Investigating several domains registered using the email address drake.lampado777@gmail[.]com. IBM Security X-Force spotted the information-stealing malware named Corebot.
The Corebot’s author included the ability to add plugins to the malware in order to incorporate more features. The features are usually a specific function the malware will perform or turned the bot in, such as being a socks proxy or adding the possibility for the malware to spread via USB drives, grab certificates, or even perform DDOS.
The sample analyzed by IBM Security X-Force communicates with two domains registered to drake.lampado777@gmail[.]com that are down at this time :
 We found a 64bits version of Corebot, but the sample seems buggy and doesn’t work out properly which suggest that it might still be under development.
We found a 64bits version of Corebot, but the sample seems buggy and doesn’t work out properly which suggest that it might still be under development.
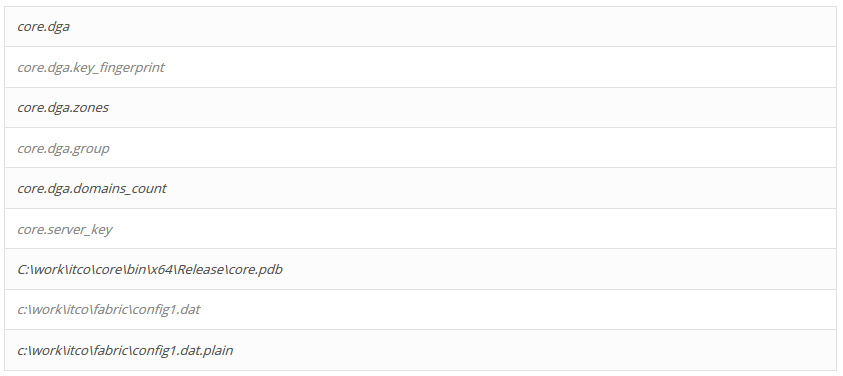
You can find similar strings in the 64bits code as the 32bits :
 Hosted on the same IP address 62.76.41.5, we found more interesting domains. One was used as a Carberp C&C and the two others hosts a TVSPY C&C :
Hosted on the same IP address 62.76.41.5, we found more interesting domains. One was used as a Carberp C&C and the two others hosts a TVSPY C&C :
We recently released a blog discussing TVSPY in greater detail. TVSPY is a remote access tool (RAT) leveraging Teamviewer software to gain access to remote computers. With this tool, the attackers could gather private information from their victims as well as take control and install further malware at will.
