There is no doubt that in the right hands, Open-Source Intelligence (OSINT) can bring many positive benefits to the Cyber Security Professional, Forensics Investigator, or Government Agencies and Corporations who wish to secure their Digital Assets and Footprint. However, like all things which bring technological positivity to the table, there is also the potential for the sword to have a darker side to the blade which, when in the hands of hostiles, hackers, criminals, or others such as State Sponsored Actors who may utilise the power of good, in pursuit of evil outcomes.
As any OSINT practitioner will attest the power of this all reaching darker methodology can be utilised to footprint an individual, right up to tracking global movements of transportation, and it is here on the latter which I wish to focus in this article – and consider the world of aviation.
Before I get into the meat of this topic, I cast my mind back to when the Special Operation commenced in the Ukraine. At that time, I was watching the movements of NATO Military Traffic taking off from multiples of military airfields, aircraft of which were showing their route for all to see – including the eyes of the hostiles. However, whilst NATO military traffic was visible in the vicinity of the region under attack, it was evident that, whilst they were playing by the rules, there was a notable absence of any tracked Russian military aircraft in the vicinity. Conclusion here was:
a. there was no Russian air activity in the area (hmmmm)
b. Russian aircraft had employed masking their transponders from advertising the identification and barometric altitude – a tactic now also being employed by NATO
So, you see the point is, if you play by the rules, you can be tracked.
In September 2022 we sadly lost our Queen, so, myself, accompanied by my wife and our 9-year-old granddaughter travelled to Windsor to pay our respect, and to lay flowers to mark the passing of a great lady. It was noticeable during the visit to Windsor just how focused the security operations were to secure the Royal Family, and the public against threats of the modern day – dog patrols, high viability policing etc. At that time, I noticed the police sealing such potential dangers of manhole covers, and other forms of ground based access points which could be utilised for terrorist intentions, so it would seem security was looking at all possible angles to decrease the risk!
OK, now back to the focus of the article – when watching the arrangments for, and movements of High-Profile Royals during those sad days in September, it struck me that, given the state of world security in 2022, it may not always be a good thing to advertise the movements of High Worth Principals such as Royal’s, which by inference increase their exposure by an unknown factor. It was here during such movement in September 2022, where I found it simply astonishing that it was so easy to track, not only the movements of our most senior members of state on the ground, but it was also possible to track them in the air also. At Fig 1 we can see the Royal Air Force aircraft approaching Aberdeen Airport, at Fig 2, we can observe the aircraft on the ground, and at Fig 3 we have confirmation of the accuracy of the tracking system
Fig 1 – Aircraft approaching Aberdeen Airport
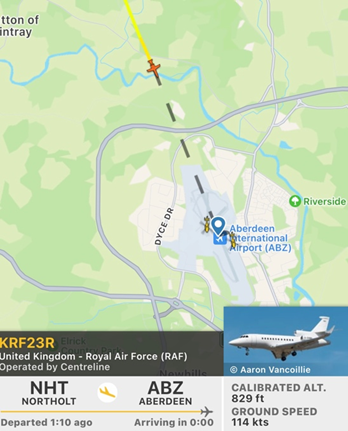
Fig 2 – Aircraft on the ground
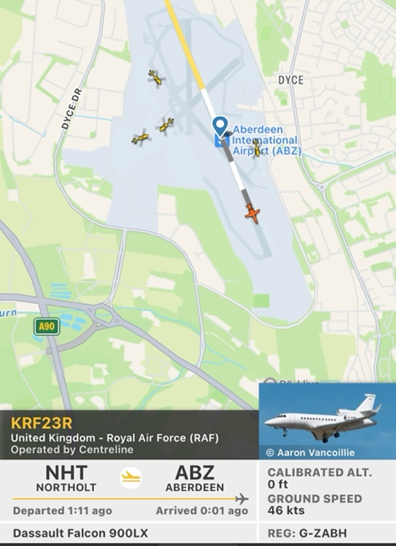
Fig 3 – the aircraft as seen on the BBC News

So, this may be an obvious observation, and of course I am certain that there were precautions taken on the day to assure the in-flight security of this very precious cargo – but my point here is, Pilots can legally turn of their on-bord transponder for various reasons – should one of those reasons also be security to protect High Worth Persons, and members of the global Royal Families when they are in flight – surly in 2022, security must be a precedent.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



