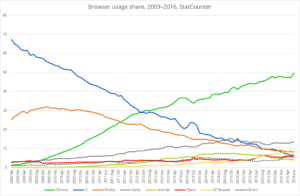
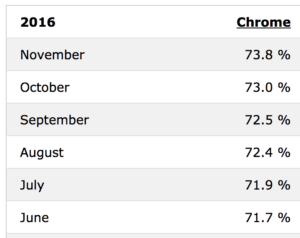
The latest browser statistics published in W3Schools show that Google Chrome’s popularity continues its upward flow relative to other browsers (Firefox, Safari, IE); it has now surpassed 70 percent of all usage over the past six months. With the ongoing aggressive campaign of Chrome in Google Search, we can surely expect Google Chrome to hit the magic 80 percent threshold of browser usage in the next few months.
When matched with Chrome’s projected growth curve, the release of Chrome 55 doesn’t bode well for the future of Flash. According to the Google blog, the Flash experience would meet its demise in December with Chrome 55, but subsequent tests on both Windows 10 and macOS showed that the browser did not restrict what’s rendered by Flash. The jury is, indeed, still out.
Beyond the future of Flash however lies a more burning question: What does this development mean for Flash vulnerabilities across the internet? In a non-Flash, or at least reduced Flash environment, where do the DevOps and security teams need to turn their attention? This article will seek to address these questions.
The HTML5 Takeover
In the recent update to Chrome 55, Google clearly showed its desire to transition the Flash experience to HTML5, by default. The main reasons are performance improvements, reduced power consumption for mobile users, and faster page load times. All of these contribute to the Google brand promise that technology always serves the user with the best possible experience.
However, there was one additional and potentially more significant reason for Google’s decision: improved security. This is because Flash is a very vulnerable engine that has been taken advantage of the most by common exploit kits.
Exploit kits, Flash and their interdependencies
Exploit kits are web toolkits that use payloads to uncover vulnerabilities in software, and they have been particularly effective when using Flash as the “way in” to remotely infect devices with malware. When we look at the most famous exploit kits from 2016 such as Angler, RIG, Neutrino or Magnitude, they are all heavily reliant on Flash vulnerabilities.

With the high usage number and the convergence to Chrome, we can expect the end of Flash very soon – but what will happen to the exploit kits market?
Security Implications of a Flash-less Web
There’s always a target
The client-side web exploitation market will be the most clearly affected. Security researchers will probably shift their reverse-engineering efforts to other engines, such as JS, SVG or any other objects supported in HTML5, putting those objects at a higher risk.
Are Chrome Extensions the Next Way In?
Regardless of whether we are indeed at the ‘end of Flash’, Chrome’s meteoric rise will see a simultaneous rise of attacks involving Chrome extensions, such as last year’s major AVG extension vulnerability. As Flash becomes harder to exploit, vulnerabilities will enter through paths of lesser resistance.
Backward Compatibility
Although Flash is being all but completely trimmed out from web browsers (Firefox, Edge & Safari have already abandoned Flash), there are still many websites that require Flash support, and these will keep the exception mechanism open. It is not far-fetched to say that Flash applications are likely to persist, perhaps in perpetuity, and the exception mechanisms represent a security weak point that cannot be ignored.
Moreover, not all tech consumers will know that Flash has been all but eliminated due to security concerns. Malicious actors will be able to successfully attack using social engineering techniques. Perhaps they will be able to convince users to enable Flash to view specific content, then slide in the open door. This method is quite similar to the exploitation methods behind the use of macro files to break into MS Office.
Adaptive Approach
Although it’s not yet known what the next browser-based attack will look like, we can hazard some guesses for the above reasons. Ultimately, it is only a matter of time until the next attack vector introduces itself. The advance of Chrome and the phasing out of Flash doesn’t mean the end of known vulnerabilities, but should rather serve as a reminder that security teams stay focused on maintaining the right intelligence, infrastructure and personnel that can adapt on a dime and take swift action. Fortunately, for organizations that must run lean in terms of their network architecture and IT staff, emerging security-enabled SD-WAN technology puts application control features into the cloud.
[su_box title=”About Elad Menahem” style=”noise” box_color=”#336588″][short_info id=’100249′ desc=”true” all=”false”][/su_box]







Most Commented Posts
2020 Cybersecurity Landscape: 100+ Experts’ Predictions
Cyber Security Predictions 2021: Experts’ Responses
Experts’ Responses: Cyber Security Predictions 2023
Data Privacy Protection Day (Thursday 28th) – Experts Comments
Experts Insight On US Pipeline Shut After Cyberattack
Most Active Commenters
Recent Comments
“Cybersecurity Awareness Month’s new evergreen theme "Secure Our World” is…
“Avoid storing data on personal devices: A crucial but often overlooked…
“I recommend a new nuance to passwords that isn’t often…
“In my role overseeing cloud environments and incident response, I'm…
“Cybersecurity Awareness Month serves as a reminder to confront the…