There is absolutely no doubt that the Investigative Journalist, Geoff Whites book, The Lazarus Heist (LH) is not only one of the best researched accounts of the dirty dealings of cyber-criminals, and state sponsored geopolitical actors, but is also a very exciting read. However, when considering some comments on Social Media, and other related professional platforms such as LinkedIn, and noting the position of those who were commenting left me with an itch which I have to scratch – as it was almost like they were viewing such subject matter for the very first time through a well presented window, whilst in some instances, actually missing and overlooking the subjective past which has brought us to this juncture of, what appears to be virgin revelations – did we not listen to the words of Richard A. Clarke in 2010, in his published work, CYBER WAR:
‘if we could put this genie back in the bottle, we should but we can’t ’ – (referring to the way in which society has embraced technology)
Or to put it another way in the words of Geoff White:
‘Its (these events) showed the bank, like many other institutions, was ready for criminals entering via the front door and carrying out a traditional form of physical crime. What it was they were less prepared for – what so many businesses across the globe seem achingly unready for – was (is) a digital crime being committed from within its own computer systems’?
Thus, one may conclude based on the inference that not all is well in the world of Cyber (Digital) Security when it comes to professional, anticipated awareness. However, what jumps out for me from the text of Geoff’s book is the associations with so many previous, successful heists which have demonstrated the same Modus Operandi (MO), which it would appear many have simply not noticed what has been in plain sight of the more current Digital day of cybercrime! Maybe it takes a lexical based Sky Glass moment to present the known-known facts in a manner which may be accommodated by an armchair read – a read which, when concluded, may place the book to one side, and move on, still with a modicum (or more) of ignorance of one’s own security posture.
To appreciate the cunning and success of the LH, we may look back over a number of historical cyber attacks which have demonstrated a similar MO of a number of the well documented LH accomplishment, these in the guise of the Tesco Bank Heist, and the debacle which implicated Equifax with such an adverse digital impact – along with many others which there simply is not room to accommodate in one single article – but nevertheless less, please see Fig 1 to give you some feel for the scale and numbers we are considering.
What is of course, or should be a revelation from Fig 1 are:
- The vertical and horizontal sector position of the compromised targets – say, from Aviation to Medical and everything sense in between
- The disparate size of the targets – in other worlds no matter how big or small, they are, the cross hairs of the attackers landed on the targets with equilibrium of the objective
The implication that, notwithstanding the assertion larger targets will be accommodated with a considerable cyber security spend, and the associate manpower, in many of the cases here, they have failed to defend their enterprise – considering Betfair, Experian, Equifax, TalkTalk, TNT, BA, Britannia Building Society (AKA Cooperative Bank), FedEx, and the UK’s National Health Service (NHS), and several other glowing examples of lacklustre security postures.
Fig 1 – Example of these fallen to Cyber Offensives

Not wishing to repeat myself but going back to Geoff Whites comment:
‘What so many businesses across the globe seem achingly unready for – was (is) a digital crime being committed from within its own computer systems’
There are several factors to consider, some may be a simple as the very leadership and skill that are (or not) employed within organisations. Take two examples involving the commonality between Experian and Equifax, which are:
- They have both suffered significant and multiple breaches
- Members of the Security Executive Teams have worked for both organisations
- Both companies as of today are still running with insecurity and exposures
This possibly leads to one conclusion – if both organisations are of such an insecure posture, with long histories of breaches, one must ask the question, are they employing staff who are upskilled enough to engage and fight the current onslaught of cyber-insecurity? Maybe here, when we consider, what is possibly the important factor of skills. Should we apply the mantra, if you can’t change the people, change the people.
The other itch which needs to be scratched is around the number of conferences and events on offer – from SC, and Infosecurity (UK and US), through to other providers such as ISMG, all of which run events which discuss the latest and greatest cyber challenges – and given delegates are attending on mass, how can it be that some are surprised by the revelations of Geoff Whites book – have they not noticed what has been occurring in the cyber world for the last two decades, and beyond? Is this a case a leading the horse to water, but observing it is not drinking? Consider two areas which are introduced in The Lazarus Heist, which are the use of weekend and down time periods to maximise the successful outcome of a cyber-attack. If we care to cast our minds back on this style of MO, we will discover that this approach has already been used, in a sophisticated 48-hour attack against Tesco Bank which resulted in £2.26m being pulled from 9,000 customers – was this a trail run in a testing phase (sort of UAT (User Acceptance Testing) in reverse).
Fig 1 – Tesco Bank

