Attending conferences and trade shows is a luxury many of us cannot afford, both from the time and expense perspectives. Compounding that fact is that many of the larger events have devolved into long-form vendor showcases, more closely resembling the International Auto Show than the educational and invigorating experiences they purport to be. These mega events are also very costly, due to travel costs and skyrocketing price of admission in the thousands of dollars.
Fortunately, many local events have sprung up for the security professional, such as local OWASP and ISSA chapter meetings, Security BSides, and many others. The cost of admission is often less than $200 and little to no travel is required for many attendees. These events are far more intimate, and the content tends to be much more compelling than the mega events that are so far out of reach.
With that in mind, I decided to attend THOTCON 0x6 in Chicago. From the THOTCON.org site:
In case you didn’t get the in-joke, 0x6 is the hexadecimal representation of 6, denoting the sixth annual event.
The two-day event is packed, and heavy on hacker culture, not just pure information security. The event included two talk tracks, a small Village (more on that later), and an interactive, hackable badge.
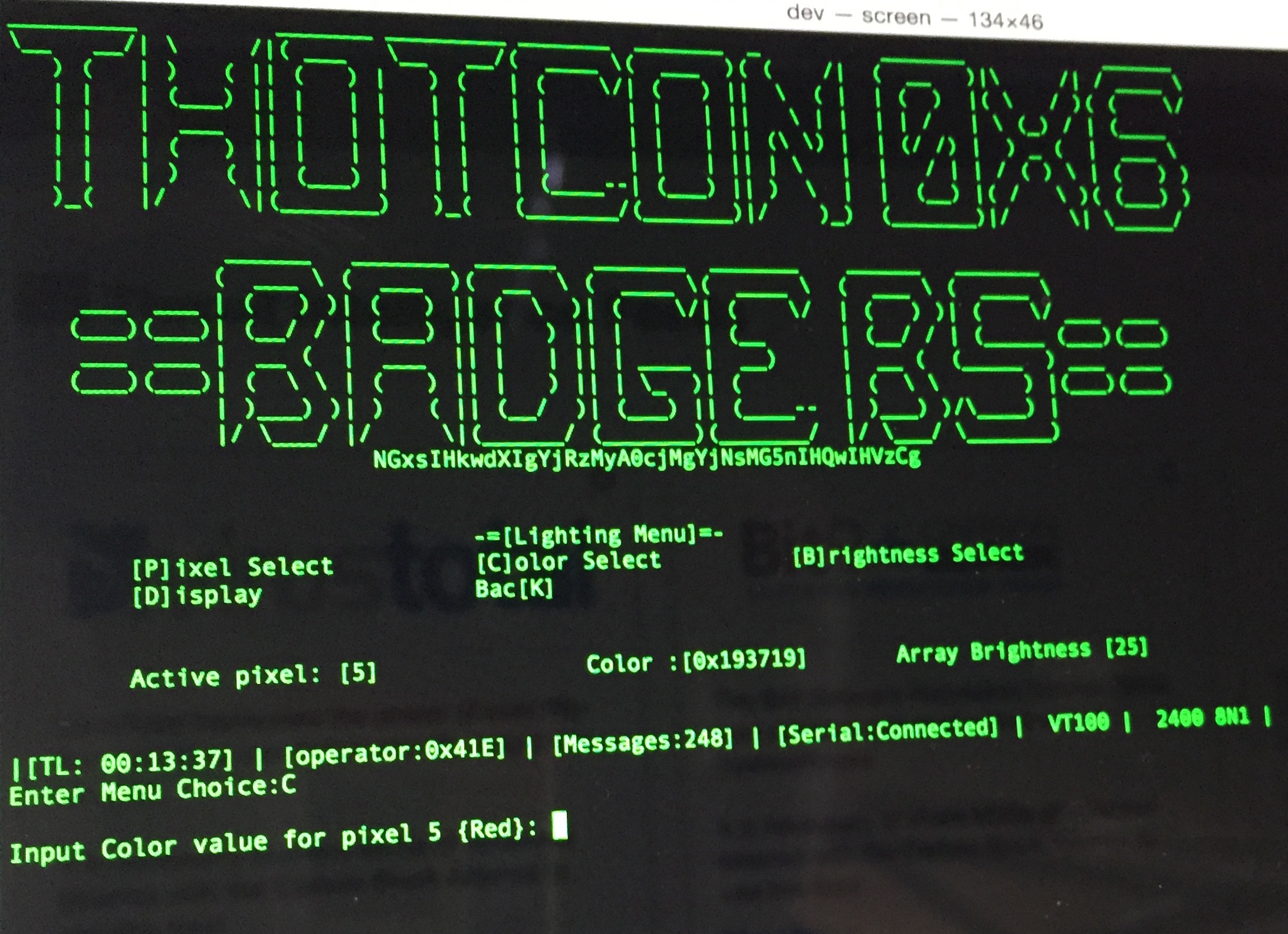
THOTCON 0x6 interactive badge
The terminal screen when connecting to the badge via USB can be seen below.
