Pandemic-resistant Teleworking – We started to use this phrase five years ago as a use case of Expanded Password System that provides ‘hard-to-forget’, ‘hard-to-break’ and ‘panic-proof’ digital identity authentication platform, though it was no more than a hypothetical statement at that time.
We now witness the pandemic assaulting us before we get ready. We were unfortunately late for the current Covid-19. When, not if, the next one hits us in 5, 10 or 20 years ahead, humans will probably be yet more heavily dependent on Digital Identity. We or our successors will hopefully be able to make a meaningful contribution to the safe and resilient cyber life.
While waiting to see what will be happening in the pandemic-overwhelmed cyberspace, we will be steadily progressing the expanded password system in order to make it readily available to all the global citizens.
The huge merits of expanding the password system for making use of our image memory, especially emotion-colored episodic image memory, as the secret credential for digital identity was closely discussed in my earlier article “Digital Identity and Episodic Memory”.
The theory of expanded password system is not a hypothesis. The versatile practicability is demonstrated by the 5-year use by 140, 000 online shoppers, the 6-year use by 1,200 employees for a corporate network and the 7-year trouble-free defense use by army soldiers.
The solid theory is endorsed by OASIS recognition as a standard candidate, publishing by Taylor & Francis, selection as a finalist by Finance Data and Technology Association for ‘FDATA Open Finance Summit and Awards 2019’ and adoption by AFCEA for ‘2020 Solution Review Problem Sets’.
Below are the subjects that we have discussed since the last article was published last autumn.
Authenticators for Identity Assurance
‘Easy-to-Remember’ is one thing. ‘Hard-to-Forget’ is another.
Publication by Taylor & Francis
Shortlisted by Financial Data and Technology Association
Video Interview by Risk Group
Rapid Increase in Defense Use
Selection by Armed Forces Communications and Electronics Association
What does ‘probabilistic authenticators’ achieve in cyberspace?
Alternative Way of Deploying Two-Factor Authentication
Issues of Shoulder Surfing & Low Entropy
High-Security Accounts
Computing Power for Secret Credentials
Future Society enabled by Expanded Password System
< Authenticators for Identity Assurance >
It makes no sense to compare the security of a strong or silly password with that of a poorly or wisely deployed physical token. Nobody can have the criteria for a meaningful comparison of the merits between ‘knife, fork and spoon’.
All that can be said about different authenticators are
- Secret credentials, say, the likes of passwords, are absolutely indispensable, without which identity assurance would be a disaster
- Two-factor authentication made of passwords and tokens provides a higher security than a single-factor authentication of passwords or tokens.
- Two-factor authentication made of biometrics and a password brings down the security to the level lower than a password-alone authentication.
- Passwords are the last resort in such emergencies where we are naked and injured
- We could consider expanding the password system to accept both images and texts to drastically expand the scope of secret credentials.
‘Easy-to-Remember’ is one thing. ‘Hard-to-Forget’ is another.
“Images are easy to remember” – This observation has been known for many decades. It is not what we advocate.
What we advocate is that ‘images of our emotion-colored episodic memory’ is ‘Hard to Forget’ to the extent that it is ‘Panic-Proof’.
Images of toys, dolls, dogs and cats, for example, that our children used to love for years would jump into our eye even when we are placed in heavy pressure and caught in severe panic.
This feature makes the expanded password system deployable in any demanding environments for any demanding use cases, with teleworking in pandemic situations included.
Publication by Taylor & Francis
In September 2019, Taylor & Francis in UK published “Digital Identity and Our Remembrance” on its EDPAC (EDP Audit, Control, and Security). I deployed the following discussion.
Assumption: The gains of cyber age would turn against us if connected computers were placed under bad guys’ control. Reliable digital identity is the key to keep off bad guys.
- Secret credentials are absolutely necessary for digital identity in democratic societies.
- The text password, which is a section of the secret credentials, is known to be too hard to manage.
- We could look for something other than the text password as the valid secret credential.
What can be simpler and plainer than this transparent logic? Perhaps only except when being distracted and blinded by vested interests and sunk costs.
Shortlisted by Financial Data and Technology Association
On 18/Oct/2019 we were suddenly invited to present our proposition even though we are not a FDATA member nor related with them in any way. The proposition was submitted on 24/Oct and I was at the Edinburgh summit on 4-5/Dec to receive the honor of being selected as one of the three finalists. It was a dazzlingly rapid development.
Here is a copy of the article “Proposition on How to Build Sustainable Digital Identity Platform” that was shortlisted in the category of “Best innovation in security management – Who has done the most to protect consumer data” for “FDATA Global Open Finance Summit & Awards 2019”.
Video Interview by Risk Group LLC
The writer was interviewed at the end of January 2020 for Risk Roundup about the big merits of making use of our episodic image memory for digital identity. The interview titled “Expanded Password System” lasts about one hour.
Rapid Increase in Defense Use
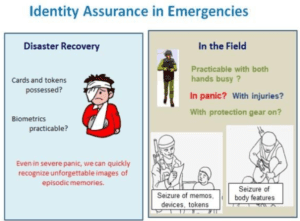
As for the versatile practicability of Expanded Password System, we now can refer to the trouble-free military use in the most demanding environment, with the users having increased 10-fold over the 7-year period from 2013 till now and set to increase further.
What is practicable in the most demanding environment for the most demanding application can be easily practiced in everyday environments for everyday applications; the reverse is not true, though.
Such an authentication system that copes with the panicky situations can be operated for all the everyday applications, too, as a stand-alone authenticator, as a factor of multi-factor schemes and as the master password of ID federation schemes.
Selection by Armed Forces Communications and Electronics Association
AFCEA called for propositions for ‘2020 Solution Review Problem Sets’ which was intended to answer to U.S. Army Chief Information Officer who is seeking solutions to emerging or existing challenges.
We submitted an abstract of our proposition for Item #3 and were notified in early March 2020 that our abstract is kept on-file as a backup and will be included in the compendium of the abstracts that is made available to CIO/G6 leadership.

