The goal of a penetration test is to test the security of a computer system by simulating an attack on it. A penetration tester uses the same tools, techniques, and processes as an attacker to detect weaknesses in an organization’s systems and demonstrate their impact.
WHAT IS PENETRATION TESTING?
It is a type of Security Testing designed to identify vulnerabilities, threats and risks that an attacker might exploit in software, a network, or a web application. Penetration testing examines all possible weaknesses in a software application to identify and fix them. Pen tests are also known as penetration testing.
Any system or any data contained within it may be vulnerable to attack by an attacker who can disrupt the system or gain access to its data. During software development and implementation, vulnerabilities are often introduced by accident. These comprise design errors, configuration errors, and bugs in software. Vulnerability Assessment and Penetration Testing (VAPT) are two mechanisms used in Penetration Analysis.
WHY DO WE NEED PENETRATION TESTING?
During penetration testing, a system is tested for its ability to safeguard its networks, applications, endpoints, and users from internal and external threats. Additionally, it aims to protect the system’s controls and prevent unauthorized access to them. Penetration testing is essential for a number of reasons.
- We can use it to determine the environment in which an attacker can exploit a system’s security.
- In performing penetration tests, testers can learn which areas of the application are vulnerable to attack.
- It safeguards the original data and prevents black hat attacks.
- Cyberattacks can damage critical data, which, in turn, results in revenue loss.
- Therefore, one of the rewards you’ll receive is the ability to predict the business’ potential loss.
- Penetrating helps improve existing security standards by informing investment decisions.
TYPES OF PENETRATION TESTING
Penetration tests are typically selected based on scope and whether an internal employee, network administrator or external source is to simulate an attack. Penetration testing can be bifurcated into three categories:
- Black Box Penetration Testing
- White Box Penetration Testing
- Grey Box Penetration Testing
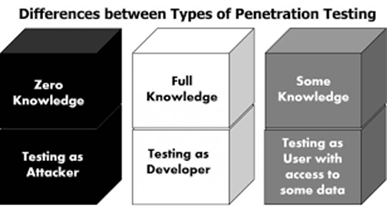
Black Box Penetration Testing:
When a penetration tester conducts black-box testing, he or she will not have any knowledge about the systems being tested. They are responsible for collecting background details on the target systems.
Pros of Black Box Testing
- Before starting, little information is required.
- It behaves in a similar way to an actual attacker. Therefore, it is likely to identify actual issues.
Cons of Black Box Testing
- As a tester, you will not have the same amount of time to plan an attack as a real attacker would
- The test wouldn’t cover all aspects.
- Implementation would be expensive.
- This is not a PCI compliance tool.
While Box Penetration Testing:
A white-box penetration test involves providing the tester with detailed information about the network or system under test, including IP addresses, source code, and OS information.
Pros of White Box Testing
- The black box approach is much less accurate and detailed.
- It is easy to plan with this method.
- Implementation is faster.
Cons of White Box Testing
- Understanding the system and preparing the data for analysis would require considerable time.
- Advanced tool execution would incur additional costs.
Grey Box Penetration Testing:
The tester of grey box penetration tests has partial knowledge of the system. As a result, it can be considered an attack by an external hacker who had accessed the network infrastructure documents of an organization illegitimately.
Pros of Grey Box Testing
- Tests are less expensive than other types.
- Pen testers can reach the same level of coverage as white box testers
Cons of Grey Box Testing
- Pen testing cannot begin until the customer provides information.
STAGES OF PENETRATION TESTING
Penetration testing allows you to proactively identify possible vulnerabilities in security before others do. Despite this, it’s not just about infiltration. Penetration testing involves the following activities:
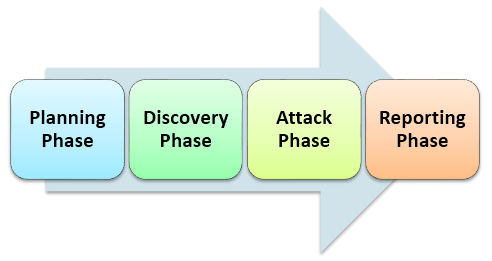
- Planning and Preparation Phase
- Discovery Phase
- Penetration Attempt & Attack Phase
- Reporting and Analysis Phase
1. Planning and Preparation Phase
Pen tests need to be spelled out and executed correctly, which means testers and clients should agree on the goals before the test begins. It will be important to know what types of tests they need to run, how much information and access they will have to begin with, and other details that can ensure the test will be successful.
2. Discovery Phase
Teams perform reconnaissance on their targets during this phase. Identifying firewalls and other connections can be done using technical information like IP addresses. Simple data such as job titles, names, and email addresses can be hugely valuable on the personal side.
3. Penetration Attempt & Attack Phase
As pen testers learn about their targets, they can begin to attempt to infiltrate the network, exploiting vulnerabilities and demonstrating how far they can get into it.
4. Reporting and Analysis Phase
Testing firms should prepare a report which describes every step of the process, including how the system was breached, what security flaws were discovered, and recommendations for resolving the issue.
METHODS OF PENETRATION TESTING
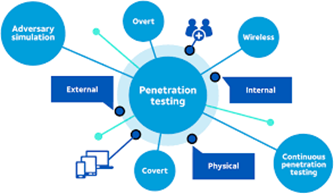
There are mainly 5 types of pen testing:
- External Testing
- Internal Testing
- Blind Testing
- Double-Blind Testing
- Targeted Testing
EXTERNAL TESTING
The assets of a company that are visible on the internet are subject to external penetration tests, such as the company website, email systems, and domain name servers (DNS). Getting access to data and extracting value is the goal.
INTERNAL TESTING
An internal test simulates an attack by a malicious insider by having a tester access to the system behind its firewall. A rogue employee isn’t necessarily simulated here. An employee’s credentials may have been stolen as a result of a phishing attack.
BLIND TESTING
As part of a blind test, the tester is given only the name of the enterprise being tested. An application attack can therefore be viewed in real time by security staff.
DOUBLE-BLIND TESTING
The security personnel in a double blind test do not know the details of the simulated attack. There will be no time to prepare their defenses before the breach is attempted, just as in the real world.
TARGETED TESTING
Security personnel and the tester are working together in this scenario, keeping each other informed about their movements. Security teams benefit from this valuable training exercise as it provides real-time feedback from the hacker’s perspective.
MANUAL PENETRATION TESTING VS. AUTOMATED PENETRATION TESTING
| Manual Penetration Testing | Automated Penetration Testing |
| It requires expert professionals to run the tests. | Less experienced professionals can produce clear reports |
| We can track manual tests by Excel and other simple tools. | Standard tools are available for automation testing. |
| Sample results are different from actual tests. | Results do not vary from tests to tests. |
| Users should be reminded to clean up their memory. | A comprehensive cleanup will be included in Automated Testing. |
BENEFITS OF PENETRATION TESTING
There are 5 biggest benefits of penetration testing:
- A pen test can be used to analyze your IT infrastructure in depth, as well as your ability to defend against external and internal attacks to disrupt your applications, systems, networks, endpoints, or users.
- Performing penetration tests frequently helps prevent and mitigate these expenses.
- You build trust and confidence by scheduling regular penetration tests and taking the necessary steps to ensure data and system security.
- It protects your organization’s image and reputation.
- Maintaining the required security controls demonstrates ongoing due diligence.
CONCLUSION
Testing should act like a real hacker and examine a system or application and also check the code’s security. Security policies that are well-implemented will ensure the effectiveness of penetration tests. It is crucial to have an effective penetration testing policy and methodology. Become an expert at penetration testing with this beginners guide.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



