For more years than I care to recall, I have been on, what has seemed like a crusade to spread the word about, what we now understand to be the Cyber Threat that our interconnected, IoT driven world faces. On my crusade, spanning over 30 years + I have had negative encounters, knock-backs, faced criticism, been called a nutter (possibly true), and have been referred to as a scaremonger who does not understand the reality of the topic. The following scenes taken from such encounters will hopefully go some way to convey my built-in sense of utter frustration as to why we are where we are today in the centre of a very critical and successful state of cyber adversity. However, prior to dishing, I would wish to thank one lady who has refreshed my belief in the existence of vision, insofar as there are some in this big wide world who fully appreciate the implications of what cyber-insecurity really is – and that inspiration came from Nicole Perlroth, author of ‘THIS IS HOW THEY TELL ME THE WORLD ENDS’ – a must read for anyone who is really interested in what Cyberwarfare looks like face up (ISBN-978-1-5266-2985-2).
So, let me start to tell of my 30+ year Crusade. I guess the very first hard rejection was when I read about the discovery of the new phenomenon of the Computer Virus in the Sunday Time – Circa mid-eighties. At that time, I was serving in a post of IT Security at a very sensitive RAF site which enjoyed direct connection to GCHQ/CESG. Post reading some early research on the subject by Fred Cohen, and the work of Ralph Burger ‘Computer Viruses – A High Tech Disease’, I was of the opinion that, here we were seeing the early leading (bleeding) edge of a new-age danger to computer systems of all shapes and sizes – and with the predicted growth of the PC, felt it was a matter of National Security importance to bring my concerns to the attention of the connected agencies. Using the site-to-agency closed network Homebrew System, I shot off a signal covering the detail of my concerns. After a few days, eventually a communication was alerted on the green screen VDU from CESG in the form of a response. It said ‘Thank you for your communication on this matter. However, CESG consider the Computer Virus as just a passing nuisance’.
As I moved into a new role, as Systems Security Manager inside one of the most cyber-secure environments known to man, a SCIF (Sensitive Compartmented Information Facility) which was not accommodated with any form of insecure external links, and with voice systems which were in place to support sensitive international, and national Calls – over the STU-II (Standard Telephone Unit II). In this period, whilst we never encountered a single malware (sorry Virus) incident, I observed from my secure domain the progress of nuisance of the computer virus start to make its presence known to the world – think again CESG!
In 1997 I move on from the military after serving 22 years in the role of Counterintelligence – working alongside various Agencies on both sides of the Pond, in what was (is) referred to as the Envelope – it was in the era of entering the Commercial World in which I noticed a distinct decline in, what was considered adequate Computer Security when compared to the Military.
When working as a Security Manager for a well-known Global Automotive Brand, I saw the first indications of recklessness was. The incident in question was an unauthorised server had been discovered which had been connected to the operational network, serving external, unknown parties who could log in to participate in the sharing of topical information of interest to the group – that information was in the domain of Paedophilia – an event which had been notified by a Whistle Blower. However, notwithstanding the connection of the server was a serious breach, and that the server potentially held the details of dangerous actors at large, the only interest expressed by the company was as to who had blown the whistle (this was never divulged) – I was the only one who knew the identity. The fix to remove this danger from the Risk Register was simple, to bury the bad news out of sight of anyone, internal or external to the – it never happened!
Around 2005 I was attending a dinner at the Hurling Club, when I got into a conversation with a Senior Member of CPNI (Critical National Infrastructure), which moved into the topic of the dangers posed by Cyberwar, and Crime (eCrime) – but the response I received was surprising, concluding that ‘It is people like you (me) who act as scaremongers – the threat does not pose the level of danger that is being suggested’. With mouth open, I walked toward my table and gave a toast to the redundancy of wisdom and foresight I had encountered with a glass of thick, sticky Victory Gin, Vintage 1985!
