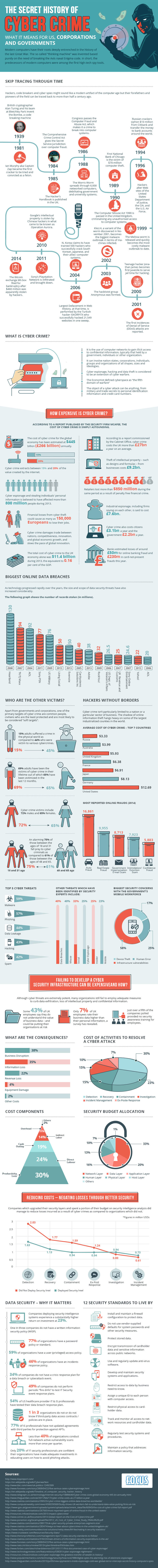
Cyber crime is on the up and with the recent hacking of Talk Talk it’s more prevalent than ever. However, hacking is not a recent phenomenon. The very first example of a computer being used to “hack” was the Enigma Machine created by a certain Alan Turing, the godfather of modern day computer science.
The first large scale attacks were first seen in 1989 when $70 million was stolen from the First National Bank of Chicago. This shocked the world and triggered the Computer Misuse Act 1990 to be passed as law in the UK. The act criminalised any unauthorised access to computer systems and was a big step in attempting to halt cyber crime.
In more recent years, cyber crime has posed a massive threat to national security, with groups like Anonymous and Lizard Squad becoming more and more powerful. As cyber crime becomes more of an issue many organisations seek to protect themselves using courses to train employees in the very real risks of the online world.
The infographic below, created by Focus Training, aims to highlight to the huge financial implications of these attacks and where they have originated from, as well as some simple security standards to live by.
 [su_box title=”About Focus Training” style=”noise” box_color=”#336588″]
[su_box title=”About Focus Training” style=”noise” box_color=”#336588″] As UK businesses experience constant increases in fraud, theft and criminal activity, isn’t it time you protected your assets with effective fraud awareness training and investigation training solutions from Focus Training (UK) Ltd. We offer a comprehensive range of training and solutions that includes fraud prevention and detection, as well as teaching the skills needed to source and analyse intelligence effectively, resulting in solid outcomes and the ability to increase security in areas shown to be lacking.
As UK businesses experience constant increases in fraud, theft and criminal activity, isn’t it time you protected your assets with effective fraud awareness training and investigation training solutions from Focus Training (UK) Ltd. We offer a comprehensive range of training and solutions that includes fraud prevention and detection, as well as teaching the skills needed to source and analyse intelligence effectively, resulting in solid outcomes and the ability to increase security in areas shown to be lacking.
Since our foundation in 1997, Focus Training has quickly risen to become one of the UK’s leading providers of Investigation and Fraud Courses, with clients that include government departments and multi-national corporations operating in over a hundred different countries. With the help of our carefully vetted and highly-trained staff you’ll be able to manage your own fraud and security issues swiftly and discreetly.[/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



