For most of us, COVID-19 is a cause of great concern, but for hackers, it is a cause for celebration. Since the beginning of the pandemic, cyber security attacks of all sorts have been on the rise with ransomware attacks being attackers’ favorite.
Two independent analyses of the attack vectors used in successful ransomware attacks, carried out by Kroll and Coveware clearly indicate that the most exploited attack vector is Remote Desktop Protocol (RDP) which was used in 47% to 55% of ransomware attacks carried out during the recent years.
Other common vectors include email phishing, software vulnerabilities and account takeovers.
It’s More Than Just Exposed RDPs
The transition to remote work resulted in surge in the use of remote desktop applications.
The rush to enable business continuity during the lockdown has had a negative impact on cyber hygiene. Back in March, we reported a sharp increase in RDPs which were left exposed to the internet with little or no protection. As of now, these numbers have gone down but at this moment there are still over 4.5 million RDP services which are exposed to the web and can be exploited to carry out various attacks including ransomware attacks.
Exposed RDPs are indeed causing much damage to their respective organizations. However, they are not the problem but rather a clear symptom of a much larger issue – Shadow IT.
For years now, IT and security experts as well as research firms have been talking about the risks of Shadow IT, repeatedly declaring it to be the next looming cybersecurity threat.
Back in 2016, Gartner included Shadow IT as part of its top 10 security predictions and said that by 2020, a third of all successful attacks experienced by enterprises will be on their Shadow IT resources. Well, 2020 is almost over and when examining the leading casual events in various breaches and incidents it is safe to say that this prediction has indeed materialized.
In the past year alone, there were endless accounts published of various data leaks, breaches and other incidents resulting from misconfigured databases and cloud services, development tools with improper access control, unpatched VPNs, exposed RDPs etc.
Is All Shadow IT Equally Dangerous?
When trying to quantify and discover the extent of Shadow IT within an organization, there are two main questions that should be addressed by IT and security professionals:
- What are my known unknowns? What unknown assets and exposures might I have within my known network ranges (we call it the “official perimeter”) and what is the level of risks that they pose? Such known unknowns can include misconfigured systems, legacy servers, and expired certificates among others.
- What are my unknown unknowns? What unknown assets and exposures might I have beyond my known network ranges (we call it the “unofficial perimeter”) and what risks might be lurking there? These unknown unknowns often include unsanctioned cloud services, use of unauthorized hosting providers, unexpected IP addresses, assets managed by your vendors, etc.
The “unknown unknown” portion of the attack surface is large and varies greatly between different types of sizes of organizations. It can range between 30% and 95% of the exposed services of an organization.
The known unknowns are partially dealt with today by IT and security teams, via the use of
various asset tracking and network scanners that are deployed on the networks and detect such assets and vulnerabilities. However, the “unknown unknown” exposures and risks are simply untraceable through the commonly used solutions which focus on your known environments.
The chart below is based on an analysis of the attack surfaces of 18 leading organizations across 9 different industries and illustrates the distribution of exposed services between their official and unofficial network perimeters.
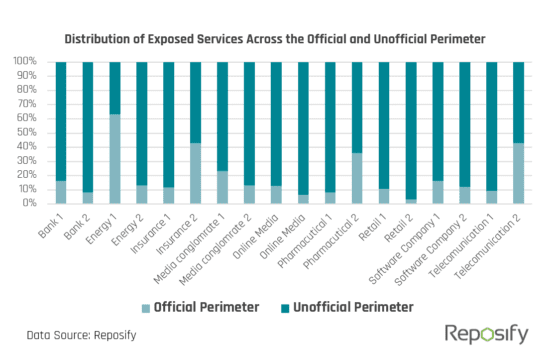
For all companies but one, the overwhelming majority of exposed services were part of their “Unofficial Perimeter” which is very likely to represent an unknown unknown.
These findings illustrate the extent to which organizations’ IT ecosystems extend beyond the firewall and team’s line of sight. How can teams fight shadow IT of which they are not even aware?
We Need a New Approach For Fighting Shadow IT
If we look reality in the eye, Shadow IT is inevitable. Performing awareness training, setting clear IT policies and improving IT service might help reduce the scope of this growing problem. However, as long as we are human, Shadow IT will continue to exist.
In addition, let’s not forget the positive aspects of shadow IT (yes, it’s not all bad).
Shadow IT often reflects a culture of innovation and a workforce which is geared towards productivity.
So, the question to be asked is, how do we embrace it, and reap the benefits of Shadow IT while eliminating the potential risks it poses to an organization?
By placing the right guardrails in place. I couldn’t agree more with the recommendation published by Gartner for dealing with Shadow IT – “Companies should find a way to track shadow IT, and create a culture of acceptance and protection versus detection and punishment.”
As IT and security professionals, we must extend our visibility and control beyond our known network ranges (“official perimeter”), so we can finally see the full picture of our shadow IT assets and related risks.
If we want to significantly reduce our chances of experiencing a breach or a ransomware attack this must be done in real time, so we can eliminate the critical risks and exposures before they can be discovered and exploited by attackers.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



