High-Tech Bridge has released its annual review of trends in web application security in 2013. The research results revealed data about vendors and vulnerabilities in 2013, with highlights including patch times cut by one-third compared to 2012.
Despite web application vendors being more responsive and releasing security patches much faster than in 2012, the research revealed that it is still taking an average of over two weeks for critical vulnerabilities to be fixed.
Many of the vendors notified of a vulnerability by High-Tech Bridge reacted within several hours and released a security patch in a couple of days. The vast majority of vendors alerted their end-users to the vulnerabilities High-Tech Bridge identified in a fair and rapid manner, but one vendor that put its end-users at risk by ignorance and negligence was Mijosoft.
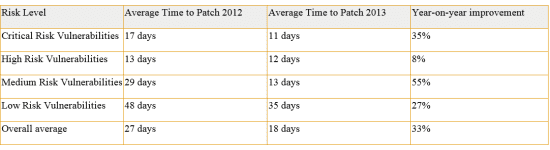
The table below details High-Tech Bridge’s comparison of average patch times in 2013 compared to 2012:
*Click image to enlarge*
Ilia Kolochenko, CEO, said: “11 days to patch critical vulnerabilities is still a fairly long delay. But, thankfully, even though serious vulnerabilities are becoming more complex to detect and exploit, there are vendors such as BigTree CMS who are responding to even complex vulnerabilities in less than three hours, so our award for the Most Responsive Vendor of the Year 2013 goes to that organisation.
General awareness within vendors about the importance of application security is also growing, with vendors finally taking security seriously. In the past, even well-known vendors postponed security-related fixes in favour of releasing new versions of their software with new functionality and unpatched vulnerabilities. However, in 2013, no big vendor adopted this dangerous approach of prioritizing functionality while sacrificing security and only three of the 62 security advisories released by us in 2013 remained unpatched.”
Despite better coding practices making serious vulnerabilities in mature apps harder to find, in its research, High-Tech Bridge also found a number of cases where excellent application security was compromised by basic mistakes such as failing to delete installation scripts, enabling cyber criminals to compromise the entire web application. This, Ilia Kolochenko believes, highlights the important of independent security testing and auditing of web applications, as even professional developers may simply miss or forget to control vital security points: “Critical and high risk vulnerabilities are becoming more sophisticated both to detect and to exploit. Gone are the days when many PHP applications commonly used “exec()” or “passthru()” functions with user-supplied input leading to remote code execution. Serious vulnerabilities are now exploitable via chained attacks and good examples that illustrate this are Remote Code Execution in Microweber and OS Command Injection in CosCms.
SQL injections vulnerabilities are also becoming more complex to exploit. A relatively complex, but efficient DNS exfiltration technique is now commonly used in cases that in the past were considered almost unexploitable to extract data from the database. It is also important to mention that many of the vulnerabilities usually deemed to be high or critical risk were downgraded to medium risk in our advisories in 2013, as their exploitation required the attacker to be authenticated or logged-in. This confirms that web developers should also pay attention to security for parts of the application accessible only to “trusted” parties who may in fact be quite hostile.”
Combining its security research with statistics from its ImmuniWeb® web application security testing SaaS and web application penetration testing , High-Tech Bridge ranked the most vulnerable web applications in the following order:
– In-house web application, at 40 per cent
– Plugins and modules for CMSs, at 30 per cent
– Small CMSs, at 25 per cent
– Large CMSs, such as WordPress and Joomla), at 5 per cent
XSS and SQLi were revealed as still being the most common weaknesses found and, in-house web applications, the most likely to be vulnerable to these types of attacks, with 55 per cent of vulnerabilities discovered by High-Tech Bridge Research in 2013 Cross-Site Scripting while, in second place, SQL injections made up 20 per cent of the total.
Marsel Nizamutdinov, Chief Research Officer at High-Tech Bridge, concluded: “It is important to say that about 90 per cent of large and medium-size commercial and open-source CMSs prone to XSS and SQL injection attacks are vulnerable because they are not up-to-date or are incorrectly configured. However, we have made great progress in terms of positive impact our research brings to the industry, with tens of thousands of popular websites no longer at risk of compromised thanks to our efforts and collaboration with software vendors.
“Our security advisory format developed together with OSVDB is now being used by other security researchers as a standard. As we can see, vulnerabilities are becoming harder to detect and exploit. Common approaches to security testing such as automated vulnerability scanning or automated source code review are no longer sufficient. At High-Tech Bridge we see the future of web application security in hybrid testing when automated testing is combined with manual security testing by a human. We implemented a hybrid approach in our SaaS called ImmuniWeb®that can detect such complex vulnerabilities missed by automated solutions.”
High-Tech Bridge
![]() High-Tech Bridge SA is a leading provider of information security services, such as penetration testing, network security auditing, consulting and computer crime forensics. In 2012 Frost & Sullivan recognised High-Tech Bridge as one of the market leaders and best service providers in the ethical hacking industry. High-Tech Bridge devotes significant resources to information security research. High-Tech Bridge Security Research Lab has helped software vendors to improve security of their products, including such vendors as Microsoft, IBM, Novell, McAfee, Sony, HP, Samsung, OpenOffice, Corel, OpenX, Joomla, WordPress, UMI.CMS, and hundreds of others.
High-Tech Bridge SA is a leading provider of information security services, such as penetration testing, network security auditing, consulting and computer crime forensics. In 2012 Frost & Sullivan recognised High-Tech Bridge as one of the market leaders and best service providers in the ethical hacking industry. High-Tech Bridge devotes significant resources to information security research. High-Tech Bridge Security Research Lab has helped software vendors to improve security of their products, including such vendors as Microsoft, IBM, Novell, McAfee, Sony, HP, Samsung, OpenOffice, Corel, OpenX, Joomla, WordPress, UMI.CMS, and hundreds of others.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.