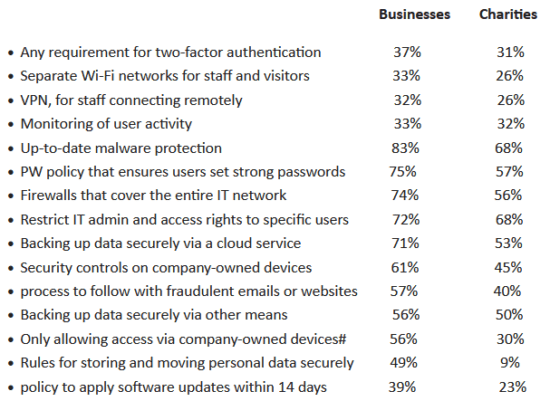
A new study finds that only one third of businesses require MFA access, have separate staff /guest WI-FI or use VPNs for remote workers. The UK government released their Cyber Security Breaches Survey 2022 this week reporting that only around third of organizations follow any of these practices, with the percentage being only slightly higher for businesses vs charity organizations. The report goes on:
“Two-factor authentication was covered for the first time in this year’s survey. Just over a third of businesses (37%) and just under a third of charities (31%), have a requirement for their people to use two-factor authentication when accessing their network, or for applications they use. … Two-factor authentication is noticeably more prevalent among businesses in information and communications (63%). Conversely, fewer than one in five (18%) businesses operating within the food and hospitality sector employ two-factor authentication procedures. It is also relatively under deployed among utilities, production, and manufacturing businesses (28%).”
Percentage of organizations that have the following rules or controls in place
The Cyber Security Breaches Survey is an influential research study for UK cyber resilience, aligning with the National Cyber Strategy. It is primarily used to inform government policy on cyber security, making the UK cyber space a secure place to do business. The study explores the policies, processes, and approaches to cyber security for businesses, charities, and educational institutions. It also considers the different cyber attacks these organizations face, as well as how these organizations are impacted and respond.
The Cyber Security Breaches Survey is an influential research study for UK cyber resilience, aligning with the National Cyber Strategy. It is primarily used to inform government policy on cyber security, making the UK cyber space a secure place to do business. The study explores the policies, processes, and approaches to cyber security for businesses, charities, and educational institutions. It also considers the different cyber attacks these organizations face, as well as how these organizations are impacted and respond.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



