Considering the known-known statistics, we seem to encounter a serious security breach at least once a week – and these are only the events which are notified or discovered. In fact, according to the BreachAware Report issued end July 2023, there were no less than 179,351,301 events involving leaked data, and other such insecurities – which does tend to focus the mind on the exposure that manifests out of, what may only be described a lacklustre cyber defence, which in real terms impact the end user account – AKA People! The question however, which hangs in the air to ponder is why? Given that some of the organisations who have been breached are shiny brands such as British Airways, Easy Jet, and Experian, who one would expect invest heavily in cyber defence to protect their product, and PII they have custodianship over, again another question which hangs in the air is, how can this be?
This last week I was reading up on some past materials I have used over my 35 years in an industry we now call Cyber Security, in which we may encounter those who use the title Cyber Security Expert (AKA operatives who know everything about everything in this vast domain of knowledge). What became very clear when reading back over the previous 35 years was, in comparison to some of the accepted materials of the day, it would seem we may have diluted what were robust Digital Security Skills into texts which seem to avoid the stressful need to appreciate the underlying technical challenges, but instead rely on heavy focus on the subject matter from a Governance, Compliance perspective which at times leans toward achieving some form of evidence skill in the format of a Certification of proven expertise! We may also encounter high level cyber assurance programs which infer that an organisation is robustly secure post performing a high-level review, which may only be described on occasions as a Tick Box exercise. Or maybe there is deep trust in the ISO/IEC 27001 Certification which was found to be adequate on the day of granting the Certificated Status!
As I introduced above, I have been spending some time reading over what may be considered out of date materials such as:
- The DoD Orange Book
- DoD Password Management (April 1985)
- CESG COMPUSEC MANUAL M – Protecting Government Connections to the Internet
- CESG COMUSEC MANUAL N – Vulnerabilities of the TCP/IP Protocol Suite (June 1996)
- CESG MEMORANDUM NO. 7 – Re Use/Disposal of Computer Memory and Magnetic Storage
- CESG INFOSEC MEMORANDUM NO. 13 – Protecting Government Connections
- CESG INFOSEC MEMORANDUM NO. 14 – Public Key Infrastructure
What becomes obvious when reading the now, considered out-of-date documentation sets is, they are full of valuable knowledge and robust technical direction, and are also in the main still as relevant today as they were on their first publication – as opposed to the lite touch of current initiatives such as Cyber Essentials.
The book I pulled from the bookshelf was Computer Security (Third Edition) by John M. Carroll. What is so evident from this comprehensive publication is the depth which the book dives to, which in its 600 pages + covers domains from the Essentials of Computer Security’ through to Physical Security, Line Security, Transmission Security, Cryptography, though to Threat Assessments to mention but a few. However, what is very clear when reading though this comprehensive work is the technical depth covered which provision valuable technical education.
I touched on Certifications which on numerous occasions are mistakenly taken has proof of hands-on expertise. One example which springs to mind is the young Security Professional who held a CSIM (Certified Information Security Manager) Certification who worked for the Co-Operative Bank in Manchester. However, this candidate, whilst holding the proof of skills, did not have the necessary underpin of hands on, or qualified time practicing the fundamentals, and thus the certified status could be considered flawed – whist at the same time it was a trusted credential by the bank – shortly after that engagement, this operative left the bank and the cyber industry to become a Witch Doctor on the sub-continent (seriously) – see below media clip:
‘But it was all getting rather routine and so he opted for something a little different – heading for South Africa, going without sleep for three days, putting himself in a trance and drinking goat’s blood.
Mr x, 32, has given up his suit, laptop, and his office to train as a witchdoctor.’
There is no doubt that Certifications do serve a valid purpose, but I make this statement with the caveat that, they should be considered as part-and-parcel, conjoined with robust level of evidenced technical skills, understanding commensurate with the role such a party is being placed in.
The world of training can also go a long way to building on the required skillset. However, again there are several training bodies both in the UK, and the Middle East who are offering courses with trainers who have had very little pragmatic expectances relating to the world of cyber, along with courses in which the level the cyber defence pragmatism is based on Governance and Compliance – not to mention, flogging standards as the silver bullet route to a secure delivery of the business and related digital assets.
As a conclusion, in my training courses I have delivered over the past decade to hundreds of delegates and students in the UK, Malaysia, Dubai, Saudi Arabia, I have always stressed that there is a need for all elements to work in concert to accommodate the secure perimeter, and related asset security, thus why it is so very important to set a tipping point to provision a balance – see Fig 1 below from my Cyber Security Training Course materials:
Fig 1 – Tipping Point of Security
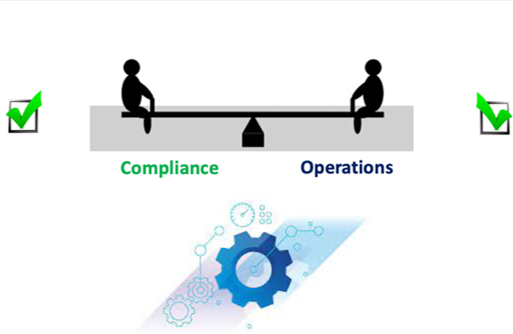
There is absolutely no doubt in my mind that the good guys/gals can combat the age of Digital Adversity and win the fight – the only thing that needs to be done is to take the threat seriously, look back at where we came from and apply a level of defence that is appropriate to the aggression – and maybe, just maybe embrace a little more technical cyber savvy.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



