On Friday 12th May, organizations across the world were hit by a massive ransomware attack, named WannaCry, which exploited a (now patched) Microsoft Windows vulnerability revealed in the Shadowbrokers dump on March 14.
Kaspersky Lab researchers have continued to track the evolution of the threat over the weekend.
Evolution of the ransomware
The total number of variants in circulation on Monday 11th is still unclear – but over the weekend two notable variants emerged. Kaspersky Lab does not believe any of these variants were created by the original authors – most likely they were patched by others keen to exploit the attack for their own ends.
The first one started spreading on Sunday morning, at around 02.00 UTC/GMT and was patched to connect to a different domain. Kaspersky Lab has so far noted three victims for this variant, located in Russia and Brazil.
The second variation that appeared during the weekend appears to have been patched to remove the killswitch. This variant does not appear to be spreading, possibly due to the fact it has a bug.
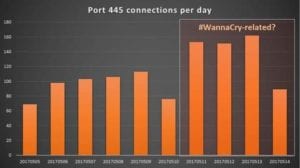
Number of infections to date
Further analysis of network logs suggests the WannaCry ransomware may have started to spread on Thursday 11 May.
It is difficult to estimate the total number of infections. Our own telemetry indicates that over 45,000 users have been attacked, but this represents a fraction of the total numbers of attacks (reflecting Kaspersky Lab’s customer share.)
A more accurate picture of the world situation can be drawn from the sinkhole for the kill switch hardcoded in most versions of WannaCry: Currently the Malwaretech sinkhole, which is collecting redirections from the ‘kill switch’ code, has registered about 200,000 hits.
It should be mentioned that this number does not include infections inside corporate networks where a proxy server is required for connecting to the internet, meaning that the real number of victims might easily be larger.
Since 06.00 UTC/GMT on Monday 15th May, Kaspersky Lab has noted about 500 new attempted WannaCry attacks across its customer base – by comparison, on Friday 12th there were six times as many attempts during the first hour alone. This suggests the infection may be coming under control.
Kaspersky Lab advice to reduce the risk of infection
- Install the official patch from Microsoft that closes the vulnerability used in the attack (there are also patches available for Windows XP, Windows 8, and Windows Server 2003)
- Ensure that security solutions are switched on all nodes of the network
- For those who do not use Kaspersky Lab solutions, we suggest installing the free Kaspersky Anti-Ransomware Toolfor business (KART).
- If Kaspersky Lab’s solution is used, ensure that it includes the System Watcher, a behavioral proactive detection component, and that it is switched on
- Run the Critical Area Scan task in Kaspersky Lab’s solution to detect possible infection as soon as possible (otherwise it will be detected automatically, if not switched off, within 24 hours).
- Reboot the system after detecting MEM: Trojan.Win64.EquationDrug.gen
- Use Customer-Specific Threat Intelligence Reporting services to be informed about possible attacks
- WannaCry is also targetingembedded systems. We recommend ensuring that dedicated security solutions for embedded systems are installed, and that they have both anti-malware protection and Default Deny functionality enabled.
Technical data
A detailed description of the WannaCry attack method, and Indicators of Compromise can be found in the blogpost from Friday 12th on Securelist. An update blogpost will be posted later today.
Kaspersky Lab network logs and data from the SANS ISC (https://isc.sans.edu/port.html?port=445)
The two new variants of the WannaCry ransomware are as follows:
Variant 1: md5: d5dcd28612f4d6ffca0cfeaefd606bcf
Connected to: ifferfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
Variant 2: md5: d724d8cc6420f06e8a48752f0da11c66
WannaCry Q&A
What is WannaCry?
WannaCry comes in two parts. First of all, it’s an exploit which purposes are infection and propagation. And the second part is an encryptor that is downloaded to the computer after it has been infected.
This is the main difference between WannaCry and the majority of other encryptors. In order to infect a computer with a common encryptor, a user has to make a mistake, for example, by clicking a suspicious link, allowing Word to run a malicious macro, or downloading a suspicious attachment from an email message. A system can be infected with WannaCry without doing anything.
What are you seeing in terms of continued expansion? Is it slowing or still spreading rapidly?