When in the employ of a new position with a well-known Credit Reference, I was caught in the crossfire between two Security Directors in conflict, both of same grade (A), who had been morphed into a power struggle for supremacy (between the CISO, and the Director of Risk and Compliance). At the high point of this battle, the CISO decided to walk out from his office, go to the local Dixon’s (IT retailer) and to purchase a Laptop. Upon return to the office, this machine was used to onboard data from the CISO’s Network Drive and Desktop PC – after which he disappeared for several months. Whilst this was reported to the Director of HR, no action was taken, and notwithstanding all the departmental, upstanding IT Security Professionals were aware of this serious breach by a trusted security professional, after a resolution was found, the CISO simply returned to his role, and carried on as if nothing had occurred! That said, the same company had previously lost a laptop containing the account details of 35,000 Barclays Bank customers in unencrypted format, which was never reported to the bank, or under any other mandated, seemingly unheard of process such as PCI-DSS, and one other debacle which was presided over by a Technical Board Member in the post of Change Management and a Senior IT Security Professional who, to deploy an Anti-Virus update applied open permissions at the NT Domain Controller (DC) to facilitate domain wide access to around d 10,000 connected PC’s. This unremarkable act had not considered, this change cannot be reverted by a simple reapplication of rights at the DC. It was only when the Security Departments phones started to ring off their hooks to report the fact that users could see data on other people’s drives – including the Director of HR!
Coming up to 2010, I was a delegate at the Conservative Party Conference, and was attending a Manchester meeting to hear the plans of James Brokenshire MP being presented about Cyber Crime. During the conversation, the subject of Gary McKinnon came up, regarding the hacking into several US Government Servers. Disagreeing with the context of the discussion, I commented ‘In my opinion he should be paid for what he has done for US Security’, followed by a rebuff of ‘what a stupid thing to say’ – I returned on my verbal challenger with ‘Gary alerted the system owners with an entry in the log of RTFM (Read The F******* Manual) which in my opinion was better than accommodating Chinese Hackers with extant, unknown access’.
In was around 2007 when I attended a Dinner at the Ritz in the company of John Thompson (CEO of Symantec), Margret Moran MP (Representing EURIM), Mark Prichard MP, and my Dining Partner Theresa May MP. The thrust of the evening was for John Thompson set out the Symantec position as to how they (we) were winning the Cyber Threat – a theme that was also followed by the McAfee Security Scientist during a TV interview. Whilst those who sat at the table were happy to be fed the exquisite food, beverages, and the words of our host – one was not, me. I challenged what was being presented as an inaccurate status, arguing that we (the good guys/gals) were very much in a serious position – went down like a bomb. Some years later I was speaking at an event in Nice, which was also attended by Mark Pritchard MP, and we shared a cab back to the Airport. During the journey, the much-travelled MP recalled the event at the Ritz and said to be ‘Do you remember that bloke who was banging on about security’ – Yes, I replied, I do! I could tell by his face; the penny had dropped as to who he was sharing a taxi with!
Circa 2012, when I was commissioned by a company based in Helsinki to support their activities researching the aspects of the AET (Active Evasion Techniques) which was basically around presenting the 7 Layer Stack to the defending Firewall in such a way, it would obfuscate the logical presentation of the packets to confuse and compromise the device, to gain access to the supposed, protected network – using and old, well known piece of Malware to create a shell condition. At that time, McAfee protested, as their own Firewalls were one of many that were laid to waste with this attack – decrying the research as flawed. Funny old thing as it may be, in 2013 McAfee acquired the company for $389 million in cash!
When there is a move to understanding of the combined power of, what can be overlooked, such as the power of OSINT, the implications of DNS exposures and exploitation, the potential hand-crafted exploitations which may be achieved through widely available utilities like the Unix/Linux command line tools, one example of which is dig. It is also a valuable life cyber-defence skill to appreciate opportunities, of what can be a regular chance find of an open Zone Transfer which may be leveraged to dump out a text based file, discovering what are supposed to be hidden assets in the form of servers on the supposed protected side of a network. For example, consider an OSINT dig against a target domain – Tld, which then further discovers a further, for example, 6207 internally linked URL’s, or 1357 externally linked URL’s – it may be then we will start to understand the Cyber Theatre of technological risks we face on a day-to-day basis, and hopefully move from the back foot toward the front.
As my late, great friend, Steve Gold (RIP) shared re an interview he had conducted with a German Hacking Group. Steve asked them how they had got so very cleaver are honing their skills to compromise multiples of secure companies. He was taken aback when one of the hackers responded, we are not that cleaver, it is just that others are so stupid applying what they consider to be security – in my opinion, a very good assessment.