What else has drake.lampado777@gmail[.]com registered :
Out of the 30+ domains registered using that email address, one domain stood out, btcshop[.]cc. This is a fairly new domain created July 30th 2015. The domain may mislead people as this is not an online shop to buy bitcoin, but an online shop to buy lists of Socket Secure (socks) proxies and personally identifiable information. The lists of proxies are usually infected machines turned into a socks proxy to be used for further malicious activity. Several malware families have the capability to turn an infected machine into a socks proxy. However, this shop has a few peculiarities that are interesting.
The registration process is very simple. You just have to click on the Register button and you are redirected to a new screen notifying you that the registration has been successful. It gives you a hash as a way to log in. The hash is 41 alphanumeric characters long similar to a sha1 hash.
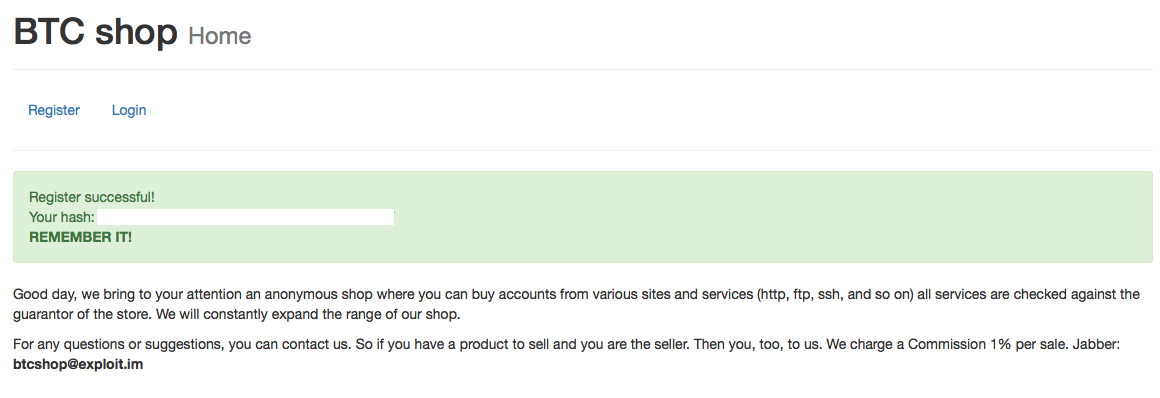 Once you get the hash you just have to click on Login and copy/paste the hash to get in :
Once you get the hash you just have to click on Login and copy/paste the hash to get in :
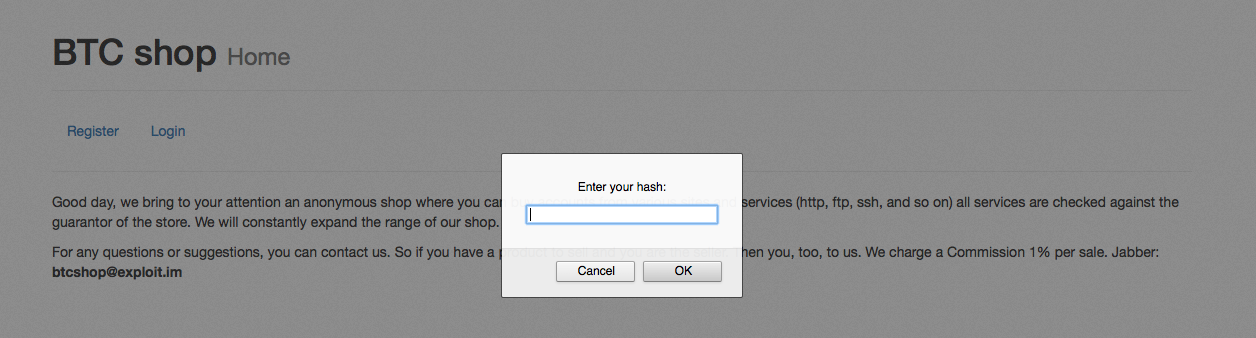 Once you are logged in, there are two tabs available, Accounts and Socks. The Accounts tab lists several countries you can choose from and check if there are any accounts available. There is no specification of what type of accounts but we can