We are still observing an increase in the number of infections, which indicates the attack is still ongoing. Compared to yesterday, the number of infections appears to be now about
3 times bigger; this was calculated taking into account new detection methods for the network attacks and several new samples we received in the meantime. Therefore, we estimate about 120-130,000 infections total. A similar number is also offered by malwaretech’ sinkhole project.
(Costin Raiu Director, Global Research & Analysis Team)
Can we say with a confidence that the attacks are now under control?
Wherever there are unpatched computers, there is a risk of infection. Historically, we know that people and organisations don’t necessarily update their systems, even where there is a known exploit for a vulnerability.
(David Emm, Principal Security Researcher Global Research & Analysis Team)
Have you already started to see new variations of WannaCry?
Several new variants have emerged during Sunday and last night, of which only one appears to have gone some very limited traction. The other variants appear to have been manually patched by unknown entities and have not been created by the original #Wannacry authors. For the new variant that appeared on Sunday morning (all times I refer to are GMT), we have seen a very limited number of attacks which included 3 customers, in Russia and Brasil. We continue to monitor the developments and watch for the emergency of any new variants.
(David Emm, Principal Security Researcher Global Research & Analysis Team)
Are there any other new developments?
We are still analysing the attack and gathering more data. We estimate we will publish an update of our findings later today.
(Costin Raiu Director, Global Research & Analysis Team)
We see in the media, comments that the “worst attacks are about to come”. What are your thoughts?
No one can say with certainty that ‘the worst is yet to come’. However, it’s likely that there are still significant numbers of unpatched systems, providing further opportunities for this malware to spread. It’s also possible that other malware might be created to take advantage of the same exploit.
(David Emm, Principal Security Researcher Global Research & Analysis Team)
Where does responsibility lie for these attacks?
The key factor in the spread of WannaCry is the use of the EternalBlue exploit, i.e. that organisations and individuals haven’t updated their systems. However, as mentioned above, malware can spread in other ways too – most notably by tricking people into installing code. So patching systems is vital – it reduces your exposure to attack. But it’s also essential to ensure that systems are protected using Internet security software. On top of this, education of staff is also vital. Finally, good network management will also help to reduce the scope of any attack, i.e. don’t assign admin rights to computers automatically, segment different parts of the network and restrict access to data to those who need it.
(David Emm, Principal Security Researcher Global Research & Analysis Team)
Are there victims who have installed the patch for Microsoft Windows? If yes, how is then possible that attacks were successful?
While the remote attack of systems using the ‘EternalBlue’ exploit is the most significant factor involved in the spread of WannaCry, this doesn’t mean it can’t spread without this. But this would require victims to run the infected code. We know that cybercriminals routinely use social engineering – tricking people into clicking on links and attachments – to spread malware, so it’s entirely feasible for WannaCry to spread this way.
(David Emm, Principal Security Researcher Global Research & Analysis Team)
Why is Russia worst affected?
There are a large amount of PCs running out of date or unofficial versions of Windows in Russia.
Do you have any data showing whether people are paying the ransom, and if they are getting access back?
We do observe multiple ransom payments in Bitcoins for the three known wallets we are monitoring, accounting for about 70 people who paid in total.
Based on the current Bitcoin exchange rate the attackers made about 20,000$ during the first 24 hours. Taking into account our experience in observing BTC ransomware payments, we estimate that the peak will be reached in 24-48 hours from the beginning of the attack, as people need to research ways of acquiring Bitcoins for the payment. We would also want to clarify we do not recommend to pay the ransom, as this only encourages the criminals to continue their activities.
(Costin Raiu Director, Global Research & Analysis Team)
What kind of fallout are people expecting: New regulations, questions about NSA role, etc.?
Unfortunately I’m not an expert in regulations or politics, but I believe an incident of this magnitude will for sure result in discussions and possible special measures being implemented to avoid other attacks in the future. This may have to do with exploit development, safeguarding, usage, export of exploits, Bitcoins, cryptocurrencies, e-payments and patch management.
(Costin Raiu Director, Global Research & Analysis Team)
[su_box title=”About Kaspersky Lab” style=”noise” box_color=”#336588″][short_info id=’59584′ desc=”true” all=”false”][/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