Conclusion
The real-world, first-hand encounters are just a small selection drawn out of a big black bag of such dire events. The question is, now with the contribution from hindsight, and power of teaching from the last 2/3 decades of adversarial cyber experiences, how does the world of Cyber Security stand up to the litmus test in 2021? Whilst I would rejoice to say, the strategic approach is very much on the front foot, nothing could be further from the truth – fact is, we are now in what I, and many others consider a very vulnerable, insecure digital world – we have morphed from the digital dangers of, what was a simplistic creation of the Brain virus (Image 1) by example, into the dangerous world of Stuxnet. To win this Cyber Battle we also need to hone the skills of the Cyber Knights and arm them with combatant knowledge and tools to fight-the-good-fight. We must evolve the material value of the CISO role, move it away from the political posturing of managing security, and fulfil the requirements of the post with a much more, in depth grasp of what the Cyber Threat is in technical terms, and underpin a response accommodated with a technological level of appreciation. As for honesty, integrity, one may only hope that comes along as an asserted expectation.
Image 1 – The Early Brain Virus

And consider those who call themselves Digital Transformers – have they not considered the consequences of extending the complex wired world into an even more complex place – as we can see clear evidence that, what we have deployed is not robust enough to secure such services. And when we look at some of the work carried out testing site security which has discovered test-on-test PKI infrastructures full of holes, insecure, outdated, or surplus Digital Certificates embedded in Critical Sites, and companies who deliver Critical Infrastructure completely open to abuse in the form of an awaiting digital key, which may be turned to grant access as, and when required. However, with the value of the exposures out of the Snowden exposures, which notified the world that the US Agencies were spying on subjects who may be come to their attention – leaves me with a question! When you inform UK National Authorities who are supposed to be looking after the Cyber Security Posture, do such embedded Digital Certificates facilitate such agencies with the potential of extant access to such compromised site?
When I think on those in CISO roles of National Critical Services, who not only deny the adverse state their technology they are hosting, but even more worrying, when you look back at the long track record of some individuals, you see a documented trail of previous data and system breaches at each company the person has worked at – just what does that tell us?
But the absolute bottom line is the work of Nicole Perlroth in her excellent book – in which a person who has only been involved with the world of cyber for a very short period (her words) has come up with the most important observations of the day. Perlroth outlines that the attacks on the Ukraine, whilst a lesson for the state for turning their back on Mother Russia were a payback, they were also a training ground for Russian Hackers to create their Run Books for the future of large-scale Cyberwarfare on the US and other Nation States. The book introduces the in-light of day implications of NotPetya, and the impact it had on the world. Above all, what we have missed here is, the day Obama’s Government took the lid of the Cookie Jar and released Stuxnet on the world, introduced the new world order for what is acceptable in the Digital Underworld Theatre of Warfare.
When you add the laissez-faire attitude, which is shown to the need to robust Cyber Security Postures, aligned to the successful growth of the cyber criminals and state-sponsored actors who are now at ply in most networks in the world, linked to the failings of Third-Party Security Service Profilers such as SolarWinds, and Qualys etc, the overall picture looks very bleak indeed.
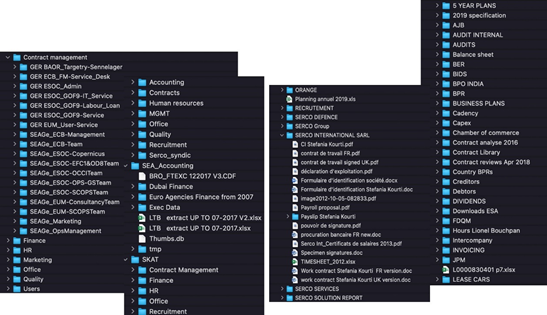
As a conclusion, and example of what is a damming indictment in real world terms. In Q4/20, serco were informed their site was running with multiples of HIGH, MEDIUM, and LOW Risk Vulnerabilities, along with data leakage at various points of their own, and client’s data – linked to serious holes within their deployed Digital Certificates. After informing the company, a few emails passed, and their CISO and DPO informed the sender they took security very seriously. In Q1/21 serco once again suffered a security breach at the hands of the Babuk Gang, placing the data of the European Space Agency, and many others potentially exposed, as data had been posted on the DarkWeb. The concluding worry is, if you have a track record of multiples of cyber security breaches, and even when informed fail to act, it does tend to reverse the question of ‘how do these things happen’ to ‘so this is how Cyber Security Breaches happen’ – Image 2 below is example of the data that was potentially compromised out of this failed security teams, supposed secure posture.
Image 2 – The Exposure of Data
So, time to change the approach, has, in my opinion passed its sell by!
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.


