July’s Advance Notice by Microsoft has just arrived. This month, Microsoft is publishing six bulletins in July, affecting all versions of Internet Explorer, Windows and one server components. Two bulletins are rated “critical,”, as they allow for Remote Code Execution (RCE), three are rated “important” as they allow for elevation of privilege inside on Windows.
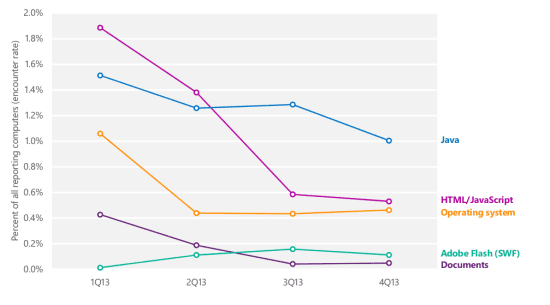
The most critical patch to consider is Bulletin 1 is for all versions of Internet Explorer (IE), all the way from Internet Explorer 6, but only supported on Windows Server 2003 since XP has been retired, to the newest IE 11 on Windows 8.1 and R. This patch should be top of your list, since most attacks involve your web browser in some way. Take a look at the most recent numbers in Microsoft SIR report v16, which illustrate clearly that web- based attacks, which include Java and Adobe Flash are the most common.
Bulletin 2 is a critical update for Windows and all desktop versions of Vista, WIndows 7, 8 and RT are affected. On the server side all but the the oldest Windows server 2003 are affected. The update will require a reboot, which is something to include in your planning, especially on the server side.
Bulletin 3, 4, and 5 are all elevation of privilege vulnerabilities in Windows. They are affect all versions of Windows. They are local vulnerabilities, i.e they cannot be used to achieve code execution remotely through the network, but require that the attacker already haves a presence on the targeted machine as a normal or standard user.
Exploits for these types of vulnerabilities are part of the toolkit of any attacker as they are extremely useful, when the attackers gets an account on the machine, say through stolen credentials. In any practical scenario, the attacker then wants to assure continued control of the machine and will need to become administrator of the machine to install their controlling malware. This is where these vulnerabilities come in – we consider these extremely important to fix to help frustrate or slow down attackers once they are on the target machine.
Lastly, Bulletin 6 is a Denial of Service vulnerability in the Service Bus for Windows. The Service Bus is a newer component of Windows in use in the Windows Azure environment for the development of loosely coupled applications. In our estimate few companies will have installed that component and on Azure, Microsoft will take of the patching for you.
Later Also this month Oracle is publishing their Critical Patch Update (CPU) July 2014. It is expected to come out on July 15 and typically contains fixes for hundreds of vulnerabilities. How applicable the patches are for your organization depends on your software inventory, but at least the update for Java will be important for most organizations.
Please stay tuned to this blog for next week’s release and further updates from Oracle.
By Wolfgang Kandek, CTO of Qualys, Inc.
About Qualys, Inc.
 The Qualys Cloud Platform and integrated suite of solutions helps businesses simplify security operations and lower the cost of compliance by delivering critical security intelligence on demand and automating the full spectrum of auditing, compliance and protection for IT systems and web applications.
The Qualys Cloud Platform and integrated suite of solutions helps businesses simplify security operations and lower the cost of compliance by delivering critical security intelligence on demand and automating the full spectrum of auditing, compliance and protection for IT systems and web applications.
Used by more than 6,700 customers in over 100 countries, including a majority of the Forbes Global 100, the Qualys Cloud Platform performs more than 1 billion IP scans/audits a year resulting in over 400 billion security events.Founded in 1999, Qualys has established strategic partnerships with leading managed service providers and consulting organizations including BT, Dell SecureWorks, Fujitsu, IBM, NTT, Symantec, Verizon, and Wipro. The company is also a founding member of the Council on CyberSecurity and the Cloud Security Alliance (CSA).
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.