The second revelation is around how dirty money may be converted to clean usable currency. Again, using Gambling Betting systems is again nothing new – as my old friend Steve Gold (RIP) said, for years the gambling industry has been aware that groups like Chinese Triads and other criminals have been using both Kiosk, and Betting Exchanges to wash their criminal gains into clean funds. In fact, as Steve Gold added, when a team of gamblers place dirty funded bets at multiple high street outlets, notwithstanding the losses which may occur, what comes out the other end is clean, so it’s a balanced risk. And washing of funds doesn’t not stop there – even gaming and social media platform such as Second Life and others have been utilised to convert grimy funds into, say Linden Dollars, and then out again as washed currency.
Fig 2 – The Workings of Betting Exchanges
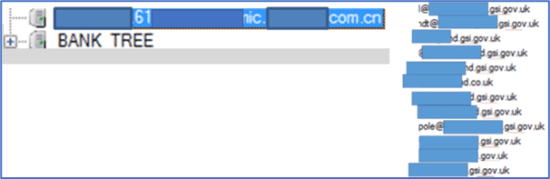
When we consider the world of Banking, I recall some ten years ago, when using OSINT, I discovered a compromise within the infrastructure belonging to one of the UK Top Financial Institutions – in fact I would say the top Institution. The compromise in question involved several Chinese (.cn) domains being attached to key systems, which seemingly offered some form of remote access capability. The institution involved were notified, and grungily accepted the outrageous report, researched the supposed compromise, and within day the servers were observed to be removed – sadly three months later they were again re-established. However, it was also discovered that there were more holes within the Swiss-Cheese build of the infrastructure, which resulted in the further discovery of sensitive government related identities, along with their email addresses – See Fig 3.
Fig 3 – Real-Time Unknown Insecurity
To conclude with one final example of insecurity, I am considering the discovery of an open Zone Transfer at a large East Midlands based organisation providing Financial Services Support facilities. In this case, not only was the zone showing all supposed protected servers, but which in turn led to the discovery of sensitive servers storing customer related applications and information, accompanied by a script with hard coded ID and the associated password – providing unfettered access to said asset.
OSINT (Open-Source Intelligence)
One final word on how such discoveries may be exposed for both good, and evil purpose to locate how objects and assets of interest which may be silently inspected or exposed. Consider OSINT as a Pond Skate supported by the tension of the water, but which is so light it does not break the surface – not dissimilar to OSINT in the form of what I think of as Layer 8 of the OSI Stack. Remembering that attackers will tend to assess what they may exploit in a Cuckoos-Egg style MO, to gain unauthorised access to compromise of a target to increase their success rate. One methodology which may be applied is to say consider the objective of compromising an object at Layer 3 and then working out what direct or indirect techniques may be applied from the acquired intelligence which may be leveraged in pursuit of a Project Managed attack to establish a compromise of, or to take part or complete ownership of the intended target – by example, a little like an open Zone Transfer. See Fig 4.
‘Hackers tend to think outside the box, and do not necessarily apply the conventions of expectation’
Fig 4 – Layer 8 – The Pond Skate

Conclusion
It was 1993 when presenting a paper at the Virus Bulleting Conference at the Grand Hotel Krasnapolsky on Dam Square, Amsterdam about bypassing Anti-Virus protection by encapsulating payload. It was at that event when I sat in on a talk by Winn Schwartau about Cyber War, and I was indoctrinated from that moment on. However, I did note that I was but a part of a minority, with most delegates pushing away the theory as hype – something I also personally encountered over the next decade where I have met similar challenges of rejection of the prospect of Cyber War was (is) real – in fact I recall, one very senior professional commenting ‘how can you harm anyone with a computer’ – granted in 2022, we can now answer that question from a position of known known authority.
There is no getting away from it, the Lazarus Heist is both an excellent, and an educational read, and is thus strongly recommended to anyone involved in, or with an interest the world of Cyber Security (or let us call it Insecurity). However, what we may not have noticed from the stylisation and MO of attacks employed by the North Korean hackers, this is nothing new and has been with us now for at least two decades in which the aggressors have silently honed their skills in plain sight and have become more proficient than those they are attacking. You only have to look back at the existing evidence, over previous decades to what was referred to as, the so-called WW1 (Web War 1) suspected to have emanated out of, yes you guessed it, North Korea – probably driven by Unit 110 of the KPA (Korean People’s Army) which is but one example of the North Korean cyber-aggressor capabilities in place in that era, alongside Unit 121 Unit (Cyber Warfare) which, even in those early days, it may surprise some to know they had approximately 600 skilled hackers assigned to the activity of Cyber War (Conflict) – others included Unit 204 (Cyber Psychological Warfare) who had in that day 100 hackers assigned to the activity. In that very same period, Russia was sharpening their very own Cyber-Sword under the direction of the then alumnus Director, Vladimir Putin out of the old world of the KGB, as it morphed into a new agency with a very focused on the digital mandate!
It is also interesting that in 2022 Bridewell surveyed 521 critical national infrastructure decision makers across multiple sectors, finding that 95% are experiencing factors that would make them likely to leave in the next 12 months. These leaders overwhelmingly attributed their desire to leave their position to two dominant causes:
- 42% say a cyber breach is inevitable and do not want it to tarnish their career
- 40% say stress and burnout are heavily impacting their personal lives
- Or could it be another reason as – Critical infrastructure operators must now report significant cyber breaches to the federal government within 12 hours of an attack, following the expiry of a three-month grace period that enabled nearly 2500 of them to prepare for the new rules – see https://lnkd.in/dxUb3eMC for the regional relevance of this legislation
Considering some of the areas I have introduced above in relation to dire security failed cyber-defences, my thoughts here are – based on what I have had first hand experiences of in multiple organisations, are we now seeing the tip of the blade which infers, as I am starting to conclude, some who have been holding Senior Cyber Security Leadership roles are now realising that they may be deficient in areas of anticipated skills, which is leading to a very hot kitchen in which, under the heat, accountability is now looming!
And given it’s not just North Korea, but the Russians, the US, the Germens – in fact anyone with a need to a defensive, or attack focused aggressive cyber posturing – we need to evolve pragmatic methodologies for delivering a robust cyber security posture, backed up by nuts-and-bolts skills, not security based on the long-standing, well-established tick-box approach. It may be that simple approach with the ticking of the ISO/IEC 27001, Cyber Essentials, or other such high-level cyber strategies to deliver robust cyber security defences works for your organisation, so that is just great – but consider, does that very approach also work for your adversaries!
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.