What has become so obvious during the sad events unfolding in Ukraine is the power of OSINT, discovering the facts through available multiple sources of verifiable intelligence – ranging from social-media titbits, images, news items, and other sources of intelligence born out of Flight Tracking applications, through to MetaData, and EXIF data extracts. For example, at Fig 1 is a display of the flight path of Military Aircraft which are clearly supporting the missions to defend those impacted by the illegal war of the Power Mad, warped Russian leader, Putin.
Fig 1 – Aircraft Tracking – Here US Airforce Boeing RC-135V Rivet Joint
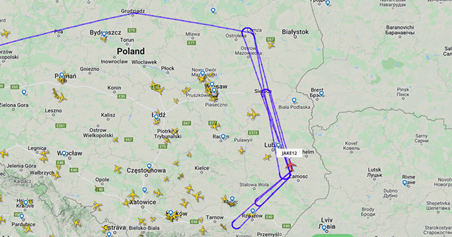
Clearly, because of the availability of such data as shown above, it is possible to drill down further to the discover the operability and capability of the aircraft, and to identify other connected information such as base of origin and flight time. Of no surprise, in the case of the Soviet aircraft, they are not detectable by such OSINT capabilities, possibly because they take steps to stealth their air movements – masking or by corrupting their transmitted signal – maybe we should take note, and do the same!
The other angle of the world of OSINT is to discover, and/or secure digital assets by discovering their potentials for vulnerabilities and security weaknesses, before that is, they are discovered and exploited by hostile actors. Or maybe, such a function could be used to run a Health Check on an asset, pre-use, or post some form of security concern. In the real-world example given here, post a client contacting me with some concerns over the activities associated with their account on the domain, I conducted a very early triage of the situation. First step was to confirm that the company in focus was real, and had a good trading record and reputation, which was confirmed as a very well respected, global trader. OK, so the next step was to look at the Digital Footprint of the company, and its relationships, and here the very credible, powerful tool provided by BrechAware was employed (https://breachaware.com) – which, believe it or not, at time of writing may be used completely free of charge!
At Fig 2 below is an example of the overall health of the domain’s digital footprint state of Digital Health as pulled down from the BreachAware dashboard:
Fig 2 – Digital Asset – URL Health Check
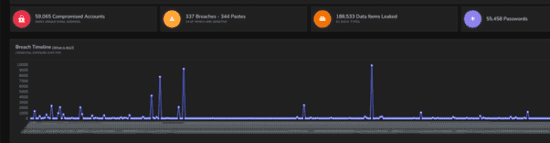
As can be seen from the screen scape shown at Fig 2, discovering:
- 59,065 Compromised Accounts
- 337 Breaches
- 344 Pastes
- 188,533 Data Leaks
- 55,458 Password Security Issue’s
Based on the aforementioned data, it may not be surprising that there are some security concerns raised related to the said URL, showing a profile of a domain which may be classified to reside in the HIGH-RISK bracket. Why? Just the volume of data would indicate they have been compromised on multiple occasions. That would be based on the sheer volume of data sets which have been exposed. It is also assessed to be of concern to discover such a high amount of pasted data, which indicates that the stolen data has been commercially maximised and then circulated to other forums, when the worth of the object diminishes, and thus ends up dumped on a Pastebin. This situation should be a concern for any client!
It is not unusual to discover email addresses and passwords, however, when usernames and payment history are in that volume, action should be to invoke audit mode and to run your remedial cyber security mitigation process without delay.
Looking at this data set from another angle through the eyes of OSINT, there were several complementary discovers and associations by associated Malicious IP addresses, Blacklisted Internet Names, 273 CVE MEDIUM Vulnerabilities – for example, CVE-2012-6708. See Fig 3:
Fig 3 – Present CVE Vulnerabilities
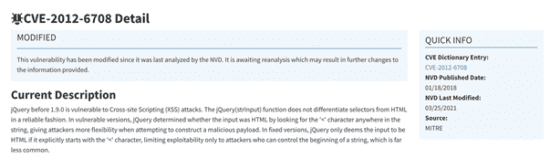
The other areas of interest were 18 mentions on the DarkNet, and High-Risk exposures such as Unencrypted Password entry pages, and we soon start to arrive at the point of impression that this deployment needs some urgent attention.