assume they contain personally identifiable information (PII). It also shows a bitcoin wallet assigned to you automatically. To purchase, you’ll have to add bitcoin to that specific wallet. Every hash has a new Bitcoin wallet address assigned.
Once you are logged in, there are two tabs available, Accounts and Socks. The Accounts tab lists several countries you can choose from and check if there are any accounts available. There is no specification of what type of accounts but we can assume they contain personally identifiable information (PII). It also shows a bitcoin wallet assigned to you automatically. To purchase, you’ll have to add bitcoin to that specific wallet. Every hash has a new Bitcoin wallet address assigned.
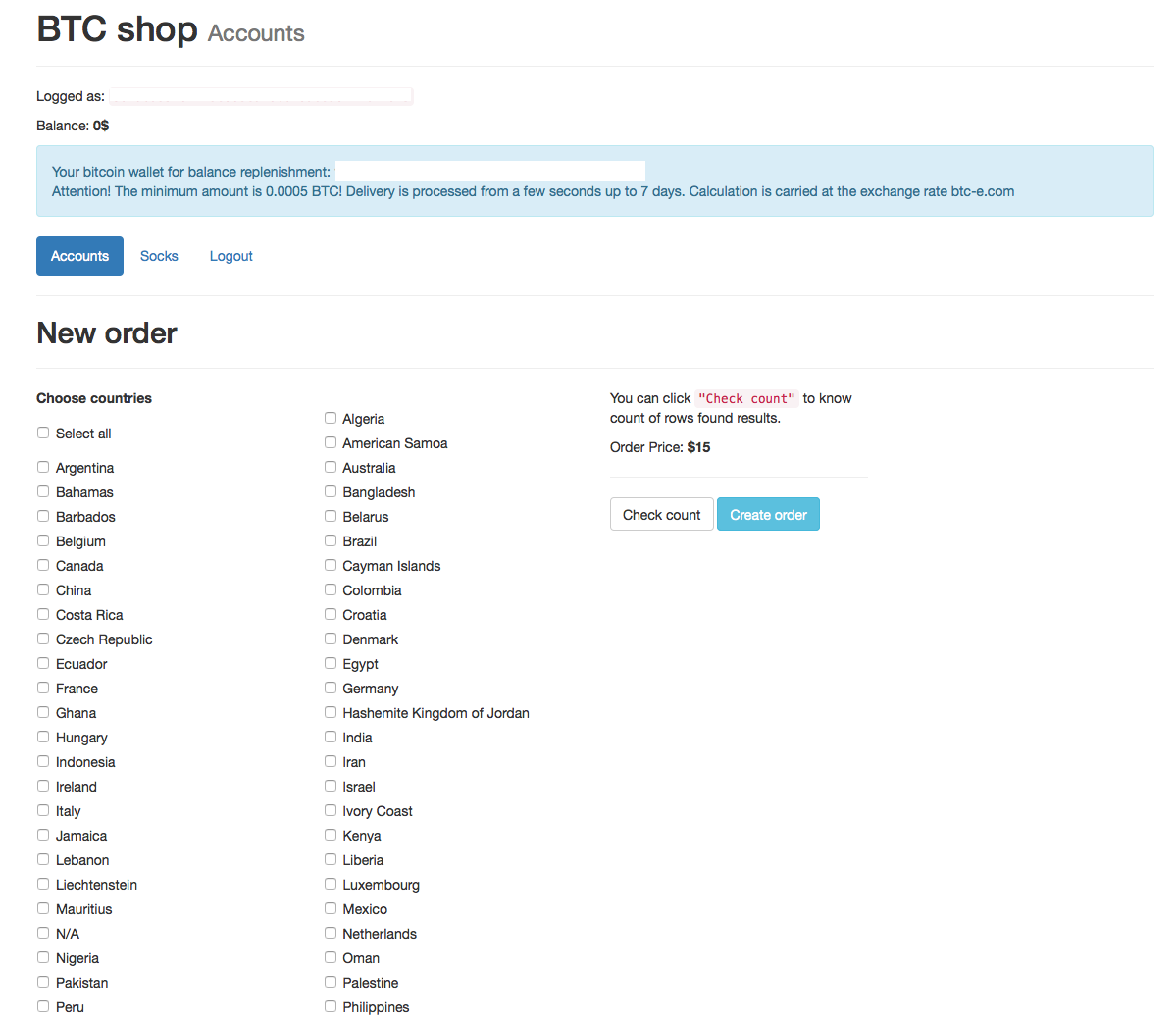 As of writing, the base contains 9597 “rows”, where “rows” are individual accounts :
As of writing, the base contains 9597 “rows”, where “rows” are individual accounts :
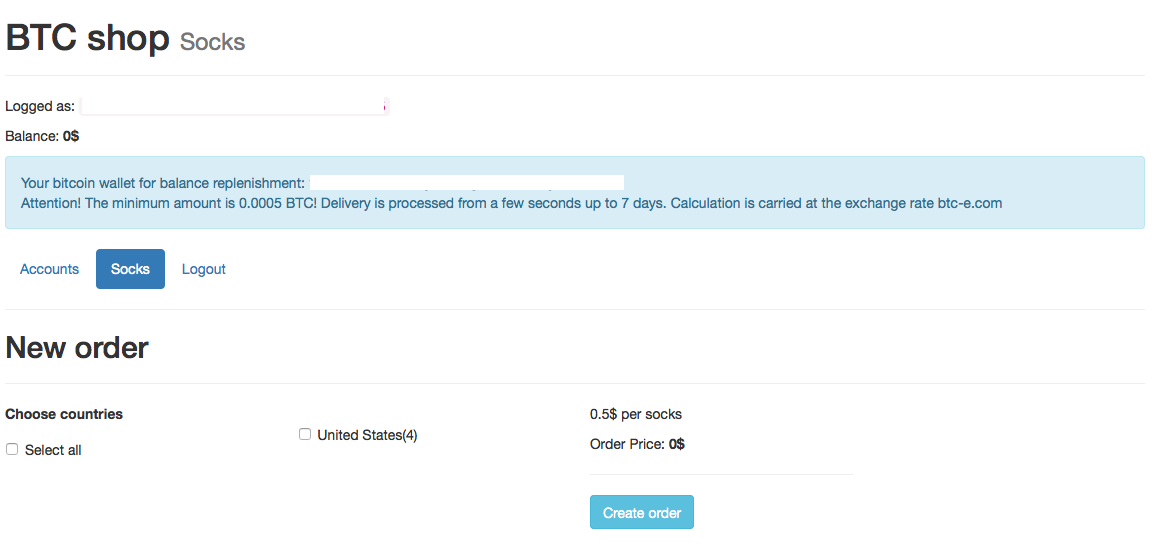
 The socks Tab only seems to contain 4 socks proxies located in the United States.
The socks Tab only seems to contain 4 socks proxies located in the United States.
Once the information about the malicious domains linked to the email drake.lampado777@gmail[.]com was collected, we looked into what we could find about btcshop on forums. We found someone using the handle btcshop who wrote a few posts on forums. In one post btcshop asks advice on how much he could sell socks proxy bots for. The jabber account used is the same account advertized on btcshop[.]cc, btcshop@exploit[.]im.
