From tooth brushes that can schedule checkups with dentists to yoga mats that can analyze poses in real-time, one thing is abundantly clear—we are entering a new era of connected devices. Collectively referred to as the Internet of Things (IoT), Gartner predicts that the number of Internet-connected devices will rise to more than 25 billion by the year 2020. At the International Consumer Electronics Show (CES) in January 2015, 3,000 companies launched more than 20,000 new products.
But IoT also introduces new security risks. Many in the security industry are wondering if the promise of IoT can be realized if IoT technology providers continue to treat security as an afterthought—and if so, at what cost? You have reason to worry as well.
By now this dirty little secret is out, really out. An IoT security breach has hit the automobile world with a bang. What was once considered science fiction is now reality. In fact, it’s so much of a reality that Chrysler has recalled 1.4 million vehicles for an IoT “bug”. So just what is the problem and how can it be solved?
The problem: In any modern car, there is a series of increasingly powerful computers all connected to each other on several networks. These networks are consolidating, so there are connections among all information systems, such as satellite navigation, Radio Head Unit, controls systems (ECU, Transmission), and safety features (ABS Brakes, 4WD, Tire pressure sensors, lights). They are all increasingly interwoven with each other. When you add cellular, WiFi, Bluetooth, NFC — and any number of other connections outside the car — you have now moved from having the old, standard access to a car — via the diagnostic port in the dash — to a connected wireless machine that can be hacked, possibly from anywhere.
Basically, the modern car has become a datacenter on wheels, but without the perimeter defenses that have been built into the traditional data center over the last 30 years; not to mention that we know even these are not exactly secure. In other words, security has been left to the individual components in many cases, sometimes relying on basic hardware authentication, but rarely has anyone thought about the interaction of thousands of lines of software code in these components.
The problem must be addressed by a more holistic security approach, which involves more than hardware security, which, while strong, can’t run an entire ECU or ABS Braking system inside the secure chip. Also, these things have to communicate outside the perimeter at some point in order to function at all.
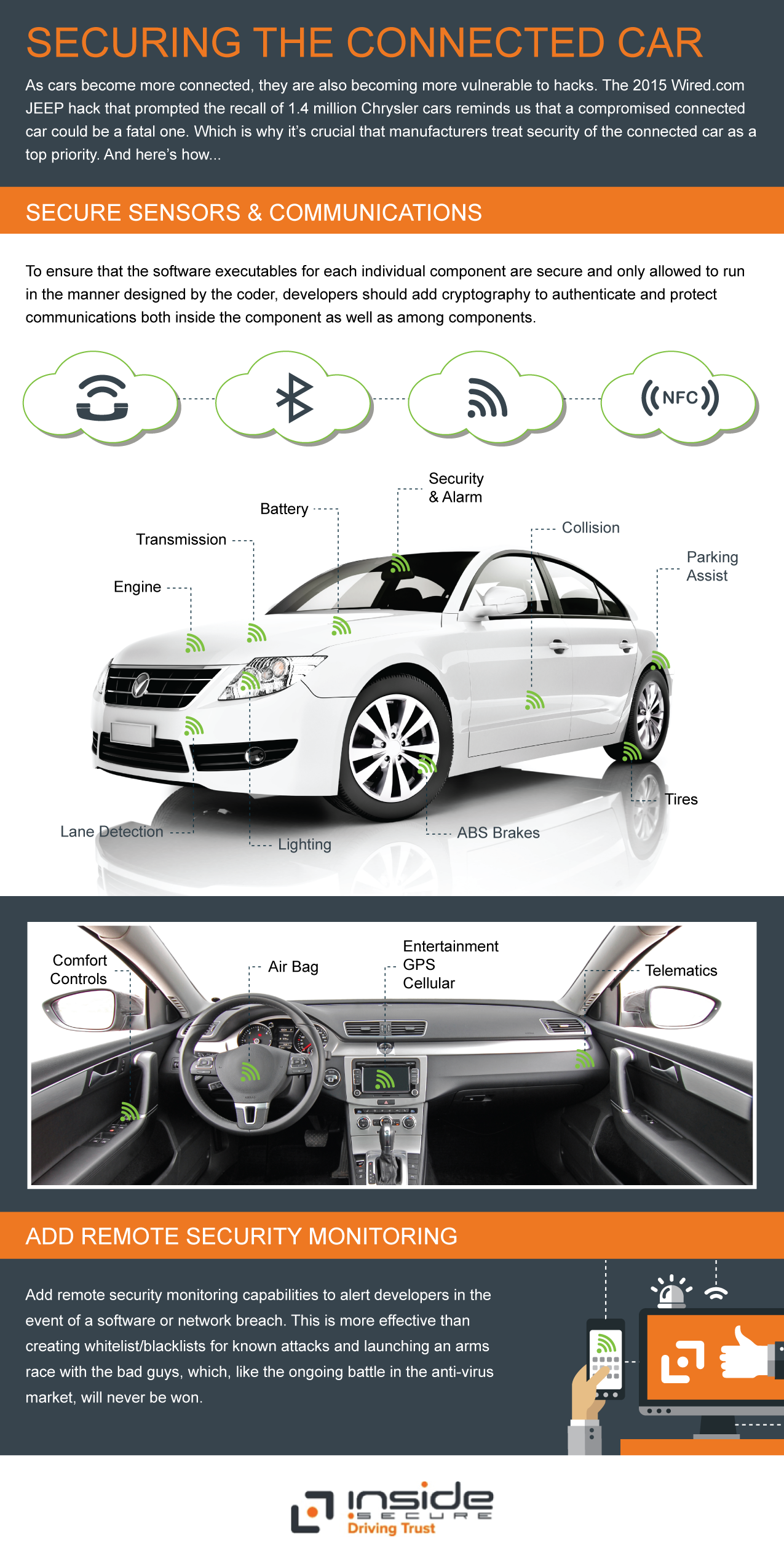 What to do: Instead of attempting the very expensive or nearly impossible task of starting from scratch, car manufacturers must ensure that all the individual executables that are written for each of the devices in the car, including the entertainment system, are secure.
