For about a decade now, I have both practiced and taught, what has, up to 2022, seemingly been considered a Grey Art – that of Open-Source Intelligence (OSINT), and its related methodologies in the UK, the UAE, Pakistan, India, and the Far East for Commercials, Industrials, Government, Police Authorities, and Military Agencies, and in that period, I have evolved a very powerful OSINT toolset. However, the world is changing, and as such we continually need to apply the life-long approach of CPD (Continuous Professional Development), and of course the continued evolution of our toolsets to keep tuned to the new threats as they emerge. In this article, I will expand on some of the exciting new OSINT tools and products we discussed in the recent Information Security Buzz Middle East WEBINAR which have entered the growing OSINT market space. However, as a prerequisite, I feel it is important to set the scene, and to outline how the new age threats and challenges of 2022 and beyond need to be understood and embraced by the way we engage and operate – please read on for the introduction to the ever-morphing Cyber Threat Landscape.
The Growth and Morphing of the Cyber Threats
It was July 2008 when presenting at a UK Government Home Office sponsored security event, held at the British Library in London, when, post the cyber-attacks labelled Titan Rain, attacks identified as manifesting from servers located in China, when it would seem, I was the first person to publicly denounce the Chinese Government for being actively involved in sponsoring cyber-terrorism and attacks, or who were complicit in looking the other way whilst their cyber-aggressor units started to hone their green shoots of digital adversity. I do recall, that whilst protests were made to the UK Home Office, one very senior Officer in the, then Metropolitan Police Computer Crime Unit congratulated me on outing a topic which everyone was aware of, but of which no one was willing to speak of in the public domain – reason being, my uncomfortable revelations were far too close to the upcoming Games of the XXIX Olympiad (AKA Beijing 2008 Summer Olympics) running from 8 to 24 August 2008 – see URL below:
https://www.itnews.com.au/news/china-blamed-for-cyberterrorism-118089
Post 2008, within the next decade there was a quantum shift in relation to the cyber dangers posed by the Chinese, as the growth of cyber-attacks started to emerge with higher frequency, and with the onslaught of cyber missions in the guise of identifying, and acquiring trade secrets, and other forms of IP (Intellectual Property) out of active Industrial Espionage missions running out of the region, and also from some University campuses situated in the US, and UK.
In 2010 the gloves came off, acknowledging the electronic dangers posed by the Chinese Doctrine, which were (are) well documented in the publication Unrestricted Warfare in 1999, authored by two Colonels of the People’s Liberation Army, Qiao Liang and Wang Xiangsui – a publication which made it very clear that, Chinese World Dominance should be achieved though any means, be they fair or foul – see the following URL:
https://www.iwp.edu/books/unrestricted-warfare/)
However, by now, the opinion of the UK Government had also changed with the circulation of a Cabinet Office Government Security Secretariate Quarterly Threat Update in April 2010, representing the first tangible UK Government acknowledgement of the dangers posed by China, and for that matter Russia – see Fig 1 below:
Fig 1 – Security Secretariate Quarterly Threat Update in April 2010
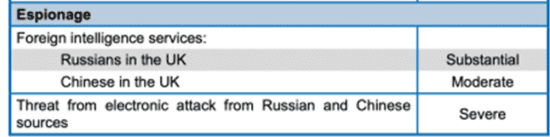
Come up to Date – 2022 – FBI Opinion on the Threat posed by China
On 24th April 2022, in an interview with CBS News, the FBI Director Christopher Wray put on record that the current scale of espionage and cybersecurity threats from China were “unprecedented in history”. Wray went on to add “The biggest threat we (the US) face as a country from a counterintelligence perspective is from the People’s Republic of China and especially the Chinese Communist Party “.
Wray went on to outline that China was actively targeting US Innovation, Trade Secrets, and Intellectual Property (IP), on a scale which is again, unprecedented in history, adding China’s Hacking program is larger today than that of every other major nation combined.
Cyber Resilience
One significant area of concern in 2022 is the level of the Persistent Levels Insecurity (PSI) which exists on far too many Governments and Local Authority Website (not to mention some Commercials), many of whom have already fallen on multiple occasions to the real-world consequence of Hacking, Ransomware, and/or Compromise born out of hostile, Cyber Criminals, and State-Sponsored Agencies or Proxies. However, when you take note of the levels of exposure such deployments run in tandem with their operational activities, it does tend to outline the level of risk and vulnerabilities such deployment allow on an extant basis. See Fig 2 as a redacted OSINT example of the profile of one UK Government Local authority carrying 3,215 Compromised Accounts, 67 Breaches with 8 pastes on to the Internet and DarkWeb (Pastebin etc), 10,831 Data Leaks, and 1,370 Password Security Issues:
Fig 2 – Live Website in April 2022
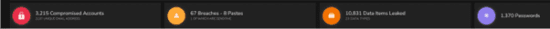
Credit: produce by BreachAware application – www.breachaware.com
OSINT Toolset Fit-for-Purpose
So, accepting and acknowledging the existing threat(s), the OSINT Professional needs to ensure their toolset are fully aligned with the levels of digital aggression the world is facing, here I am considering the operational requirement to expand into a world, yet unknown to myself in relation to researching and investigating any threats manifesting from China. That said, on past occasions when such a task has crossed my desk, I have been very much aware of the complexities involved with such investigations into any elements associated with the Chinese Web – which led my logical path to the door of I-Intelligence.