What does ‘probabilistic authenticators’ achieve in cyberspace?
A big question is often missing in the discussions about the deterministic authenticators (passwords and tokens) and probabilistic authenticators (biometrics); Are the users to blame when the login fails?’
When the user fails to feed a correct password or present a correct token, the user would be to blame. Well, when the sensor fails to get the user’s body features and behaviors authenticated, would the user be to blame?
Where the rejected users are solely to blame, their login would be justifiably denied. On the other hand, where the rejected users are not solely to blame, they should be given a fallback measure with which they can access what they must be able to access. In cyberspace, passwords/PINs are the fallback measures for the self-rescue in most cases.
Where biometrics is used together with a default/fallback password/PIN in a ‘two-entrance’ deployment, we will see the security getting brought down to the level lower than a password/PIN-only authentication. It is, as it were, a below-one factor authentication.

This is what the probabilistic biometrics achieves in cyber space. Criminals will benefit.
Alternative Way of Deploying Two-Factor Authentication
Using two factors together does not always bring higher security.
Higher security is obtained when two factors are used in ‘two-layer’ deployment at the sacrifice of convenience, while better convenience is obtained when two factors are used in ‘two-entrance’ deployment at the sacrifice of security.

We must be careful not to mix up these two ways of deployments that have the exactly opposite security effects lest a serious false sense of security should be created and spread. Here is the updated version of “Negative Security Effect of Biometrics Deployed in Cyberspace”
Issues of Shoulder Surfing & Low Entropy
We have been advocating Expanded Password System that accepts images as well as texts from 2001. We have since kept hearing our proposition blamed for two major ‘drawbacks’ of using images – Shoulder Surfing and Low Entropy. So many people are still misguided to take it for granted as if it were the case.
The fact is that threats of shoulder surfing can be mitigated with ease by some simple techniques – images to get shrunk prior to tapping, texts allocated to images for quiet typing and so on at the end of developers, with the simplest solution being just looking around you before tapping the images at the end of users.
Another seemingly serious problem of low entropy can be eliminated at the end of developers without giving any extra burden on users.
High-Security Accounts
Data-separation, with which images stay in the user’s device while the hashed credentials of extremely high entropy is stored on the authentication server, will help.
Bad guys would have to steal the user’s device and find the correct images quickly before the accounts get blocked. It would be next to impossible with the high-security version of Expanded Password System that comes with such functions as follows.
- Distinguishing certain errors that we are unlikely to commit from the errors that we are apt to make often. This function is expected to screen out bad guys accurately and quickly, while largely mitigating the user’s stress.
- Quietly sending a duress code/signal that is practicable in a panicky situation. There have been a number of suggestions of duress code, but the earlier ones have all been no more than a pipe dream because they are not practicable when we are caught in panic, in such a situation as at gun/knife point. Only the memorable images associated with our unforgettable episodic memory enables the practicable duress code.
Computing Power for Secret Credentials
When the computing power was very limited, we were only able to use texts, namely, characters and numbers, as the secret credential for identity authentication. Now that the computing power is no longer so limited, we could accept non-text credentials such as visual images, audio sounds and tactile sensations where they contribute to better security and/or better usability.
Humans acquired the ability of reading, writing and remembering texts quite recently – a few hundred years ago for the majority of our ancestors. On the other hand, our ability of seeing, watching, finding, distinguishing and remembering visual objects dates back to 5 hundred million years ago. This ability is solidly inscribed at the deep layer of the brains for all of us.
Separately, we know that cognitive science supports that our episodic memory, much of which is visual, is the core of humans’ internal identity.
Future Society enabled by Expanded Password System
Textual passwords could suffice two decades ago when computing powers were still limited, but the exponentially accelerating computing powers have now made the textual passwords too vulnerable for many of the cyber activities. The same computing powers are, however, now enabling us to handle images and making more and more of our digital dreams come true, some of which are listed below.
– Electronic Money & Crypto-Currency
– Hands-Free Payment & Empty-Handed Shopping
– ICT-assisted Disaster Prevention, Rescue & Recovery
– Electronic Healthcare & Tele-Medicine to support terminal care in homes
– Pandemic-resistant Teleworking
– Hands-Free Operation of Wearable Computing
– User-Friendlier Humanoid Robots
– Safer Internet of Things
– More effective Defense & Law Enforcement
all of which would be the pie in the sky where there is no reliable identity assurance.
Would it be possible to not make use of our own emotion-colored episodic image memory for our identity assurance?
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.


