All companies have assets. They help them generate profit and hence require protection. Information security professionals help companies to assess and manage risk to these assets and make sure that cost-effective and appropriate response strategies are chosen to address these risks.
Enterprises in turn may decide to implement mitigation strategies in the form of technical, procedural, physical or legal controls. These implementations would have a defined start and end date and would require resources and hence a project rather than an operational activity.
However, such implementations have their own project risks. According to the Guide to the Project Management Body of Knowledge, risk is an uncertain event or condition that, if it occurs, has a positive or negative effect on one or more project objectives.
The project risk management process is similar to the information security risk management and consists of four stages:
1. Identification – Log risk, agree and assign an owner
2. Analysis – An owner assesses risk and sets probability and impact
3. Monitoring and Control – An on-going process of tracking identified risks, monitoring residual risks, identifying new risks, executing risk response plans and evaluating their effectiveness throughout programme
4. Response planning – What response will be taken to manage the risk
It is a good practice to involve your team and all relevant stakeholders during the project planning stage to identify the risks and populate the risk log
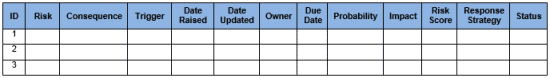
o ID – assign a number (e.g. 1, 2, 3)
o Risk– a specific definition of the risk event.
o Consequence –what effect each entry has on the business/change programme/projects
o Trigger – an event which signals the risk occurrence
o Date Raised – when the risk was initially raised
o Date Updated – when the risk was updated
o Owner – a person responsible for monitoring risk event, notifying team, and executing risk response
o Due Date – when will the actions be completed
o Probability (on a scale 1-5) – likelihood of the risk occurring
o Impact (on a scale 1-5) – impact if the risk does occur
o Risk Score – probability x Impact
o Response Strategy – a specific agreed actions which will take place to manage the risk (Avoid, Transfer, Mitigate, Accept))
o Current Status – indicate risk status (Red, Amber, Green, Closed)
During the execution of the project, the risk log should be continuously revised and kept up to date to ensure that project issues, risks and mitigating actions are fully and formally assessed and managed throughout the project lifecycle
Author’s bio:
Leron Zinatullin
 Business-oriented information security professional with several years of proven experience in architecture design and project management. Extensive knowledge and practical experience pertaining to analysing and solving governance, risk, compliance, information security and privacy issues.
Business-oriented information security professional with several years of proven experience in architecture design and project management. Extensive knowledge and practical experience pertaining to analysing and solving governance, risk, compliance, information security and privacy issues.
Website: http://zinatullin.com/
Twitter: @le_rond
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