I am also looking to update my OSINT Toolkit with commercial applications to compliment my OSINT posture when conducting investigation to derive meaningful intelligence of any acquired artifact and scattered (seemingly unrelated) digital objects – it is here where have landed on the value of two Swedish applications in to form of PALISCOP and YOSE
Whilst researching for the WEBINAR which was published by Information Security Buzz on 26th April 2022 (On-Demand Buzz WEBINAR available at the URL below:
I discovered a very exciting, unique offering out of a company based in Zurich, I-Intelligence (https://i-intelligence.eu). Here I was very interested in their unique training courses which are focused on supporting OSINT Professionals, Researchers, Academics, Law Enforcement Agencies, and businesses achieving a pragmatic understanding of the Chinese-language internet and the associated social media sources to discover and identify people, Chinese language documents, and to enable the professional on how to set their devices to support location specific regional data-collection with processing and translation. In this age of Globalised threats, and in this instance, in particular the Chinese area of associated risks, for myself, I consider this training an invaluable must have resource to research and investigate Chinese-language areas of interest to either validate Chinese companies, or to identify hostile actors.
To add to my favourite list in support of the Information Security Buzz WEBINBAR, I included two of my top-rated commercial, must have OSINT applications, which are PALISCOPE and YOSE (https://paliscope.com). The first part of this pair of tools is PALISCOPE which provisions a built-in forensic browser with highly secure capability that supports the contemporaneous recording for the professional when capturing Digital Evidence directly from the source, along with the application of necessary time/date stamping and annotated hash values. These capabilities and more make this a tool I simply would not be without in my OSINT Toolset to support a robust level of Case Management when discovering and acquiring artifacts which may represent, case related Objects of Intelligence Interest (OoII) to turn them into meaningful intelligence, all of which are processed under a complete overseeing Audit Trail of activities, making the investigation outcome more robust in cases which may encounter some form of challenge.
With the second tool in the PALISCOP armoury, we encounter YOSE (Your Own Search Engine). Think of YOSE as a massive container which may be populated with all the acquired and encountered OoII, ranging from email, web pages, images, telephone numbers, chat analytics etc, which then will form an emerging database which may be searched, based on lexical parameters, which may, for example associate and match the diverse relationships of objects, providing a conjoined picture of disparate, seemingly non-related artifacts, to form a related Meaningful Intelligence. The real longer-term value here is, the YOSE environment will provision a high worth tool to enable the Investigator, SOC Analysists, and CSIRT Teams to better leverage the historic, past encountered events with a relationship, as and where they exist in today’s encountered adverse situations.
Conclusion
When it comes to the Digitised World upon which people, business and agencies rely, vulnerabilities and exposures can represent a very complex paradigm which, by inference dictates that Cyber Responsive capabilities must be fully honed to meet the challenge of the time. It is here where, in the year of 2022 OSINT, and the underpin smart toolsets and awareness empower the engaged person or team with the capabilities to respond, investigate and verify out of the shadows what is real, or fake with a much-increased level of high probability. In a world overspilling with Threat Intelligence, and adverse events, no longer will the simple pen, paper and clipboard suffice –smart attacks require a smart response.
John is the Principle at Shadow-Intelligence (Si), partnering with PALISCOPE, BreachAware and iStorage. He is a Visiting Professor at the School of Science and Technology, Nottingham, Trent University (NTU) and holds the appointment of Editor in Chief for the International Journal of Cyber Forensics and Advanced Threat Investigations (CFATI). For the last decade he has delivered training courses in the Middle, and Far East to Commercial, Industrial, the Financial Services Sector, and Military Agencies, including the UAE, US, Pakistan, Saudi Arabia, Malaysia (KL), Singapore, Argentina, and Sao Paulo
He served in the Royal Air Force 22 years’, specialising in Counterintelligence, working with UK Agencies such as GCHQ/CESG, and others in the fields of SIGINT, COMINT and Satellite Communications, holding appointments such as System ITSO for a CIA SCIF.
In the commercials sectors of IT/Cyber he has worked for/with Logica, Bae, T5, GM, Experian, Betfair, Palace of Westminster, House of Lords/Commons, TSol (Treasury Solicitors) and provided Consultancy to the Saudi Arabian MOD, TRA (Telecommunications Authority (Dubai) and the Military Academy of Malaysia (KL) on SOC, CSIRT, Digital Forensics and OSINT. Within the last 5 years he has focused on Geopolitics, with global expertise around the UAE and Russia, Anti-Terrorist Operations (ATO), Cyber-Warfare, Dezinformatsiya (Disinformation) and Maskirovka (Military Deception).
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



