2014 truly looks like being the year of Office 365. So now seems like a good time to lift the lid on the commercial drivers and the size of the opportunity. That’s why we partnered with Mimecast in January to survey UK IT Managers and Directors about email services and Office 365.
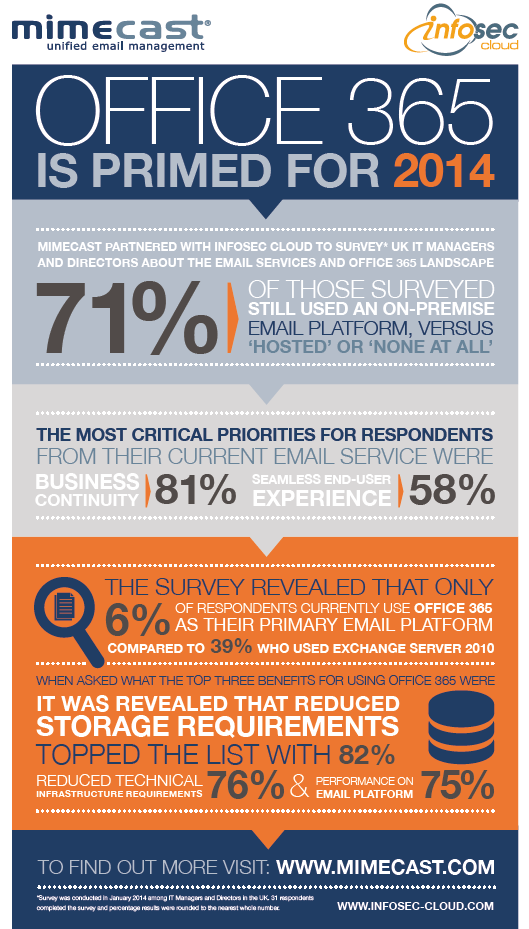
Not all of the results were surprising – the most critical priorities for respondents from their current email service were ‘business continuity’ (81%), followed by ‘seamless end-user experience’ (58%). These are issues which have been top of the list for our customers for many years.
However, what was surprising was 71% of those surveyed still used an on-premise email platform, versus ‘hosted’ or ‘none at all’. It’s a result which highlights size of the cloud email market opportunity as on-premise platforms will migrate to hosted service in the next few years.
How does this migration translate into a growth opportunity for Office 365?
The short answer is ‘massively’ – the survey revealed that only 6% of respondents currently use Office 365 as their primary email platform, compared to 39% who used Exchange Server 2010.
Can we be sure organisations will migrate to Office 365? Well as you’d expect the drivers for Office 365 uptake are excellently matched against the commercial realities facing IT teams…
When asked what the top three benefits for using Office 365 were, it was revealed that reduced ‘storage requirements’ topped the list with 82%, with reduced ‘technical infrastructure requirements’ coming in a close second with 76% and ‘regulatory compliance’ polling at 67%. These are prime areas to really ‘wow’ IT teams.
By adding Mimecast to Office 365 we can seamlessly deliver next generation email services with platinum-standard archiving, storage and security.
As Mimecast recently pointed out on its blog, in the long-term we’re all preparing for an Office 365 world. I, for one, can’t wait to make the most of the seismic changes affecting IT infrastructure as a result.
Pete Sherwood, Managing Director of Infosec Cloud
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.