Do you break down firewalls on a daily basis? Exploit vulnerabilities in your sleep? Crack through encrypted websites like it’s nothing? Do you do it all for the good of the people? If you answered yes to all four questions, you’re an ethical hacker—or you’re pretty darn close to one. Chances are though, that you don’t know everything that role entails—and chances are you want to know more. But no worries. Information Security Buzz and TrainACE have put together a top ten list of tips that any aspiring ethical hacker (or current one for that matter) will want to keep in their arsenal.
[wp_ad_camp_4]
1) KNOW all operating systems. Unlike humans, all operating systems are not created equal. No two Windows updates are the same, nor will a Linux vulnerability be identical to an OS X one. If you want to hack, and hack well, you’ll have to do some research. An OS can affect the feasibility, methodology and impact of an exploit. Knowing your way around an OS directory and its commands is a BIG must. Covering tracks and editing files are largely important techniques while hacking. If you don’t know where specific logs and system files are, you risk the chance of being caught by incident response teams. If you take the time to learn the commands and directory layouts of all of these operating systems, you’ll save yourself a lot of time and energy once you DO actually get into a system.
2) KNOW a little bit of everything. When hacking, it’s important to have a skill set that expands past the general script kiddy exploit. Being proficient in areas such as coding and scripting, knowing the languages of Python, Ruby, C and Perl, and having other general IT skill sets like network security and network analysis will improve every aspect of ethical hacking. Being able to see what’s happening on the network and writing your own exploits or scanners can be the difference between you getting caught in a DMZ or being able to get the information you wanted.
3) KNOW your network. If you’re going to strike a network, it pays to know as much about it as possible before you attack. Find out your network, how it’s set up and figure out an attack vector. Then write down what you’re going to do for every attack vector. While it may sound tedious, it’s extremely helpful. This will help you keep all of your steps nice and neat so you don’t forget what you have actually done and what you still have to do. Additionally, this will prevent you from going back and repeating the same steps over and over, wasting time trying to figure out where you were in your attack. Be warned, repeating tasks can cause a lot of unnecessary and obvious traffic, potentially exposing your agenda.
4) KNOW your tools! Understanding the tools you’re using, how they work and what they do will play a major role in getting them to work. If you don’t know how to use your tools, you can seriously damage things. You don’t want to attempt a stealth scan but end up with a highly active scan because you used the wrong nmap options. Tools are unpredictable; they can either be easy to us or finicky. If you don’t know a tool or the options it has, you may end up doing something accidently, or not getting anything done at all. It’s vital to ensure that the tools you are using are indeed tailored to what you are trying to do.
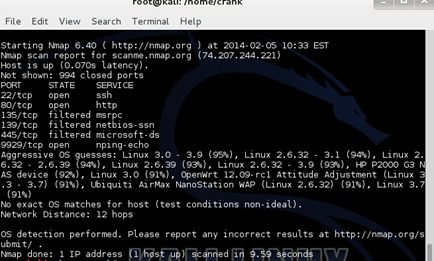
*An Nmap scan. Nmap is a network mapping and scanning tool, you can find more info at www.nmap.org
5) KNOW an alternative approach. Thinking outside of the box is a skill that separates a good hacker from a great hacker. When you attack a system differently than it what is expected, it makes it a lot harder for your attempt to be seen. If you can create a way to exploit a system or a network that is unique to you, it will make your exploit, and everything contained in it, harder to find. Having a unique attack vector isn’t necessary, but it definitely makes a huge difference. Start brainstorming! Think of multiple ways to get your exploit on to the system you are trying to get in to. When you have a unique attack vector, it makes it extremely difficult to find the origin of the exploit, because traditional tactics are usually focused on during a primary level investigation.
6) KNOW that you must document everything. If you’re hacking for a client, they’ll probably want to see a breakdown of what you did. There is nothing more frustrating for a client than getting a report that does not give enough information on how to reproduce an issue or how you carried out your testing. Even worse is the possibility of a client asking for further details about a test or particular issue, and not being able to produce the data for them because you no longer have it. Notes and screenshots are your best friend. Additionally, save everything. Save your tools’ output, logs, the arguments passed to those tools, and even all of your network traffic to and from the target(s). While it may add to your workload, it’s a smart move that verifies all of your hard work.
7) KNOW how to communicate with managers, developers and project managers. While it’s great that you’ve exploited a Blind SQL Injection vulnerability, managed to get shell and exfiltrated the users table, ultimately this means nothing to a CEO or high level manager who doesn’t understand the language you’re using. You can be the best hacker in the world in terms of technical ability, but if you can’t communicate effectively with your peers, managers or clients, then your findings become a lot less valuable to everyone.
8) KNOW how to get involved with the community. While keeping up with absolutely everything in the security industry is pretty much impossible, take the time to get involved in a few key groups that provide informative and innovative content that you can apply to your own projects. By getting involved you’ll get to know other hackers, keep track of what’s happening in the industry, and discover new tools—all things that will ultimately give you an edge over your peers. Start now! Get on Twitter, Reddit’s netsec, forums, go to cons, participate in CTFs, and contribute to Open Source! Get involved!
 *Meet-up groups are a great resource to connect with other members of the community and exchange ideas and advice.
*Meet-up groups are a great resource to connect with other members of the community and exchange ideas and advice.
9) KNOW how to exploit a bug when you find one. Finding a Cross-Site Scripting (XSS) issue is nothing to brag about (unless in a very high profile application). What really matters is to demonstrate why that vulnerability is an issue, and to show the true risk by exploiting it. Turn ‘XSS’ into ‘30,000 User Accounts Compromised via XSS’ by putting the extra effort into exploitation. Any monkey with a computer and time on their hands can find XSS, but it takes some skill to effectively exploit it.
10) KNOW how to do your own research. Don’t just rely on other people’s tools and research; do your own too. There is never going to be a tool for every situation, so create your own. Found something new or interesting? Research it and share the results with the rest of the community so that they can benefit from it too.
Author Credit:
Ryan Dewhurst is an ethical hacker, security blogger, and security engineer for Random Storm. You can follow him on Twitter @ethicalhack3r
Christian Crank is a subject matter expert and security researcher for TrainACE’s cyber security branch, Advanced Security. You can follow him on Twitter @crankadv_sec.






