As an Expert Witness, Digital Forensics First Responder Investigator, and a provider of specialist training in the disciplines of in-depth Cyber Security Management, and Digital Forensics and Investigations, to underpin both operational engagements, and my academic teaching, and training commitments in Dubai for Meirc, I need to selected a trusted tool-sets and utilities to support my various missions – and these I call ‘My Favourite Things’.
So, what qualifies entry into my selection criteria of ‘Favourite Things’? Well in no particular order, please see below:
- They must add value to the activity
- Stability of the tool is paramount.
- They must be cost effective
- Ideally, they should be in use with Law Enforcement, or other recognised Agencies
- I expect them to achieve value for money – and not be too expensive
- They must be subject to have regular updates – or updates as directed by requirement
- For Teaching – they should not have a steep learning curve
- And of course, they must be underpinned with good support
And so, based on the aforementioned criteria, I can confirm that three of my selections into ‘My Favourite Things’ are shown below meet my base selection criteria.
Belkasoft Evidence Center 2017: The first tool I wish to pay homage to is that of the excellent and the highly credible Digital Forensics application in the form of the Belkasoft Evidence Center 2017 (https://belkasoft.com/ec). The first noticeable credit to this tool is it is easy to use – and in the case of my students, they manage to get to grips with it with the minimal of applied learning curve (unlike some other systems I have utilised). The Belkasoft Evidence Center enables the investigator to acquire, search, analyse, store and share digital evidence discovered, and acquired from computer systems, and mobile devices. What is even more impressive to me as a user is the speed at which the toolkit can extract digital evidence and artifacts from multiple sources, by interfacing and analysing hard drives, drive images, memory dumps, iOS, Blackberry and Android backups, UFED, JTAG and chip-off dumps – particularly important to me when under time pressure. However, within the classroom environment, its ease of use is even more impressive when I set my students on the end-of-course Investigation of a Digital Crime Scene – here I can attest even those new to this platform become productive in a very small window of time.
Belkasoft Live RAM Capture in Progress
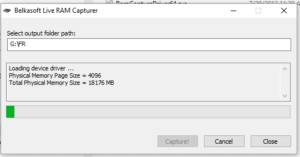
Add to the above this toolkit in in use with both UK and International Law Enforcement, Big Name Consultancies, and Government Agencies – then add to this fact the low-price tag, and the free tools Belkasoft offer like their Live RAM Capture, and the Belkasoft Acquisition Tool. This, in this category for me makes this toolkit a no brainer of choice to have in both my Operational and Teaching Bags alike.
Echosec: My second tool of choice is out of the stable of those nice people at Echosec (https://www.echosec.net/). Echosec is a location-based search platform which provisions, security, journalism, intelligence agencies, law enforcement, investigators, and, in my case academics and teachers with actionable knowledge discovered from OSINT (Open Source Intelligence), and other social media related artifacts and tit-bits. Echosec can also be very valuable when investigating a pre, and post attack crime, seeking out, what I refer to as Objects of Intelligence Interest (OoII), and thus can become very complimentary to any SOC (Secure Operations Centre) or CSIRT (Computer Security Incident Response Team) operation when responding to an event. That same observation is equally applicable to the work of the Expert Witness – in 2015 I utilised this tool to some excellent effects to identify social media footprints in support of an International Case I was representing. As an example, for another use – this is a tool which has been used to track down runaways, and other varieties of missing people by monitoring their movements and associations in the world of on-line conversations. Again, this is another highly functional multipurpose tool, which is only limited by the imagination of the user. Then consider the associated low cast, and thus the reason why it is on my list.
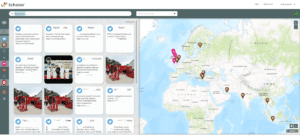
Show below is Echosec in Operation
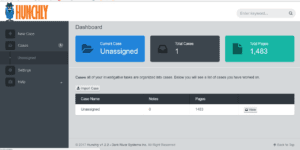
HUNCHLY: My final selection in this article is that of a tool I can’t now live without – called HUNCHLY (https://www.hunch.ly/). One of the problems when investigating on the web is keeping track of all those URL’s one may visit during a week. And it is here where recalling that ‘interesting’ link you stumbled on what not be easily located through the normal search mechanisms. Enter this high functionality tool. Running HUNCHLY on localhost:9999 will assure that you keep track of all your visits – but even more valuable is the fact that you may create case files within the application, thus ensuring that your visitations and collections are specific to the case in hand. For me this one of the most useful feature of this unique tool is, it can compile and generate reports based on the investigation scope – and it can be a life saver. I am also looking forward to adding this into the new 2017 Meirc Digital Forensics and Investigations courses to be run in Dubai, and am anticipating positive student feedback. Shown below is the dashboard of this very useful tool.
The HUNCHLY Dashboard
Conclusion: No matter teaching, training, investigating, or performing Expert Witness support, the user must be enabled with a trusted set of robust tool to underpin the operation in hand – in support of producing a robust outcome. And with tools like those I have introduced above, they may not do it for you – but will most certainly add value to your productivity, effectiveness, and the outcomes of the case, or mission.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