Terminal screen accessing the badge via USB
THOTCON is a jam-packed two days and, unfortunately, it’s impossible to experience all of it. It carries over directly into BSidesChicago, held over the weekend, so there’s no shortage of good talks and activities. I stuck mostly to Track1, which included keynotes and other 50-minute format talks. Track2, held simultaneously, was for 25-minute “turbo talks.”
The opening keynote by Chris Valasek (@nudehaberdasher) of IOActive kicked the event off with a bang. His presentation was peppered with humor and high energy, as he held forth on the higher stakes of hackable systems such as cars, planes, medical devices, and other systems. Valasek is well known for his research with Charlie Miller (0xcharlie) into the vulnerable systems of cars, and dove into the details of their findings.
So-called stunt hacking has been in the news a lot lately, most notably Chris Roberts’ audacious and irresponsible claims of hacking avionic systems in flight via vulnerabilities in the in-flight entertainment systems. While the true story of in-flight avionics vulnerability remains unclear, the vulnerable nature of automotive systems in the Toyota Prius and Ford Escape is well documented by Valasek and Miller. Some in the infosec community claim Roberts’ sort of stunt hacking lacks tangible value, aside from drawing headlines and audiences at security/hacker conferences.
However, Valasek argued compellingly that research in the area of vehicles and other similar systems is critical for a safer future. Realistically, the exploits demonstrated require physical access to the vehicle, greatly reducing the risk of malicious use. Automotive systems are increasingly accessible via remote mechanisms such as Bluetooth and WiFi cellular hotspots. With this trend in automotive system technology accelerating, it’s only a matter of time before remote exploits are possible. Researching these systems responsibly now makes it more likely they will be better designed with security in mind. Currently, automotive systems are essentially one, big trusted system, including Bluetooth and iPod integrations, and they lack any notion of logging, detection, or monitoring.
From there, the talks ranged all over the map. Some covered advanced topics, such as Ryan Linn’s (@sussurro) deep dive into forensics and the digital footprints left behind by penetration testers, and Jeremy Richards’ rabbit hole on firmware reverse engineering. Other presentations took advanced topics like cryptography and simplified them, such as Jon Callas’ “Everything You Need to Know about Crypto in 50 Minutes.” Steve “nosteve” Ocepek’s proposal for better visualization tools and dashboards was wildly entertaining and gave us a glimpse of how videogame nostalgia inspired an interesting new tool for spotting anomalies in TCP dumps. If you can’t quite imagine what such a tool might look like, head on over to GitHub to check out nosteve’s SYNspot project.
I was impressed by the turbo talk David Shaw delivered. Facing the infosec skills shortage that my friend David Holmes covered earlier this year, Shaw has founded a project called SecGrowth aimed at connecting infosec mentors with individuals seeking opportunities to break into a security career. As with many other talks at THOTCON, Shaw’s timeslot was scarcely enough to scratch the surface, but he proposed a solution to this pressing problem.
The Village, hosted upstairs, featured a lock-pick station and 3-D printers, as well as a craft brew contest. Nearby, many attendees could be seen plugging into the USB port on their badges, altering the LED colors and digging into what other capabilities it held. My friend and I got a kick out of making our badges look like Tony Stark’s arc reactor.
THOTCON isn’t the only event of its kind, as I mentioned in the opening. After attending, I can definitely say that I’ll seek out opportunities to attend similar conferences such as NOLAcon, DerbyCon, and others.
Did you attend THOTCON? If so, I look forward to reading your impressions in the comments below. Which other local security conferences do you attend?
[su_box title=”About Brian A. McHenry” style=”noise” box_color=”#0e0d0d”]
 Bio: As a Security Solutions Architect at F5 Networks, Brian McHenry focuses on web application and network security. McHenry acts as a liaison between customers, the F5 sales team, and the F5 product teams, providing a hands-on, real-world perspective. Prior to joining F5 in 2008, McHenry, a self-described “IT generalist”, held leadership positions within a variety of technology organizations, ranging from startups to major financial services firms.
Bio: As a Security Solutions Architect at F5 Networks, Brian McHenry focuses on web application and network security. McHenry acts as a liaison between customers, the F5 sales team, and the F5 product teams, providing a hands-on, real-world perspective. Prior to joining F5 in 2008, McHenry, a self-described “IT generalist”, held leadership positions within a variety of technology organizations, ranging from startups to major financial services firms.
Twitter: @bamchenry[/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.