Critical vulnerabilities discovered in Symantec and Norton security products. Here below Chris Wysopal, CTO and co-founder at Veracode, reflecting on how security software is second to worst category of software for application security.
Chris Wysopal, CTO and co-founder at Veracode:
“The critical vulnerabilities discovered in Symantec and Norton security products are not a surprise – Veracode’s State of Software Security v3 (SoSSv3) report shows security software is second to worst category of software for application security.
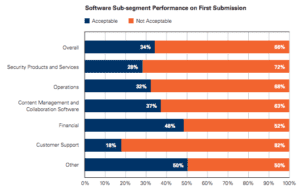
And in general the code you buy is worse than the code you build because the operator of the software retains all liability not the software vendor. This is why security conscious organisations typically build more secure apps than the apps the buy like security software. From SoSSv6:
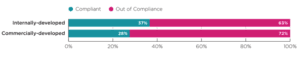
Security software vendors hire from the same pool of developers who in general have had no security training in college or on the job security training. To make things worse security software is typically written in the C/C++ which has more critical vulnerabilities like buffer overflows and integer overflows than more modern type-safe languages like Java, C#, or Javascript. Another thing that makes vulnerabilities in security software worse than the average software is it often runs at a higher privilege level so it can inspect the data going to and from other applications. When a vulnerability is exploited it often means complete system compromise. The operations security software is performing often require complex parsing and pattern detections which is typically complex and bug prone code.
All these things add up to making security software an attractive target for attackers. Vulnerabilities are plentiful and the software is running with elevated privileges. I’m surprised we don’t see more disclosures around security software. Perhaps more bug bounties are needed in the security software marketplace.”
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



