachelor’s degree in Sociology from California State University, Hayward, and a Masters of Business Administration degree from Kaplan University. Kyle is also completing his Masters of Homeland Security and Emergency Management degree.
Kyle Kennedy is STEALTHbits Technologies’ Chief Technology Officer. With nearly 20 years of experience in the Information Technology field, over a decade of which he focused on Enterprise Security Architecture, Identity & Access Management, and Business Process Management, Kyle has been able to lead large, complex organizations by efficiently mapping business processes to technology solutions. As the former Vice President of Business Development at Pontis Research and Global Director – Directory Services, Identity Services and Enterprise Security Architecture in the Corporate Information Technology organization at ADP, Kyle brings personal, real-world experience in facing the challenges STEALTHbits’ customers encounter daily and the knowledge of how to navigate the hurdles that present themselves along the way. Kyle holds a Bachelor’s degree in Sociology from California State University, Hayward, and a Masters of Business Administration degree from Kaplan University. Kyle is also completing his Masters of Homeland Security and Emergency Management degree.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



