With news that the UK energy sector is likely to have been targeted and probably compromised by hackers, please see below for comment from David Emm, principal security researcher at Kaspersky Lab, and relevant statistics from Kaspersky Lab research.
“The world isn’t ready for cyber threats against critical infrastructure, but criminals are clearly ready and able to launch attacks on these facilities – as the widely-speculated compromise of the UK’s energy sector shows. We’ve seen attempts on power grids, oil refineries, steel plants, financial infrastructure, seaports and hospitals – cases where organisations have spotted attacks and acknowledged them. However, many more companies do neither, and the lack of reporting these incidents hampers risk assessment and response to the threat.
“Security must be tailored to the specific needs of each organisation and be seen as an ongoing process. This is true also of the human dimension – tricking people into taking action that launches the initial exploit is as common in attacks on such facilities as it is in any other context.” David Emm, principal security researcher, Kaspersky Lab
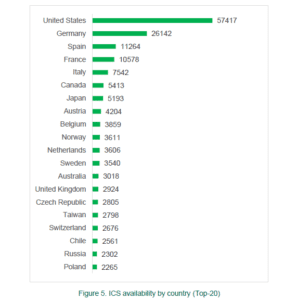
Last year Kaspersky Lab released its report on the Industrial Control Systems (ICS) threat landscape, which revealed that large organisations likely have ICS components connected to the internet that could allow cybercriminals to attack critical infrastructure systems. One of the interesting findings was that the majority of ICS components connected to the Internet are located in the United States.
The investigation found that 17,042 ICS components on 13,698 different hosts exposed to the Internet likely belong to large organisations. These include energy, transportation, aerospace, oil and gas, chemicals, automotive and manufacturing, food and service, governmental, financial and medical institutions.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