What is so very interesting here is, the full-blown service of BreachAware provides the user the real-time monitoring capabilities to discover such exposures – leaving one to wonder why this no brainer is not in place for all organisations who care about their Security Posture remaining, well, secure!
The other element of the power of OSINT is the extraction and investigative capabilities of speciality tools – in my case, PALISCOPE (https://www.paliscope.com) which arrives out of their HQ in Sweden. Where to start to describe the capabilities of PALISCOP and its high functionality capability twin YOSE is difficult, as they are so comprehensive. Ranging from identification of individuals and scraping data from social media, through to other powerful capabilities which allow the OSINT Practitioner or Investigator to extract EXIF data from an image, and then conduct a discovery across the Internet to discover any other such images which have the same EXIF, shall we say DNA structure – which may be extrapolated to discover the concerned party, and possibly through other OSINT techniques in the tool to discover the very front door of the actor or concerned perpetrator. At Fig 4 below is an example of the PAILSOPE interface:
Fig 4 – PALISCOPE Interface
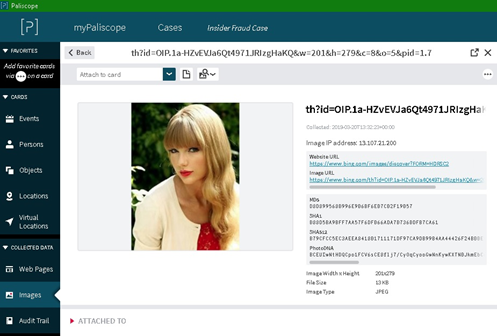
As can be visualised from Fig 4, the power of discovery is enormous, which also provides me with the ability to carry out Contemporaneous Reporting (at the time), as the tool captures the case history and events as they are discovered or annotated and writes them to the associated case file, allowing a single view of the truth to be achieved.
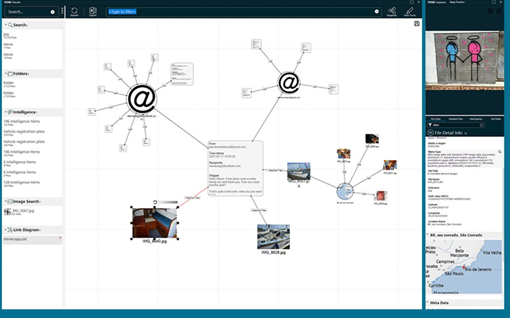
The other tool worth mentioning which I employ is YOSE. As an example, YOSE provides the OSINT capabilities to conduct analytics of desperate objects such as email, files, images, documents, and by the power of the embedded algorithms, then links the objects by a form of aggregation, provisioning intelligence out of fragmented information, and then displaying the associations via a representative image showing the connections and relationships – See Fig 5:
Fig 5 – YOSE Extraction of Intelligence
Conclusion
OSINT has been standing in the wings now for many years now, but has been slow on the uptake of many within the Commercial and Industrial Sectors – and yet, its power is proven, and can provision the before-the-fact defensive capabilities which range from discovering any hosted security vulnerabilities and point of potential exploit, before they are leveraged by a malicious actor, though to provisioning after-the-fact power in your digital toolset to run coordinated investigation, and incident response capabilities to discover, aggregate and map Objects of Intelligence Interest (OoII) down to a finite discovery of interlinked data sets.
We may also look to the many other OSINT services which are available in 2022, such as Leicester based Bellingcat (https://www.bellingcat.com) who provide verified OSINT Intelligence on a rage of subjects, from MH17, the Ukrainian War, and other reported on, say the subject of Terrorist Gangs.
It may be today, you organisation, department, or even Police Force are not leveraging the power of OSINT – if this is the case, the year is 2022, and maybe it is time to think again.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



