Beckie Neumann, product manager, RiskIQ, a digital threat management leader
To state a few universal truths in Digital Threat Management:
- The Internet is really big and contains a vast number of digital threats.
- Not all threats pose the same level of risk to an organization—some are minor annoyances while others constitute genuine crises for a business.
Despite common knowledge of these facts, practitioners of Digital Threat Management still often find themselves faced with a choice that, in reality, they don’t have to make. A., a comprehensive approach to threat detection at the risk of unleashing a flood of alerts or B., a limited, narrowly focused approach that reduces alerts to a manageable trickle but at the expense of visibility into the big picture and the ability to detect and react to what’s coming tomorrow.
The truth is, it’s not a binary choice. The most effective Digital Threat Management programs don’t just balance the perils of both extremes and learn to live with something in the middle. Instead, they create a third path that optimizes the benefits of each approach. With the right tools in place, casting a wide net doesn’t have to mean biting off more than you can chew or letting important alerts get lost in the noise. Conversely, acknowledging the realistic day-to-day workload your security team can handle doesn’t have to mean putting on blinders and completely ignoring vast swaths of data on potential threats.
The key is leveraging automation to group threats by key risk factors so that security analysts can dedicate their time to issues with the highest impact to the business. By coupling priority-driven filtering and sorting with automated, continuous monitoring of threats, you can both have your cake and eat it too.
RiskIQ’s Digital Threat Management platform is designed to facilitate this third path:
- Gain comprehensive visibility into the state of your organization’s public-facing digital assets as well as third-party owned web, mobile, and social properties unofficially using your brands via dashboards and top-level reports.
- Drill down from the big picture with surgical precision to identify the handful of highest priority items for your team to action at any given time.
- Quickly mitigate high-risk threats with built-in workflow and integrations to free up time for other tasks.
- Continuously monitor all the threats to your organization and automatically track changes in their behavior over time. Pre-existing items that are a low priority today will automatically bubble up towards the top of your team’s queue as monitoring picks up increases in risk severity tomorrow, allowing your team to see and take action on emerging threats as they develop.
The result is that your team uses automatically gathered data about threats to intelligently and efficiently work through alerts according to their current importance to the business, rather than just working through them in the order they were received.
To illustrate this approach in action, I will show how we use our own products at RiskIQ to manage our digital presence, including monitoring for domain threats. The sheer number of suspicious domains and subdomains exploiting brand names out there is one of the biggest challenges for any organization to manage. This problem has grown worse in recent years due to the opening of thousands of new gTLDs, the growth of free and extremely cheap domain registration services, and the increasing popularity of subdomain infringement and attack techniques like domain shadowing . Because of the potentially high volume of alerts, being able to drill down from a large set of candidates to quickly identify which domain threats truly demand your time and attention is crucial.
Logging into our RiskIQ workspace, I see in the dashboard that there are 165 domain threats I have not yet investigated. Clicking on that number takes me to view those domain infringement events.
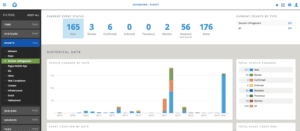
Fig-1 Domain threats in the RiskIQ dashboard
Before I click on any events in the list, I use the quick filters to help me narrow my search to high priority risks. The first attribute I look for is look-a-like domains that are not only registered, but also currently have live website content associated with them, and thus, maybe being used for phishing or other fraudulent purposes.
That filter cuts my list from 165 to 109. I can go further, however, by also excluding generic parking pages from that list. Of the 109 pages that had an http response, only 61 of them resolved to a page with something other than a generic parking page.
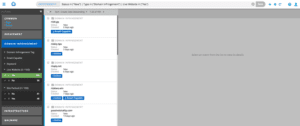
Fig-2 Narrowing it down to “priority risks”
Left with 61 more domains to look at, I quickly check if any of the domains contain my logo in the content of the page, but no domains fit that criterion.
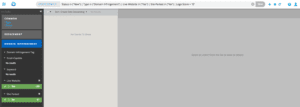
Fig-3 61 pages resolving to something other than a generic parking page
Instead, I open another quick filter on the left to check how many of those domains or hostnames contain an exact match to one of my brand names (as opposed to either an exact match or a close misspelling).
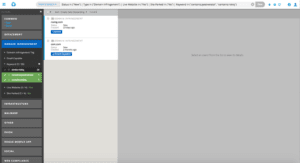
Fig-4 Only my top risks are left
From 165 all the way down to 2 in a couple of clicks—I have now identified my top risks to review.
After I investigate these two threats, I can then move on to other threat groups of interest, including:
- Close misspellings of my brand names in domains that have live, non-parked sites
- Infringing domains that are email-capable and could be used to send email appearing to come from one of my brands in phishing campaigns (even if they are not hosting phishing sites directly on the domain itself)
- Other suspicious but currently unused domains I want to investigate
- Similar domains currently for sale I may want to register defensively to prevent them falling into the wrong hands
RiskIQ continuously detects new infringing domains and subdomains related to my brands and automatically updates and tracks changes to all of them over time. Automated discovery and monitoring give me both top-level visibility into my organization’s overall domain threats risk posture, as well as the context I need about how each domain is being used by the third parties who own it to intelligently prioritize threats and effectively dedicate resources.
Click here to learn more about how RiskIQ can actively defend your organization against digital threats.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