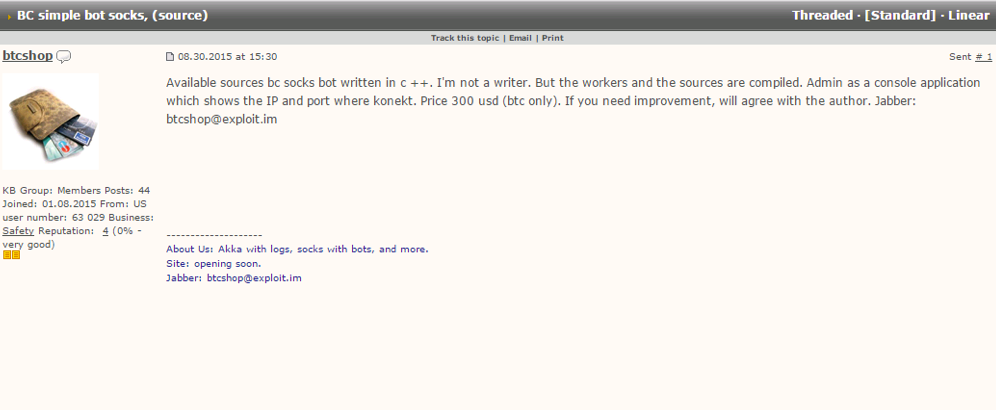
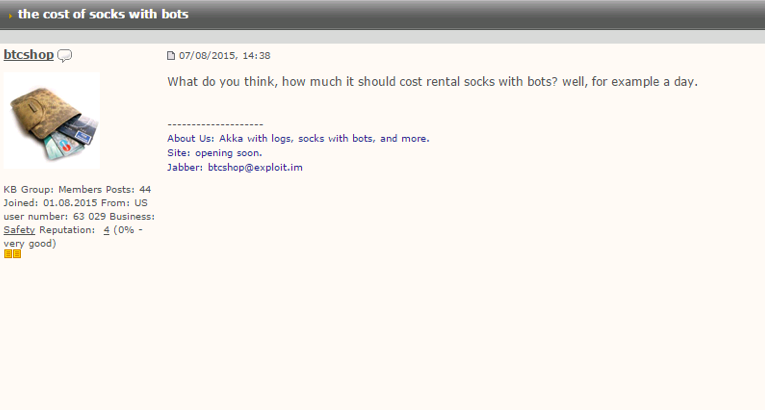 In another interesting post btcshop is apparently selling bot source code on behalf of the author.
In another interesting post btcshop is apparently selling bot source code on behalf of the author.
The email address is linked to a Google+ account :
https://plus.google.com/118423272977624417312/posts
Conclusion:
The link between Corebot, the TVSPY C&C and the online shop is the email address used to register all the domains. We were able to link the online shop to a person on a forum using the handle btcshop and using the Jabber account btcshop@exploit.im. This person may or may not be running Corebot and TVSPY a way to collect personally identifiable information for sale in his online shop. However, it would be convenient for the same person or a small group of people to be running malicious domains registered under the email drake.lampado777@gmail[.]com and also running btcshop to sell their collected wares. More evidence is needed to definitively say that drake.lampado777@gmail[.]com and btcshop@exploit.im are the same person.[su_box title=”About Damballa” style=”noise” box_color=”#336588″] As a leader in automated breach defence, Damballa delivers advanced threat protection and containment for active threats that bypass all security prevention layers. Born for breach defence, Damballa rapidly discovers infections with certainty, pinpointing the compromised devices that represent the highest risk to a business, and enabling prioritized response and refocusing of security experts to the areas of greatest risk to an enterprise. Our patented solutions leverage Big Data from one-third of the worlds Internet traffic, combined with machine learning, to automatically discover and terminate criminal activity, stop data theft, minimize business disruption, and reduce the time to response and remediation. Damballa protects any device or OS including PCs, Macs, Unix, iOS, Android, and embedded systems. Damballa protects more than 400 million endpoints globally at enterprises in every major market and for the world’s largest ISP and telecommunications providers.[/su_box]
As a leader in automated breach defence, Damballa delivers advanced threat protection and containment for active threats that bypass all security prevention layers. Born for breach defence, Damballa rapidly discovers infections with certainty, pinpointing the compromised devices that represent the highest risk to a business, and enabling prioritized response and refocusing of security experts to the areas of greatest risk to an enterprise. Our patented solutions leverage Big Data from one-third of the worlds Internet traffic, combined with machine learning, to automatically discover and terminate criminal activity, stop data theft, minimize business disruption, and reduce the time to response and remediation. Damballa protects any device or OS including PCs, Macs, Unix, iOS, Android, and embedded systems. Damballa protects more than 400 million endpoints globally at enterprises in every major market and for the world’s largest ISP and telecommunications providers.[/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.