What to do: Instead of attempting the very expensive or nearly impossible task of starting from scratch, car manufacturers must ensure that all the individual executables that are written for each of the devices in the car, including the entertainment system, are secure.
- Add cryptography to ensure that communications and authentication between software inside a device and among devices are authenticated (signed), and ensure that software is only allowed to run in the manner designed by the coder.
- Add in remote security monitoring to alert if there is a software or network breach. (Note: This means you do not have to rely on trying to create white-list/black-lists for known attacks because the bad guys are always a step or two ahead of developers — and it’s an arms race that has never yet been won in anti-virus markets.
In other words, the car network has to be treated in the way that the mobile payment folks are treating mobile phones, as a potentially hostile environment, and act accordingly. Developers must anticipate and bring best-fit security to the fast growing Internet of Things market by addressing the need for authentication, secure communication, information protection and user privacy.[su_box title=”About Andrew McLennan” style=”noise” box_color=”#336588″] Andrew McLennan serves as Senior Vice President, Mobile Security Division, INSIDE Secure, and is an experienced entrepreneur and start-up CEO, having co-founded Metaforic. He helped the company gain industry acclaim for its mobile security infrastructure and white-box cryptography. Before Metaforic, Andrew headed up several innovative start-up companies like Slam Games, DC Studios, and Steel Monkeys, showcasing his leadership and business development skills that enabled these upstart companies to grow into profitable, successful businesses. Andrew received his Bachelor of Engineering in Mechanical Engineering and Aerodynamics from Strathclyde University in Glasgow, United Kingdom.[/su_box]
Andrew McLennan serves as Senior Vice President, Mobile Security Division, INSIDE Secure, and is an experienced entrepreneur and start-up CEO, having co-founded Metaforic. He helped the company gain industry acclaim for its mobile security infrastructure and white-box cryptography. Before Metaforic, Andrew headed up several innovative start-up companies like Slam Games, DC Studios, and Steel Monkeys, showcasing his leadership and business development skills that enabled these upstart companies to grow into profitable, successful businesses. Andrew received his Bachelor of Engineering in Mechanical Engineering and Aerodynamics from Strathclyde University in Glasgow, United Kingdom.[/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



