A new initiative aims to revolutionize how companies share and analyze information without compromising anyone’s privacy.
The project is called Reliance Point. It is a collaborative effort between Intel and a research group operating under the guidance of Sridhar Iyengar. Iyengar is the director of security research at Intel Labs. He is known, among other things, for having developed and demonstrated palm-scanning technology back in 2012 as a potential alternative to the use of passwords.
In today’s data-sharing environment, there is little trust amongst end-users. A 2013 Microsoft survey demonstrated as much when out of a pool of 1,000 respondents, 45% stated that they feel they have little or no control over what companies do with their personal information. This lack of control makes users hesitant to share information with one another.
Companies are just as hesitant to pool their data together, even in situations which might effectively serve their mutual interests. This is because businesses are reluctant to trust one another with their valuable proprietary data. And even if they act through an intermediary, they need to be able to trust that mediating actor as well as agree on what analysis will be performed when information is shared.
These are no small challenges.
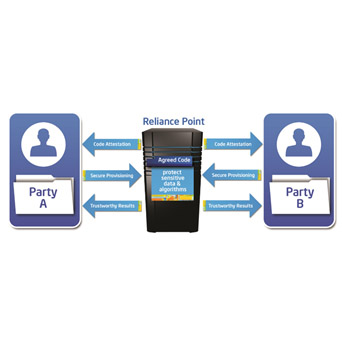
Reliance Point responds to this need for trust in instances of data-sharing. Specifically, Iyengar and Intel’s data center are seeking to develop a secure data locker—a container for users’ personal information which gives the data’s owners the ability to control how and when their information is shared and projected—into which companies can deposit data without worrying about whether it will be compromised.
This data locker works by activating a security chip when booted up. This chip, in turn, analyzes the BIOS—the Basic Input/Output System that is fundamental for all computers in that it contains instructions for how a system should boot up and operate—and makes sure that it has not been tampered with. Once this security test has been cleared, checks will move on to higher levels of software before the entire system can become functional.
At the same time, both companies agree to a specific algorithm that processes their data, while hardware security components help protect this exchange of data.
Even so, there are a number of challenges that must be addressed.
Reliance Point does not resolve the trust issue as much as it relocates it with a third party. Neither company trusts the other more, but they can collaborate with one another because of the security of the project’s data-sharing software. This of course raises the issue of how businesses can agree on a trustworthy third-party actor that can host this software.
Once an intermediary has been chosen, there is also the issue of verifying what a code should do and actually does, and to what extent it reveals information about the input data of either company.
Reliance Point is a step in the right direction. But in relocating the trust issue to secondary channels of interaction, not to mention introducing uncertainty with regards to what an agreed-upon algorithm might do, it is not accomplishing much towards lessening the costs of data-sharing.
David Bisson | @DMBisson
 Bio: David is currently a senior at Bard College, where he is studying Political Studies and writing his senior thesis on cyberwar and cross-domain escalation. He also works at the Hannah Arendt Center for Politics and Humanities at Bard College as an Outreach intern. Post-graduation, David would like to leverage his extensive journalism experience as well as his interest in computer coding and social media to pursue a career in cyber security, both its practice and policy.
Bio: David is currently a senior at Bard College, where he is studying Political Studies and writing his senior thesis on cyberwar and cross-domain escalation. He also works at the Hannah Arendt Center for Politics and Humanities at Bard College as an Outreach intern. Post-graduation, David would like to leverage his extensive journalism experience as well as his interest in computer coding and social media to pursue a career in cyber security, both its practice and policy.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.