After multiple reports of massive DDoS attacks using memcached servers were detailed this week by researchers including Imperva and Akamai, a new development involving ransomware demands was also published Thursday by Cybereason.
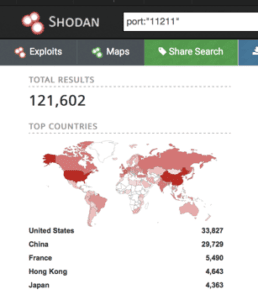
Nick Bilogorskiy, Cybersecurity Strategist at Juniper Network, commented below, and provided a supporting screenshot from the Shodan search engine.
, Cybersecurity Strategist at Juniper Network:
 “It is a pretty clever trick to embed the ransom demand inside the DOS payload. It is also fitting with the times that attackers are asking for Monero rather than Bitcoin because Monero disguises the origin, destination and amount of each transaction, making it more suitable for ransoms.
“It is a pretty clever trick to embed the ransom demand inside the DOS payload. It is also fitting with the times that attackers are asking for Monero rather than Bitcoin because Monero disguises the origin, destination and amount of each transaction, making it more suitable for ransoms.
On Shodan, a search engine for internet connected devices and exposed servers, one could see over 100,000 exposed memcached servers, mostly in the US, China and France. While those are connected to the Internet and not firewalled, memcached DDOS attacks are likely to continue. The amplification factor in memcached reflections is much higher than what we have ever seen before – 50,000 amplification vs 179 amplification factor in a DNS amplified DOS attack.”
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



