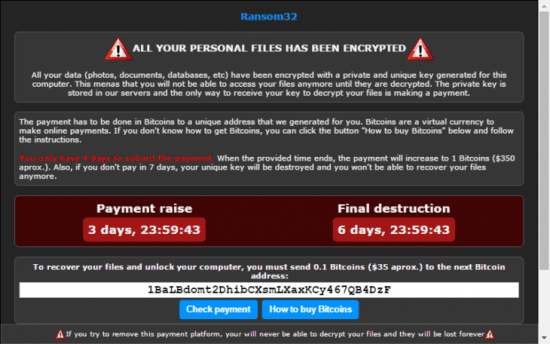
Ransom32 has been discovered which seems to be the first cross-OS ransomware that uses JavaSript to infect users and is coded on top of the NW.js platform. Tim Erlin, director of IT and risk strategy for Tripwire have the following comments on it.
[su_note note_color=”#ffffcc” text_color=”#00000″]Tim Erlin, Director of Security and Product Management at Tripwire :
“Whatever feature or capability makes a language or platform great for developers will also be leveraged by cyber criminals. The self-contained runtime environment and cross-platform nature of NW.js allows a developer to ship code that’s easy to get running on as many systems as possible, and that’s just the kind of feature a malware author needs.
As is the case with most malware, we tend to focus on the interesting technical discussion of the code itself, rather than the much more practical infection vectors. No one wants to read another article about phishing, yet it continues to be a primary method for malware to find its intended target.”[/su_note][su_box title=”About Tripwire” style=”noise” box_color=”#336588″] Tripwire is a leading provider of advanced threat, security and compliance solutions that enable enterprises, service providers and government agencies to confidently detect, prevent and respond to cybersecurity threats. Tripwire solutions are based on high-fidelity asset visibility and deep endpoint intelligence combined with business-context and enable security automation through enterprise integration. Tripwire’s portfolio of enterprise-class security solutions includes configuration and policy management, file integrity monitoring, vulnerability management and log intelligence.[/su_box]
Tripwire is a leading provider of advanced threat, security and compliance solutions that enable enterprises, service providers and government agencies to confidently detect, prevent and respond to cybersecurity threats. Tripwire solutions are based on high-fidelity asset visibility and deep endpoint intelligence combined with business-context and enable security automation through enterprise integration. Tripwire’s portfolio of enterprise-class security solutions includes configuration and policy management, file integrity monitoring, vulnerability management and log intelligence.[/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.