Enterprises across the world are becoming more and more aware of security-related issues and their impact on the business, making them increasingly willing to address them. Although they are open to listening to the security professionals’ advice, the language the business speaks is different.
It is important for security specialists to understand the business requirements and communicate the value of security accordingly. Managing stakeholders and communication is therefore becoming one of the essential skills of the modern security professional.
One should understand that the earlier people are involved in a security project, the easier it is to get their buy-in. It is useful to spend some time on planning the communication prior to a project kick-off.
As a first step to such planning, a stakeholder register could be created capturing the contact information, expectations about the project, level of influence, and other characteristics, as in the table below.
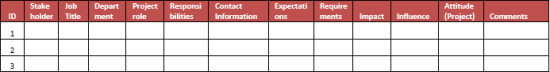
As soon as the stakeholders are identified, a communication management plan should be created. One can engage the stakeholders to identify the best way of communication, its frequency, responsibility and a reason for sending.
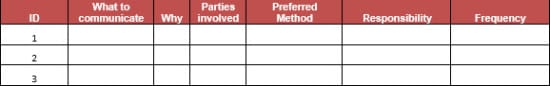
While managing a project, a security professional spends almost all his / her time communicating in various ways. Proper stakeholder engagement and communication planning can make the security-related projects run much smoother. At the end of the day, security professionals are there to help people to make the business more secure. This task can be achieved more easily when people are cooperating with the security professionals rather than trying to sabotage the project.
Author’s bio:
Leron Zinatullin
 Business-oriented information security professional with several years of proven experience in architecture design and project management. Extensive knowledge and practical experience pertaining to analysing and solving governance, risk, compliance, information security and privacy issues.
Business-oriented information security professional with several years of proven experience in architecture design and project management. Extensive knowledge and practical experience pertaining to analysing and solving governance, risk, compliance, information security and privacy issues.
Website: www.zinatullin.com
Twitter: @le_rond
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



